AAA stands for Authentication, Authorization, and Accounting. It is a framework that provides security to network resources by controlling who can access them (authentication), what they can do (authorization), and what actions they perform (accounting). AAA can be implemented by using the local database of the device or by using an external server such as Cisco ISE (Identity Services Engine).
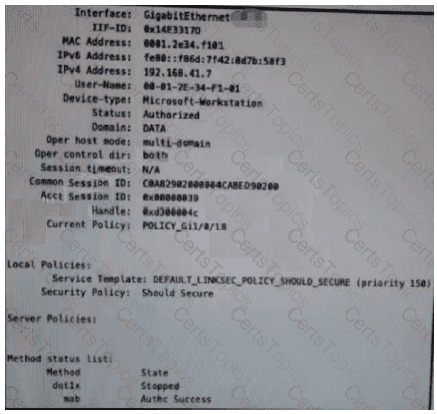
The question asks which configuration item makes it possible to have the AAA session on the network. A session is a logical connection between a user and a network device. A session can be initiated by various methods, such as console, telnet, SSH, PPP, etc. Each session can have different AAA policies applied to it, depending on the method list configured for that session.
A method list is a set of rules that define the authentication, authorization, and accounting methods to be used for a particular session. A method list can be named or default. A named method list is applied to a specific session by using the login, authorization, or accounting keyword followed by the name of the method list. A default method list is applied to all sessions that do not have a named method list configured.
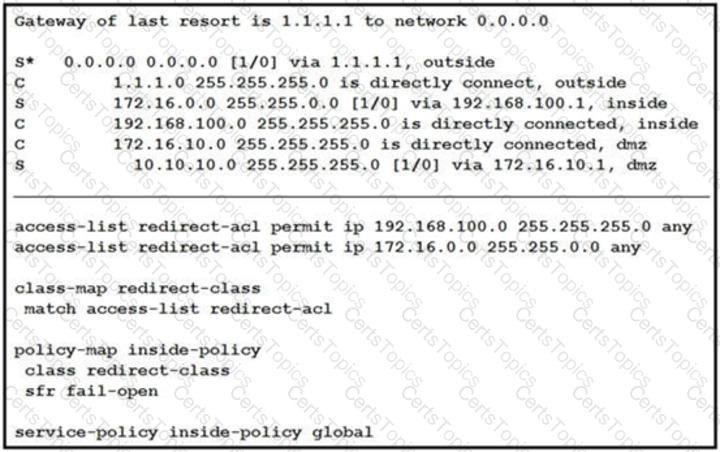
The configuration item that makes it possible to have the AAA session on the network is the aaa authorization network default group ise command. This command configures a default method list for network authorization, which is the process of determining the network services and attributes that a user is allowed to access after authentication. The command specifies that the network authorization method is group, which means that the device will use an external server (such as Cisco ISE) to obtain the authorization information for the user. The command also specifies that the name of the server group is ise, which means that the device will use the server group defined by the aaa group server radius ise command.
The other options are incorrect because they do not configure a default method list for network authorization. Option A configures a named method list for login authentication, which is the process of verifying the identity of the user. Option B configures a default method list for enable authentication, which is the process of verifying the identity of the user who wants to enter the privileged EXEC mode. Option D configures a default method list for exec authorization, which is the process of determining the commands and features that a user can access in the EXEC mode. References:
Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0, Module 1: Security Concepts, Lesson 1: Describing Information Security Concepts
Configure Basic AAA on an Access Server, General AAA Configuration, Authentication Configuration, Authorization Configuration
AAA (Authentication, Authorization and Accounting) - GeeksforGeeks, AAA implementation, ACS server