Cisco Related Exams
300-215 Exam







An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team’s approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?
What describes the first step in performing a forensic analysis of infrastructure network devices?
Refer to the exhibit.
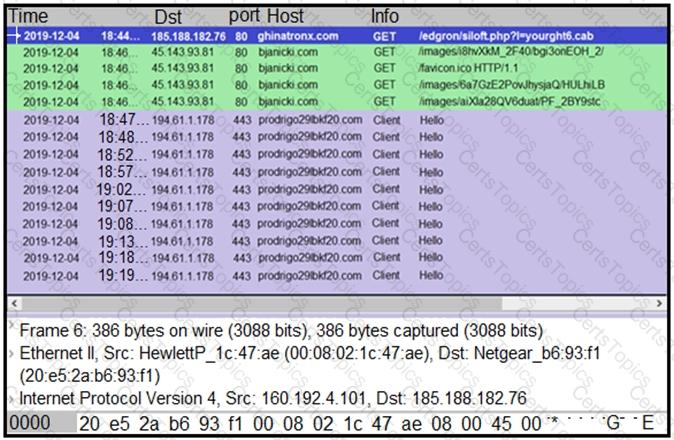
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?