An organization recently implemented a policy that requires all passwords to be rotated every 90 days. An administrator observes a large volume of failed sign-on logs from multiple servers that are often accessed by users. The administrator determines users are disconnecting from the RDP session but not logging off. Which of the following should the administrator do to prevent account lockouts?
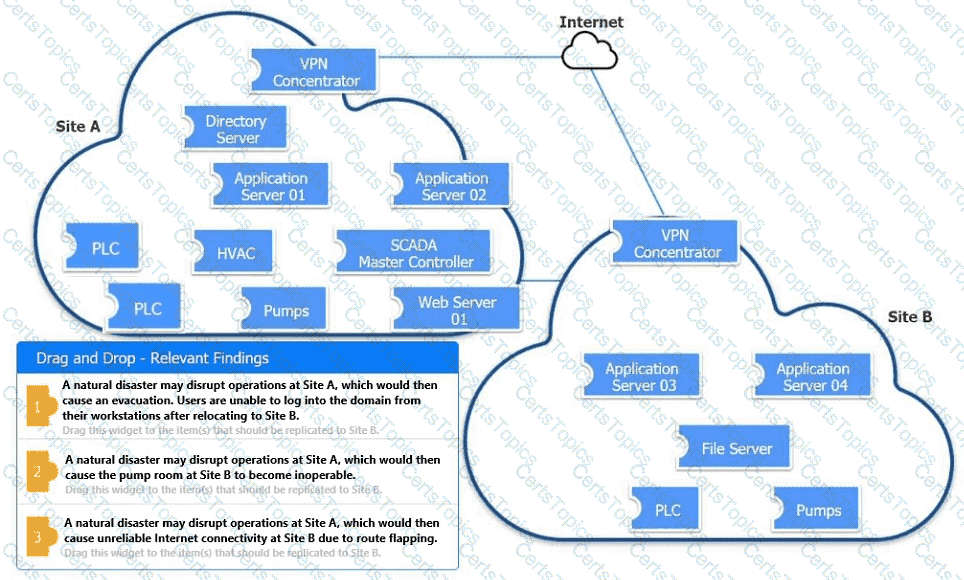
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
An organization is looking for gaps in its detection capabilities based on the APTs that may target the industry Which of the following should the security analyst use to perform threatmodeling?
A company developed a new solution that needs to track any changes to the data, and the changes need to be quickly identified. If any changes are attempted without prior approval, multiple events must be triggered, such as:
Raising alerts
Blocking the unapproved changes
Quickly removing access to the data
Which of the following solutions best meets these requirements?