A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not normally send traffic to those sites. The technician will define this threat as:
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
During an incident response activity, the response team collected some artifacts from a compromised server, but the following information is missing:
• Source of the malicious files
• Initial attack vector
• Lateral movement activities
The next step in the playbook is to reconstruct a timeline. Which of the following best supports this effort?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:
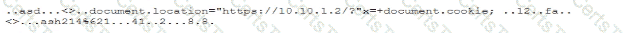
Which of the following best describes this incident?