Refer to the exhibit.
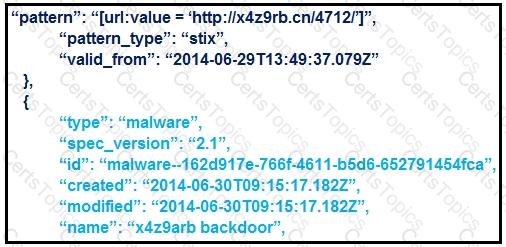
What is the IOC threat and URL in this STIX JSON snippet?
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?


Refer to the exhibit.
What is occurring?
An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?