When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
Refer to Exhibit.
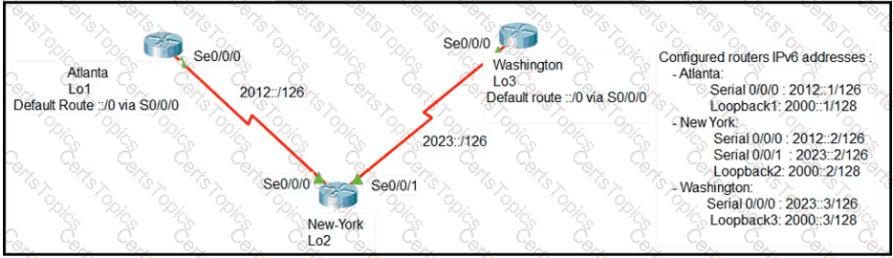
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the NEW York router? (Choose two)
What causes a port to be placed in the err-disabled state?
Which WAN access technology is preferred for a small office / home office architecture?