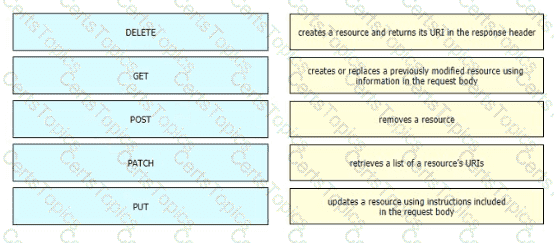
Drag and drop the HTTP methods used with REST-Based APIs from the left onto the descriptions on the right.
Which two capabilities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two.)
What provides connection redundancy increased bandwidth and load sharing between a wireless LAN controller and a Layer 2 switch?
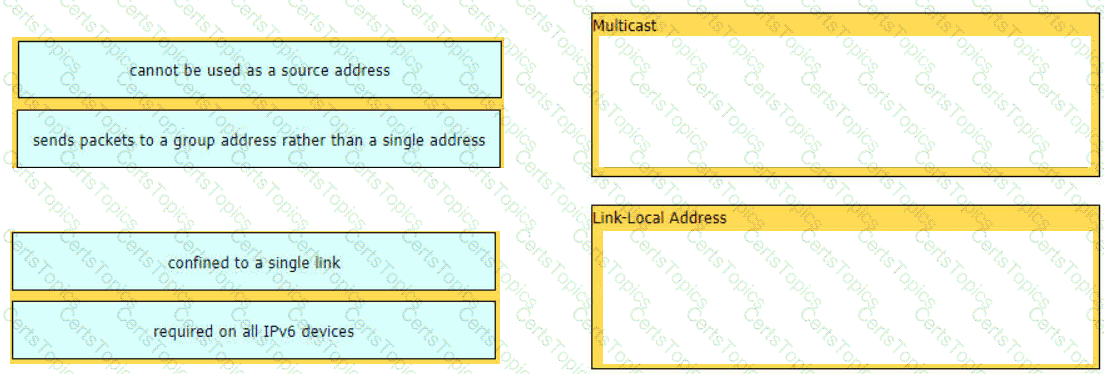
Drag and drop the characteristic from the left onto the IPv6 address type on the right.