As part of a new network design documentation, you are required to explain the reason for choosing Cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network? (Choose two)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Refer to the diagram.
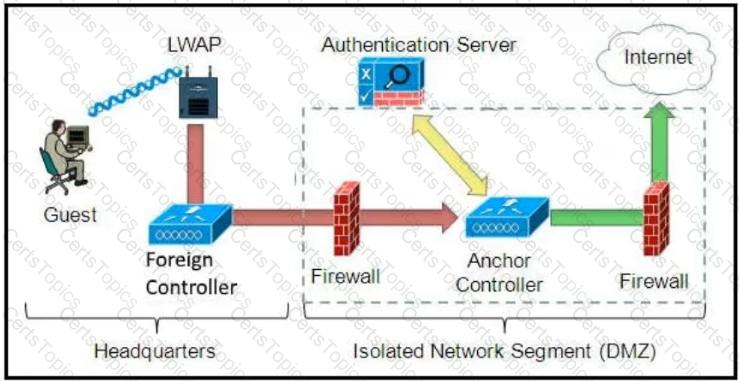
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
An external edge router provides connectivity from a service provider to an enterprise. Which two Internet edge best practices meet compliance regulations? (Choose two)