Which Cisco AMP file disposition valid?
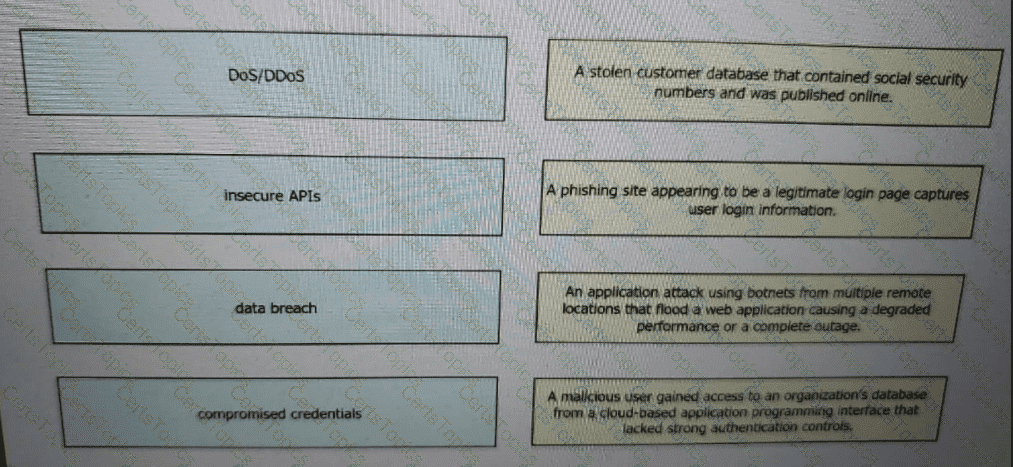
Drag and drop the threats from the left onto examples of that threat on the right
Which attribute has the ability to change during the RADIUS CoA?
Which two methods are available in Cisco Secure Web Appliance to process client requests when configured in Transparent mode? (Choose two.)