Refer to the exhibit.
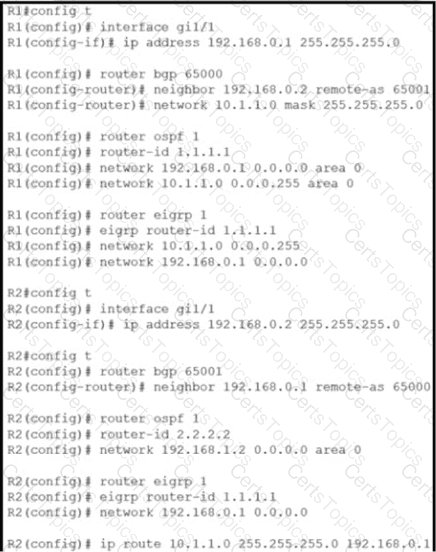
Router R2 is configured with multiple routes to reach network 10 1.1 0/24 from router R1. What protocol is chosen by router R2 to reach the destination network 10.1 1 0/24?
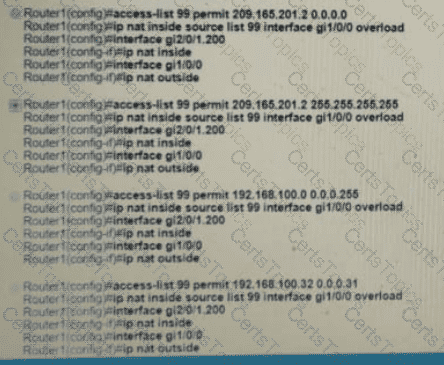
Refer to Exhibit.
Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN 100 to use their own IP addresses?
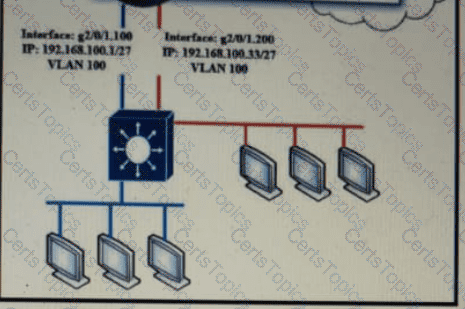
Refer to the exhibit.
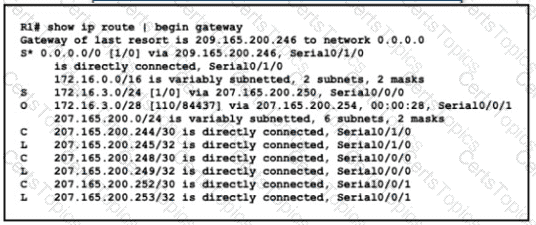
A packet is being sent across router R1 to host 172.163.3.14. To which destination does the router send the packet?
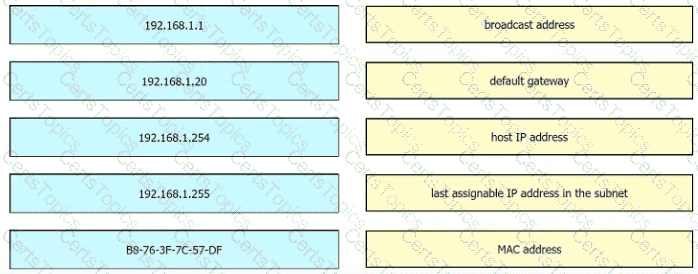
Refer to the exhibit.
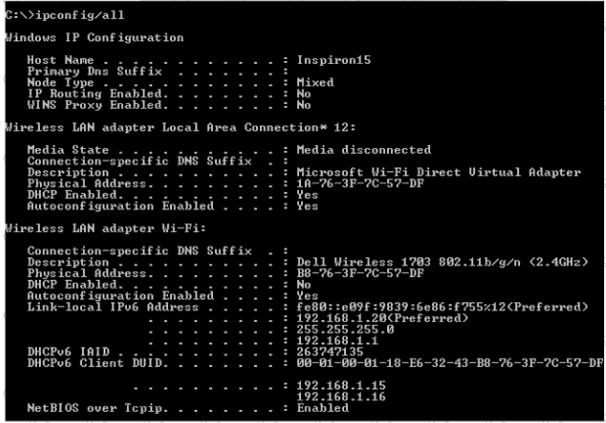
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.