A web application server that provides services to hybrid modern and legacy financial applications recently underwent a scheduled upgrade to update common libraries, including OpenSSL. Multiple users are now reporting failed connection attempts to the server. The technician performing initial triage identified the following:
• Client applications more than five years old appear to be the most affected.
• Web server logs show initial connection attempts by affected hosts.
• For the failed connections, logs indicate "cipher unavailable."
Which of the following is most likely to safely remediate this situation?
Users must accept the terms presented in a captive petal when connecting to a guest network. Recently, users have reported that they are unable to access the Internet after joining the network A network engineer observes the following:
• Users should be redirected to the captive portal.
• The Motive portal runs Tl. S 1 2
• Newer browser versions encounter security errors that cannot be bypassed
• Certain websites cause unexpected re directs
Which of the following mow likely explains this behavior?
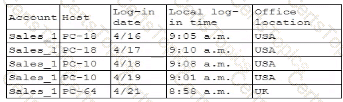
Which of the following is the security engineer most likely doing?
A company recentlyexperienced aransomware attack. Although the company performssystems and data backupon a schedule that aligns with itsRPO (Recovery Point Objective) requirements, thebackup administratorcould not recovercritical systems and datafrom its offline backups to meet the RPO. Eventually, the systems and data were restored with information that wassix months outside of RPO requirements.
Which of the following actions should the company take to reduce the risk of a similar attack?