An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice. Which of the following should the organization consider first to address this requirement?
A company finds logs with modified time stamps when compared to other systems. The security team decides to improve logging and auditing for incident response. Which of the following should the team do to best accomplish this goal?
Company A and Company D ate merging Company A's compliance reports indicate branchprotections are not in place A security analyst needs to ensure that potential threats to the software development life cycle are addressed. Which of the following should me analyst cons
A security analyst isreviewing the following event timeline from an COR solution:
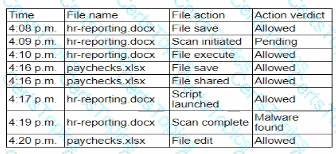
Which of the following most likely has occurred and needs to be fixed?