An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
Which information is provided about the object file by the “-h” option in the objdump line commandobjdump –b oasys –m vax –h fu.o?
Refer to the exhibit.
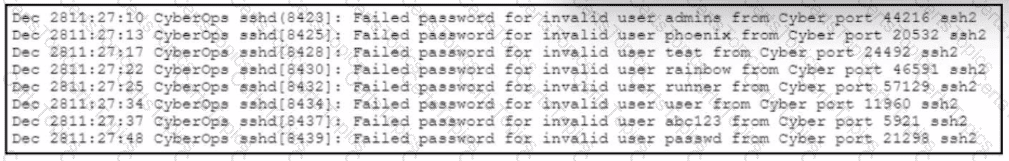
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities. Which attack vector is used and what mitigation can the analyst suggest?
Refer to the exhibit.
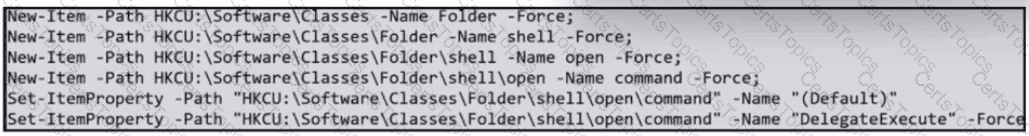
What does the exhibit indicate?