A security analyst is reviewing a SIEM and generates the following report:
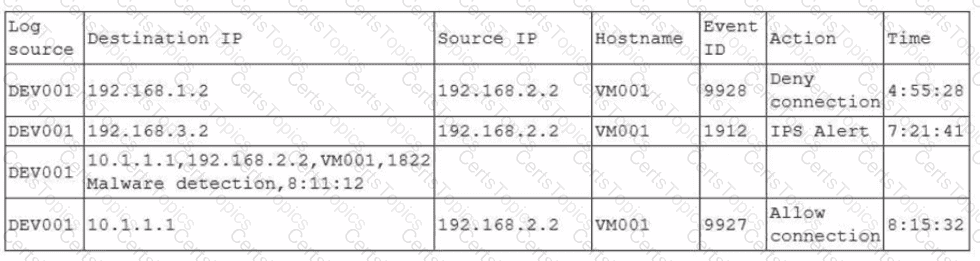
Later, the incident response team notices an attack was executed on the VM001 host. Which of the following should the security analyst do to enhance the alerting process on the SIEM platform?
A company wants to perform threat modeling on an internally developed, business-critical application. The Chief Information Security Officer (CISO) is most concerned that the application should maintain 99.999% availability and authorized users should only be able to gain access to data they are explicitly authorized to view. Which of the following threat-modeling frameworks directly addresses the CISO's concerns about this system?
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With
issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure
authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase
character, one numeric character, and one special character, and it must
meet a minimumlength requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration.
Fill in the appropriate fields and make selections from the drop-down menus.
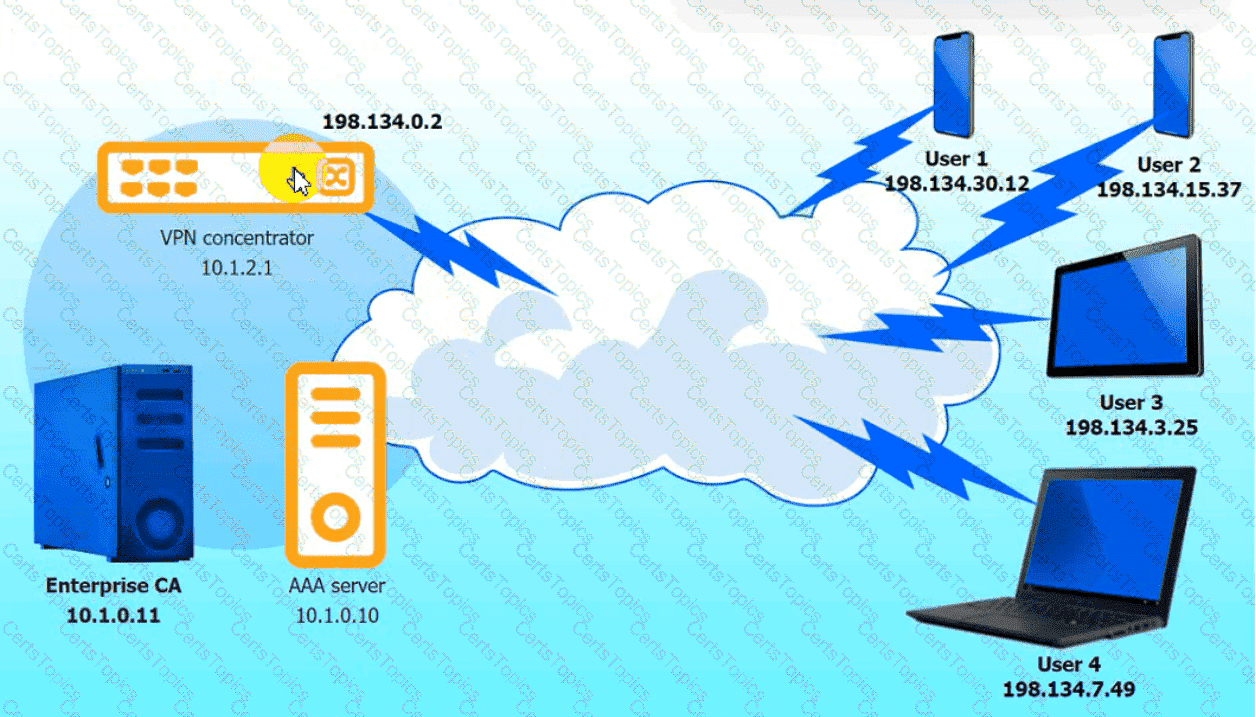
VPN Concentrator:
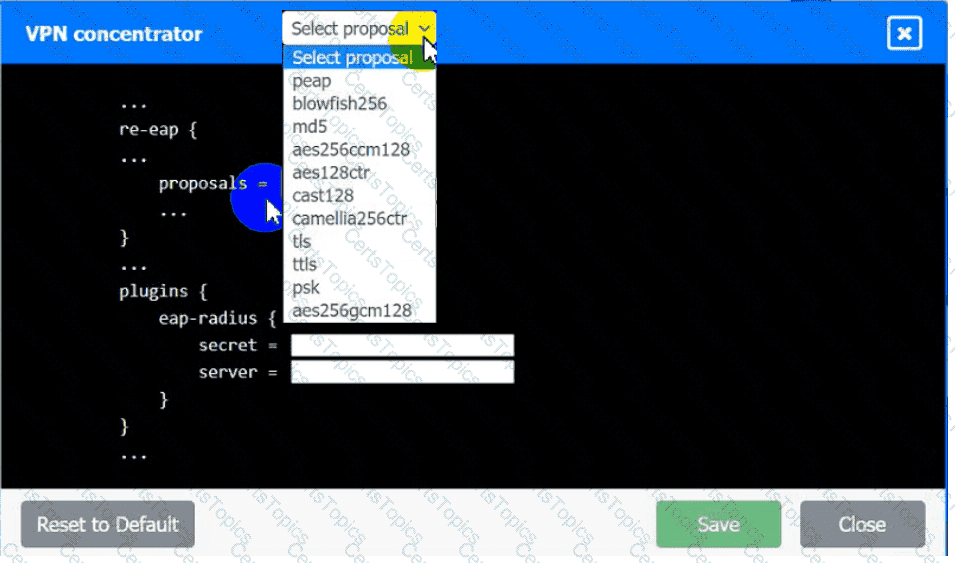
AAA Server:

A cloud engineer needs to identify appropriate solutions to:
• Provide secure access to internal and external cloud resources.
• Eliminate split-tunnel traffic flows.
•Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).