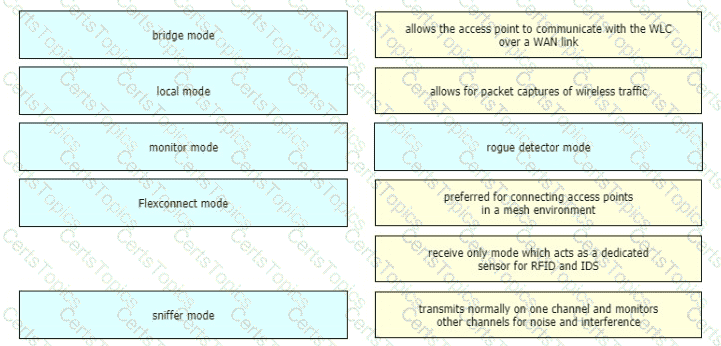
Drag and drop the lightweight access point operation modes from the left onto the descriptions on the right
An engineer must establish a trunk link between two switches. The neighboring switch is set to trunk or desirable mode. What action should be taken?
A router running EIGRP has learned the same route from two different paths. Which parameter does the router use to select the best path?
Which unified access point mode continues to serve wireless clients after losing connectivity to the Cisco Wireless LAN Controller?