Refer to the exhibit.
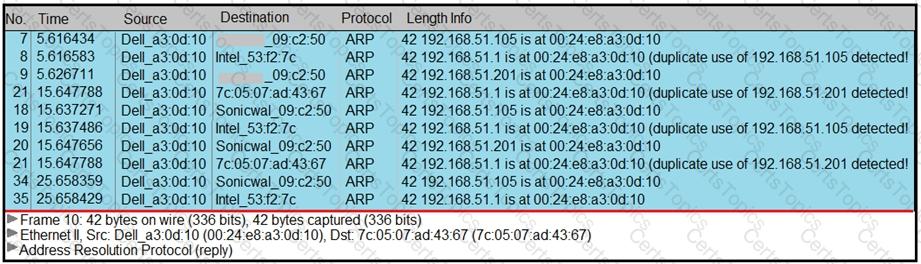
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
A cybersecurity analyst is analyzing a complex set of threat intelligence data from internal and external sources. Among the data, they discover a series of indicators, including patterns of unusual network traffic, a sudden increase in failed login attempts, and multiple instances of suspicious file access on the company's internal servers. Additionally, an external threat feed highlights that threat actors are actively targeting organizations in the same industry using ransomware. Which action should the analyst recommend?
Refer to the exhibit.

An engineer received a ticket to analyze a recent breach on a company blog. Every time users visit the blog, they are greeted with a message box. The blog allows users to register, log in, create, and provide comments on various topics. Due to the legacy build of the application, it stores user information in the outdated MySQL database. What is the recommended action that an engineer should take?