A service provider recently migrated to an SD-WAN solution for delivering WAN connections to its customers. One of the main challenges with the SD-WAN deployment is that branch site volume increases every year, which causes management complexity. Which action resolves the issue?
Retef to the exhibit.
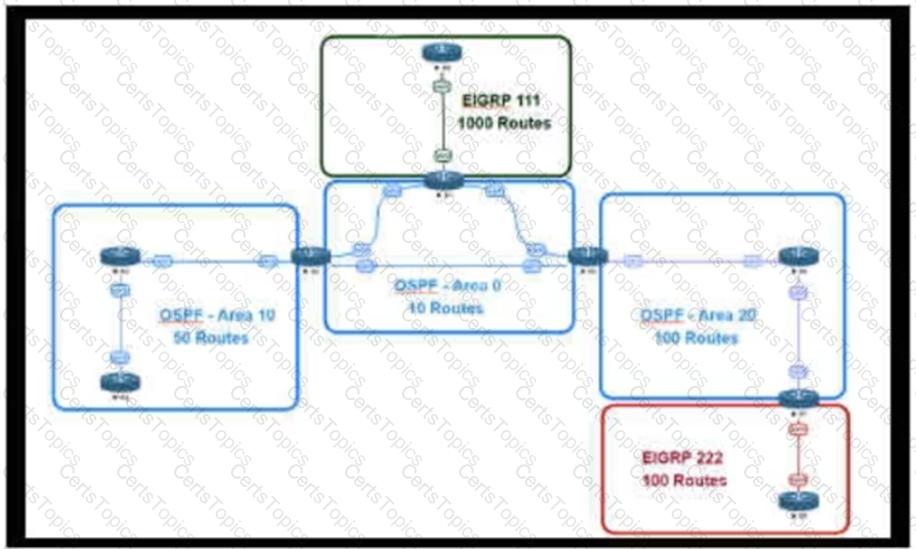
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain. EIGRP routes are getting redistributed into OSPF. OSPF area 20 has routers with limited memory and CPU resources. The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to flow in. Which OSPF area type fulfills this design requirement?
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two.)
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?