Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
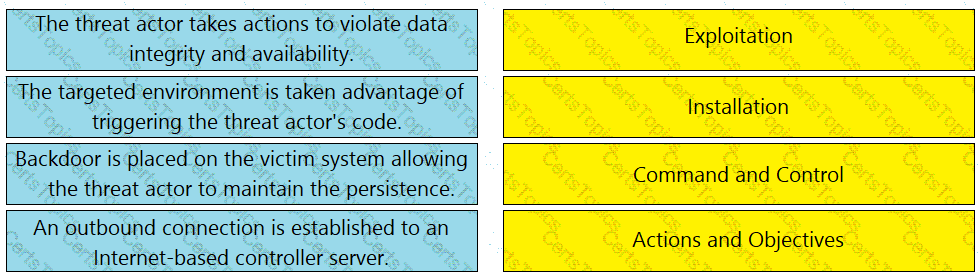
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
What is personally identifiable information that must be safeguarded from unauthorized access?