A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
A security architect is troubleshooting an issue with an OIDC implementation. The architect reviews the following configuration and errors:
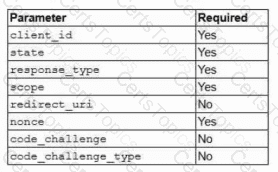
Error: Invalid authentication request code
Which of the following is the most likely cause of the error?
A security administrator is performing a gap assessment against a specific OS benchmark The benchmark requires the following configurations be applied to endpoints:
• Full disk encryption
* Host-based firewall
• Time synchronization
* Password policies
• Application allow listing
* Zero Trust application access
Which of the following solutions best addresses the requirements? (Select two).
PKI can be used to support security requirements in the change management process. Which of the following capabilities does PKI provide for messages?