Refer to the exhibit.
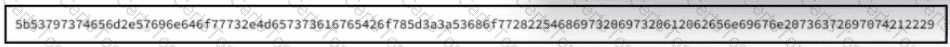
Refer to the exhibit.
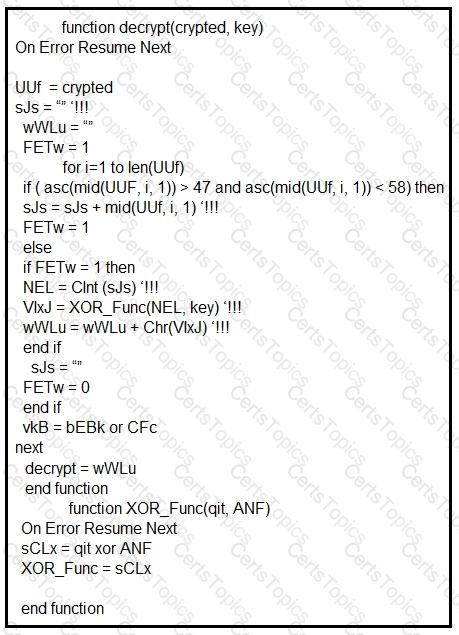
Which type of code created the snippet?
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
Which type of record enables forensics analysts to identify fileless malware on Windows machines?