Refer to the exhibit.
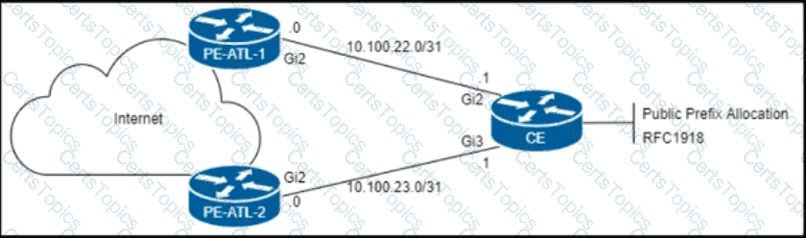
The CE router is peering with both PE routers and advertising a public prefix to the internet. Routing to and from this prefix will be asymmetric under certain network conditions, but packets must not be discarded. Which configuration must an engineer apply to the two PE routers so that they validate reverse packet forwarding for packets entering their Gi2 interfaces and drop traffic from the RFC1918 space?
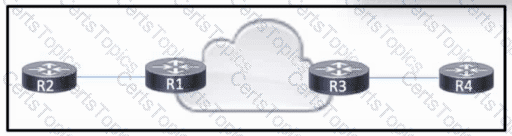
Refer to the exhibit. R1 and R3 have a pseudowire connection between them, which allows R2 and R4 to communicate via Layer 2. R2 uses VLAN 10. R4 also uses VLAN 10, but with a different subnet associated.
Which configuration should the engineer apply to R3 to rewrite the VLAN on traffic from R2 to VLAN 15?
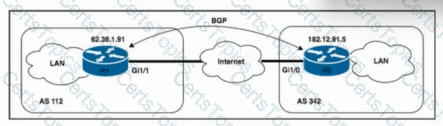
Refer to the exhibit. Routers R1 and R2 are connected over the internet, with the connection passing over four different autonomous systems. The company must mitigate potential DDoS attacks and protect the CPUs of the routers. A network engineer must secure all external connections on edge router R1 based on RFC 5082. R2 has already been secured. Which task should the engineer perform on R1 to achieve the goal?
Under which circumstance does BGP ignore the best-path algorithm after receiving multiple routes to a destination?