Refer to the exhibit.
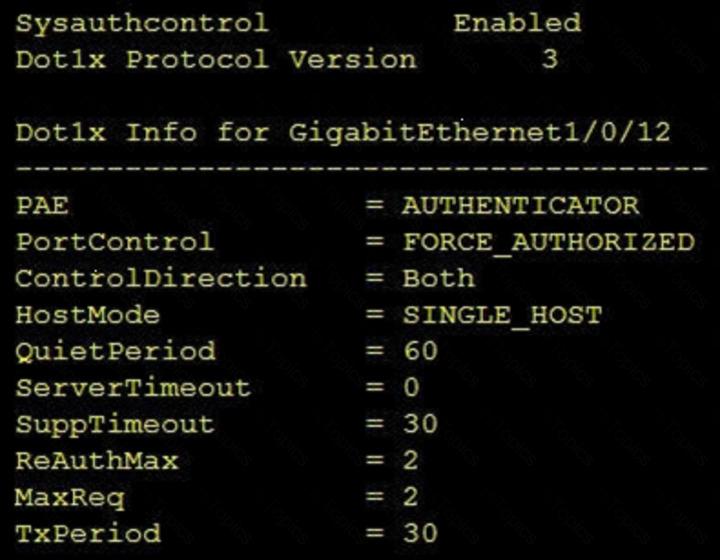
Which command was used to display this output?
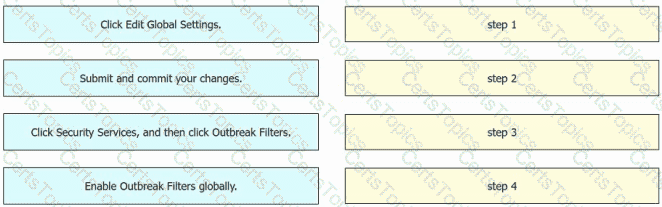
An engineer must enable Outbreak Filters globally on an AsyncOS for Cisco Secure Email Gateway to protect the network from large-scale malware attacks. Drag and drop the steps from the left into the sequence on the right to complete the configuration.
A web hosting company must upgrade its older, unsupported on-premises servers. The company wants a cloud solution in which the cloud provider is responsible for:
Server patching
Application maintenance
Data center security
Disaster recovery
Which type of cloud meets the requirements?
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)