Refer to the exhibit.
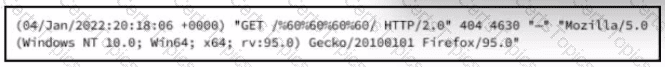
What is occurring?
Refer to the exhibit.
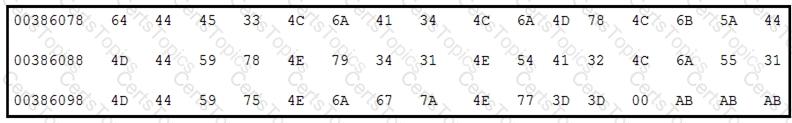
Which encoding technique is represented by this HEX string?
Refer to the exhibit.
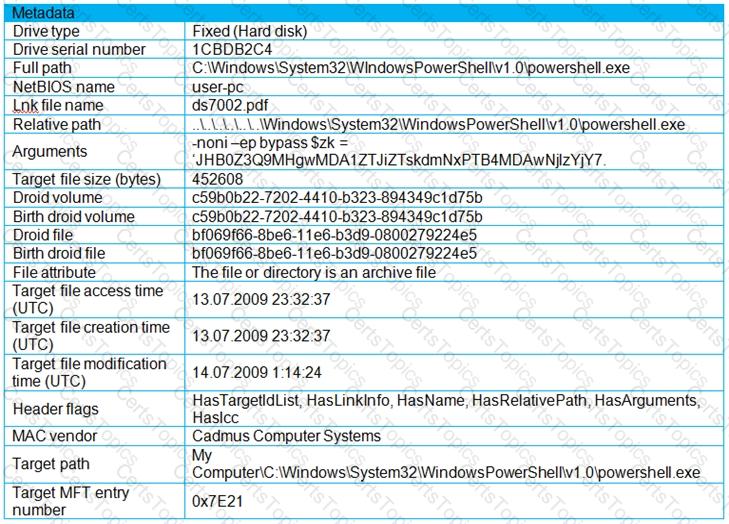
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?