Refer to the exhibit.
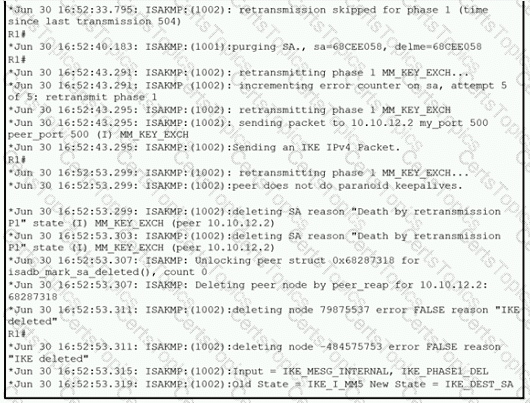
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
Which statement about IOS zone-based firewalls is true?
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?