Which type of dashboard does Cisco DNA Center provide for complete control of the network?
How does DNS Tunneling exfiltrate data?
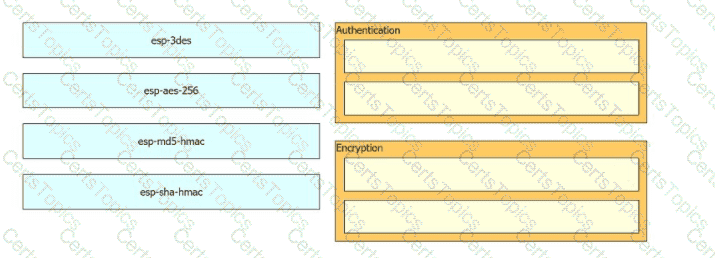
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?