Refer to the exhibit.
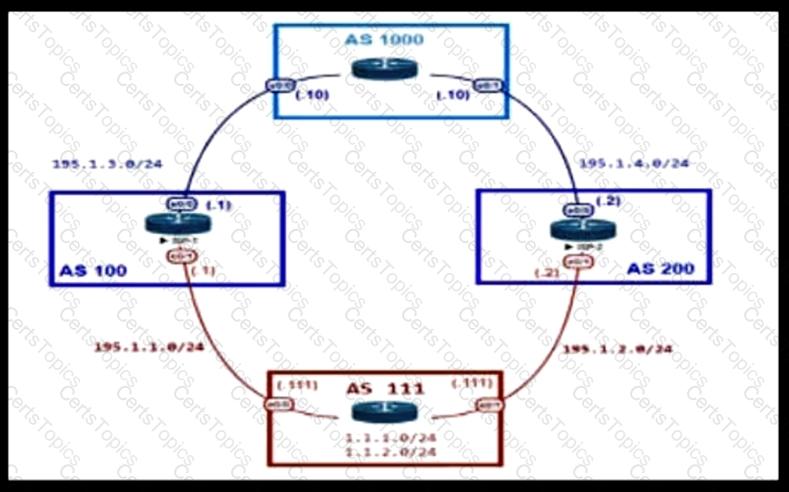
An engineer is designing the network for a multihomed customer running in AS 111. The AS does not have any other ASs connected to it. Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
Which feature is supported by NETCONF but is not supported by SNMP?
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?