Refer to the exhibit.
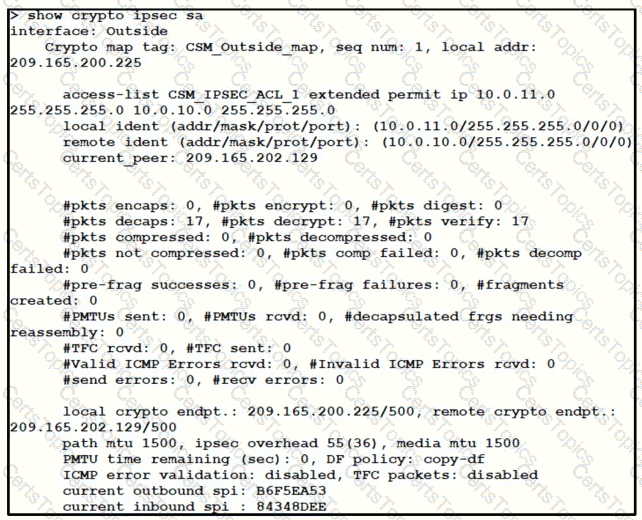
Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance. What is causing this issue?
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls?
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
What is an advantage of network telemetry over SNMP pulls?