Refer to the exhibit.
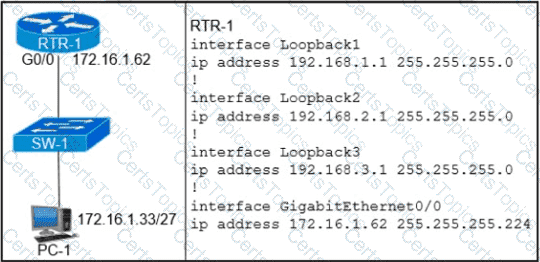
Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
Which two functions are performed by the core layer in a three-tier architecture? (Choose two)
Which command on a port enters the forwarding state immediately when a PC is connected to it?
What does physical access control regulate?