An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA
command must be used?
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
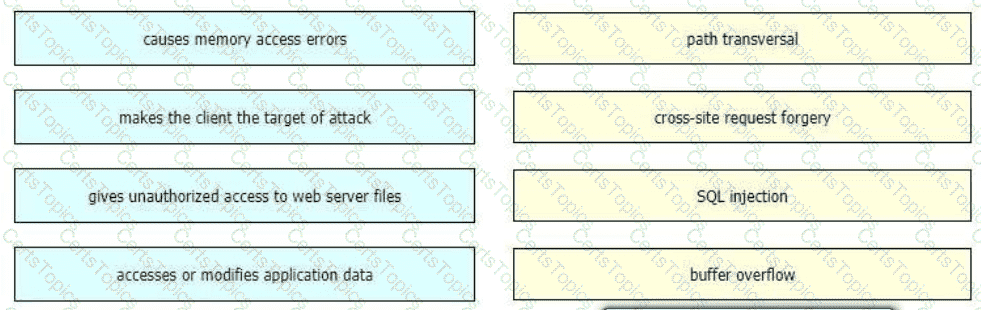
Drag and drop the exploits from the left onto the type of security vulnerability on the right.
An engineer needs to configure an access control policy rule to always send traffic for inspection without
using the default action. Which action should be configured for this rule?