Which device tracks the state of active connections in order to make a decision to forward a packet through?
Which protocol does an IPv4 host use to obtain a dynamically assigned IP address?
Refer to the exhibit.
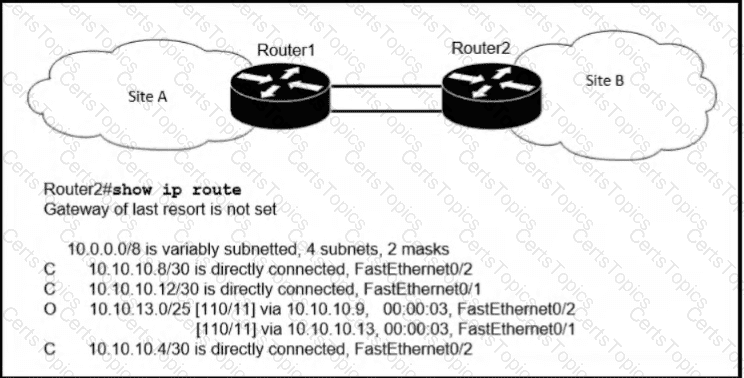
If OSPF Is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?