Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Which information must an organization use to understand the threats currently targeting the organization?
Syslog collecting software is installed on the server For the log containment, a disk with FAT type partition is used An engineer determined that log files are being corrupted when the 4 GB tile size is exceeded. Which action resolves the issue?
What does an attacker use to determine which network ports are listening on a potential target device?
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
Which security principle requires more than one person is required to perform a critical task?
What is a difference between a threat and a risk?
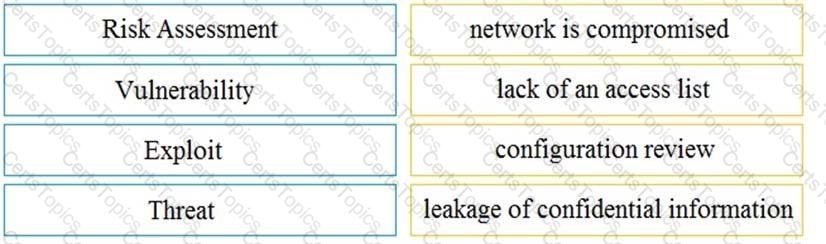
Drag and drop the uses on the left onto the type of security system on the right.
Refer to the exhibit.
What is depicted in the exhibit?
What is the difference between the ACK flag and the RST flag?
How is NetFlow different from traffic mirroring?
What is the difference between a threat and a risk?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
Exhibit.
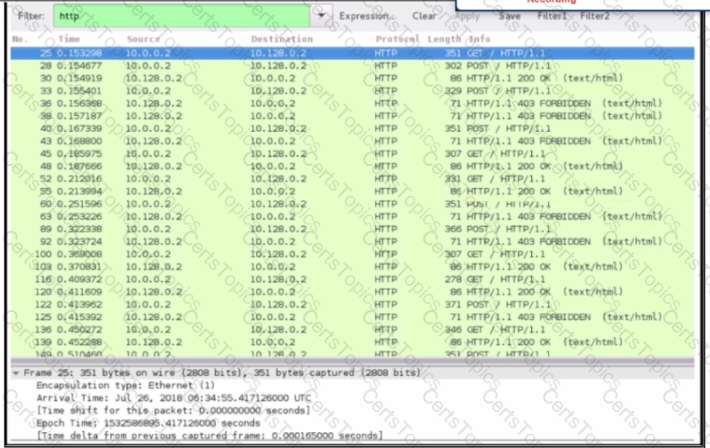
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)
Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
What makes HTTPS traffic difficult to monitor?
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
Which component results from this operation?
Refer to the exhibit.
Which application protocol is in this PCAP file?
Refer to the exhibit.
Which application protocol is in this PCAP file?
Refer to the exhibit.
An engineer received an event log file to review. Which technology generated the log?
Drag and drop the security concept on the left onto the example of that concept on the right.
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
What is a purpose of a vulnerability management framework?
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
Which security monitoring data type requires the largest storage space?
Drag and drop the data source from the left onto the data type on the right.
What is the difference between deep packet inspection and stateful inspection?
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load What is the next step the engineer should take to investigate this resource usage7
How does an attack surface differ from an attack vector?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
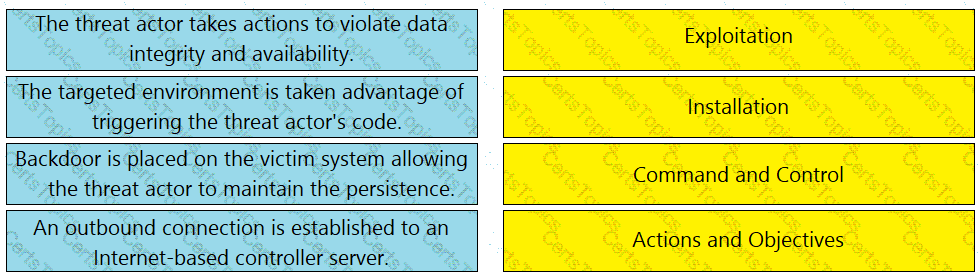
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
What is personally identifiable information that must be safeguarded from unauthorized access?
Refer to the exhibit.
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
Refer to the exhibit.
Which event is occurring?
Refer to the exhibit.
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Refer to the exhibit.
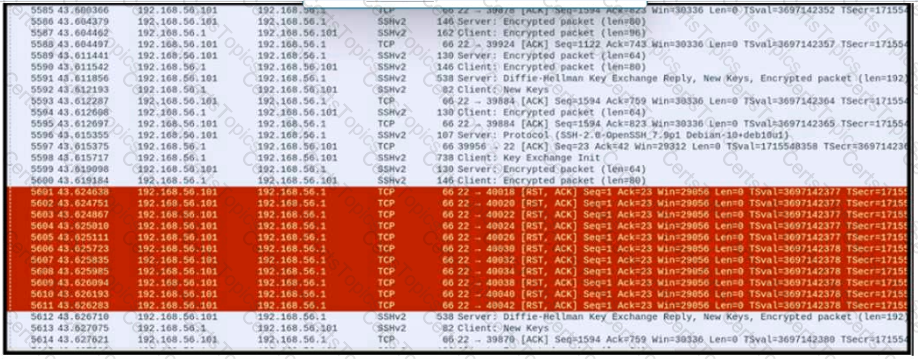
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
Refer to the exhibit.
Which kind of attack method is depicted in this string?
Which event is user interaction?
Refer to the exhibit.
What does the message indicate?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data. The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Refer to the exhibit.
Which stakeholders must be involved when a company workstation is compromised?
Refer to the exhibit.
What should be interpreted from this packet capture?
What is a difference between SOAR and SIEM?
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Refer to the exhibit.
What is occurring within the exhibit?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology should be used to accomplish the task?
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
An engineer must configure network systems to detect command-and-control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology must be used to accomplish this task?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit.
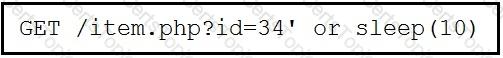
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
Which tool provides a full packet capture from network traffic?
Which incidence response step includes identifying all hosts affected by an attack?
What describes a buffer overflow attack?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
Which attack method intercepts traffic on a switched network?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
Which vulnerability type is used to read, write, or erase information from a database?
What describes the impact of false-positive alerts compared to false-negative alerts?
Refer to the exhibit.
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
Refer to the exhibit.
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded what would have occurred with stronger data visibility.
How can TOR impact data visibility inside an organization?
What ate two categories of DDoS attacks? (Choose two.)
What is the impact of encryption?
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
What are the two characteristics of the full packet captures? (Choose two.)
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
Which type of data collection requires the largest amount of storage space?
Which element is included in an incident response plan as stated m NIST SP800-617
How does agentless monitoring differ from agent-based monitoring?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.

What is the purpose of command and control for network-aware malware?
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Which regex matches only on all lowercase letters?
Which items is an end-point application greylist used?
STION NO: 102
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
What is data encapsulation?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
What is a comparison between rule-based and statistical detection?
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
Refer to the exhibit.
What must be interpreted from this packet capture?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)