Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
Refer to the exhibit.
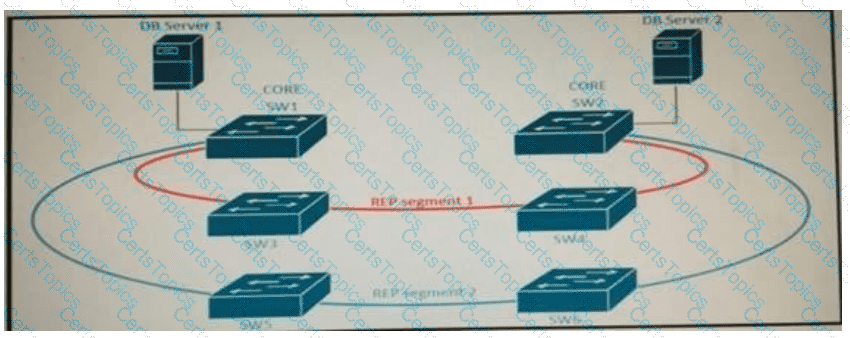
Refer to the exhibit. A new high availability DB server cluster is installed in the network. These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?