A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
• Obtain sensitive data and export the data out of the network.
• Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
In the wake of a security compromise incident where the internal networks were breached by an outside attacker at the perimeter of the infrastructure, an enterprise is now evaluating potential measures that can help protect against the same type of incident in the future. What are two design options that can be employed? (Choose two)
A network design includes a long signaling delay in notifying the Layer 3 control plane that an interface has failed Which two of these actions would reduce that delay? (Choose two.)
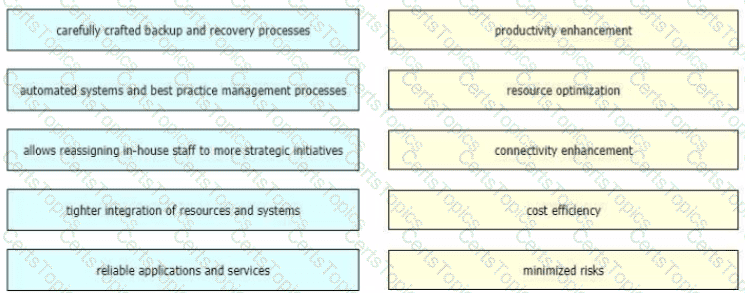
As technologies such as big data, cloud, and loT continue to grow, so will the demand for network bandwidth Business strategies must be flexible to accommodate these changes when it comes to priorities and direction and the network design strategy also must be agile and adaptable Drag and drop the benefits from the left onto the corresponding strategic approaches on the right as they relate to network design and management.