A new network is being created to support 126 users. Which of the following CIDR ranges provides the most efficient use of space?
A network engineer is configuring network ports in a public office. To increase security, the engineer wants the ports to allow network connections only after authentication. Which of the following security features should the engineer use?
Which of the following is used to stage copies of a website closer to geographically dispersed users?
A network engineer performed a migration to a new mail server. The engineer changed the MX record, verified the change was accurate, and confirmed the new mail server was reachable via the IP address in the A record. However, users are not receiving email. Which of the following should the engineer have done to prevent the issue from occurring?
Users are reporting issues with mobile phone connectivity after a cellular repeater was recently installed. Users also note that the phones are rapidly losing battery charge. Which of the following should the technician check first to troubleshoot the issue?
A network administrator is configuring access points for installation in a dense environment where coverage is often overlapping. Which of the following channel widths should the administrator choose to help minimize interference in the 2.4GHz spectrum?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
A network administrator deploys new network hardware. While configuring the network monitoring server, the server could authenticate but could not determine the specific status of the hardware. Which of the following would the administrator most likely do to resolve the issue?
A network administrator deployed wireless networking in the office area. When users visit the outdoor patio and try to download emails with large attachments or stream training videos, they notice buffering issues. Which of the following is the most likely cause?
An IT manager needs to connect ten sites in a mesh network. Each needs to be secured with reduced provisioning time. Which of the following technologies will best meet this requirement?
A network security administrator needs to monitor the contents of data sent between a secure network and the rest of the company. Which of the following monitoring methods will accomplish this task?
A network administrator is planning to host a company application in the cloud, making the application available for all internal and third-party users. Which of the following concepts describes this arrangement?
A detective is investigating an identity theft case in which the target had an RFID-protected payment card issued and compromised in the same day. The only place the target claims to have used the card was at a local convenience store. The detective notices a video camera at the store is placed in such a way that customers' credentials can be seen when they pay. Which of the following best explains this social engineering technique?
Which of the following is most likely responsible for the security and handling of personal data in Europe?
A network engineer needs to change, update, and control APs remotely, with real-time visibility over HTTPS. Which of the following will best allow these actions?
A network administrator's device is experiencing severe Wi-Fi interference within the corporate headquarters causing the device to constantly drop off the network. Which of the following is most likely the cause of the issue?
A network engineer runs ipconfig and notices that the default gateway is 0.0.0.0. Which of the following address types is in use?
Which of the following network cables involves bounding light off of protective cladding?
Which of the following is the step that a troubleshooter should take immediately after implementing a solution?
A network administrator needs to monitor data from recently installed firewalls in multiple locations. Which of the following solutions would best meet the administrator's needs?
A network analyst is installing a wireless network in a corporate environment. Employees are required to use their domain identities and credentials to authenticate and connect to the WLAN. Which of the following actions should the analyst perform on the AP to fulfill the requirements?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host’s TCP/IP stack first. Which of the following commands should the network administrator run?
A network administrator notices uncommon communication between VMs on ephemeral ports on the same subnet. The administrator is concerned about that traffic moving laterally within the network. Which of the following describes the type of traffic flow the administrator is analyzing?
Which of the following allows a network administrator to analyze attacks coming from the internet without affecting latency?
During a VoIP call, a user notices inconsistent audio and logs an incident ticket. A network administrator notices inconsistent delays in arrival of the RTP packets. Which of the following troubleshooting tools should the network administrator use to determine the issue?
Which of the following involves an attacker traversing from one part of a network to another part that should be inaccessible?
A network engineer connects a business to a new ISP. A simple ping test to 8.8.8.8 is successful. However, users complain of extreme slowness to any website and periods of no connectivity. Which of the following is the most likely cause?
A network engineer discovers network traffic that is sending confidential information to an unauthorized and unknown destination. Which of the following best describes the cause of this network traffic?
A network engineer is designing an internal network that needs to support both IPv4 and IPv6 routing. Which of the following routing protocols is capable of supporting both IPv4 and IPv6?
A network architect of a stock exchange broker is implementing a disaster recovery (DR), high-availability plan. Which of the following approaches would be the best fit?
An organization recently connected a new computer to the LAN. The user is unable to ping the default gateway. The technician examines the configuration and sees a self-assigned IP address. Which of the following is the most likely cause?
After installing a new 6E wireless router in a small office, a technician notices that some wireless devices are not able to achieve the rated speeds.
Which of the following should the technician check to troubleshoot the issue? (Select two)
A small business is deploying new phones, and some of the phones have full HD videoconferencing features. The Chief Information Officer (CIO) is concerned that the network might not be able to handle the traffic if it reaches a certain threshold. Which of the following can the network engineer configure to help ease these concerns?
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
An organization wants to ensure that incoming emails were sent from a trusted source. Which of the following DNS records is used to verify the source?
Which of the following layers of the OSI model is responsible for end-to-end encryption?
Which of the following is a type of NAC that uses a set of policies to allow or deny access to the network based on the user's identity?
Which of the following can be used when a server at a remote site is physically unreachable?
Which of the following technologies is the best choice to listen for requests and distribute user traffic across web servers?
A systems administrator needs to connect two laptops to a printer via Wi-Fi. The office does not have access points and cannot purchase any. Which of the following wireless network types best fulfills this requirement?
A network administrator needs to connect a department to a new network segment. They need to use a DHCP server located on another network. Which of the following can the administrator use to complete this task?
Which of the following steps in the troubleshooting methodology comes after using a top-to-top buttom examination of the OSI model to determine cause?
Which of the following network topologies contains a direct connection between every node in the network?
A firewall receives traffic on port 80 and forwards it to an internal server on port 88. Which of the following technologies is being leveraged?
Which of the following actions should be taken as part of the first step of the troubleshooting methodology?
Which of the following allows a user to connect to an isolated device on a stand-alone network?
Which of the following is used to redistribute traffic between one source and multiple servers that run the same service?
A network administrator needs to create a way to redirect a network resource that has been on the local network but is now hosted as a SaaS solution. Which of the following records should be used to accomplish the task?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses (one for a computer and one for a phone). Which of the following classful IPv4 address ranges will be best-suited for the network?
A company recently implemented a videoconferencing system that utilizes large amounts of bandwidth. Users start reporting slow internet speeds and an overall decrease in network performance. Which of the following are most likely the causes of the network performance issues? (Select two)
Which of the following technologies are X.509 certificates most commonly associated with?
Which of the following protocol ports should be used to securely transfer a file?
Which of the following objectives does an evil twin achieve?
A network administrator needs to change where the outside DNS records are hosted. Which of the following records should the administrator change the registrar to accomplish this task?
Which of the following ports is a secure protocol?
Which of the following best describes the amount of time between a disruptive event and the point that affected resources need to be back to fully functional status?
After changes were made to a firewall, users are no longer able to access a web server. A network administrator wants to ensure that ports 80 and 443 on the web server are still accessible from the user IP space. Which of the following commands is best suited to perfom this testing?
Users report performance issues on the network. A network administrator notices broadcast storms occurring. Which of the following protocols should the administrator configure to mitigate this issue?
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers' activities?
A network administrator needs to connect two routers in a point-to-point configuration and conserve IP space. Which of the following subnets should the administrator use?
A network technician is troubleshooting a web application's poor performance. The office has two internet links that share the traffic load. Which of the following tools should the technician use to determine which link is being used for the web application?
Which of the following ports creates a secure connection to a directory service?
Which of the following offers the ability to manage access at the cloud VM instance?
Which of the following describes the best reason for using BGP?
Which of the following can be implemented to add an additional layer of security between a corporate network and network management interfaces?
A Chief Information Officer wants a DR solution that runs only after a failure of the primary site and can be brought online quickly once recent backups are imported. Which of the following DR site solutions meets these requirements?
A systems administrator is looking for operating system information, running services, and network ports that are available on a server. Which of the following software tools should the administrator use to accomplish this task?
A network engineer configures a NIC that has an IP address of 192.168.123.232. Which of the following classes is this address an example of?
Which of the following would allow a network administrator to analyze attacks coming from the internet without affecting latency?
Which of the following is the best way to securely access a network appliance from an external location?
Which of the following is a type of NAC that uses a set of policies to allow or deny access to the network based on the user’s identity?
A user notifies a network administrator about losing access to a remote file server. The network administrator is able to ping the server and verifies the current firewall rules do not block access to the network fileshare. Which of the following tools wold help identify which ports are open on the remote file server?
A company security policy requires all network traffic from remote employees' corporate laptops to use the company’s VPN. Which of the following network access methods best describes this scenario?
Which of the following cloud service models most likely requires the greatest up-front expense by the customer when migrating a data center to the cloud?
A network administrator upgrades the wireless access points and wants to implement a configuration that gives users higher speed and less channel overlap based on device compatibility. Which of the following accomplishes this goal?
A technician is troubleshooting a computer issue for a user who works in a new annex of an office building. The user is reporting slow speeds and intermittent connectivity. The computer is connected via a Cat 6 cable to a distribution switch that is 492ft (150m) away. Which of the following should the technician implement to correct the issue?
An attack on an internal server is traced to an isolated guest network. Which of the following best describes the attack?
An organization requires the ability to send encrypted email messages to a partner from an email server that is hosted on premises. The organization prefers to use the standard default ports when creating firewall rules. Which of the following ports should be open to satisfy the requirements?
Which of the following services runs on port 636?
Which of the following allows a user to authenticate to multiple resources without requiring additional passwords?
A network administrator performed upgrades on a server and installed a new NIC to improve performance. Following the upgrades, usera are unable to reach the server. Which of the following is the most likely reason.
A VoIP phone is plugged in to a port but cannot receive calls. Which of the following needs to be done on the port to address the issue?
A technician is troubleshooting wireless connectivity near a break room. Whenever a user turns on the microwave, connectivity to the user's laptop is lost. Which of the following frequency bands is the laptop most likely using?
Which of the following is the most likely benefit of installing server equipment in a rack?
A network administrator is connecting two Layer 2 switches in a network. These switches must transfer data in multiple networks. Which of the following would fulfill this requirement?
A company’s Chief Information Security Officer requires that servers and firewalls have accurate timestamps when creating log files so that security analysts can correlate events during incident investigations. Which of the following should be implemented?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
A network engineer needs to correlate findings and receive alerts if there are brute force attacks, DDoS attacks, or port scanning happening within their network. Which of the following network monitoring technologies should the engineer implement?
A company upgrades its network and PCs to gigabit speeds. After the upgrade, users are not getting the expected performance. Technicians discover that the speeds of the endpoint NICs are inconsistent. Which of the following should be checked first to troubleshoot the issue?
Which of the following is the best reason to create a golden configuration?
A network administrator has been monitoring the company's servers to ensure that they are available. Which of the following should the administrator use for this task?
After extremely high temperatures cause a power outage, the servers automatically shut down, even though the UPSs for the servers still have hours of battery life. Which of the following should a technician recommend?
An administrator wants to find the top destination for traffic across the infrastructure on a specific day. Which of the following should the administrator use?
A wireless technician wants to implement a technology that will allow user devices to automatically navigate to the best available frequency standard. Which of the following technologies should the technician use?
A network administrator is trying to troubleshoot an issue with a newly installed switch that is not connecting to the network. The administrator logs on to the switch and observes collisions on the interface. Which of the following is most likely the issue?
Which of the following is a major difference between an IPS and IDS?
Which of the following source control features allows an administrator to test a new configuration without changing the primary configuration?
Which of the following appliances provides users with an extended footprint that allows connections from multiple devices within a designated WLAN?
Which of the following does BGP use for loop avoidance?
Which of the following explains what happens if a packet is lost in transit when using UDP?
A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
A network manager wants to implement a SIEM system to correlate system events. Which of the following protocols should the network manager verify?
Which of the following is associated with avoidance, acceptance, mitigation, and transfer?
A virtual machine has the following configuration:
•IPv4 address: 169.254.10.10
•Subnet mask: 255.255.0.0
The virtual machine can reach colocated systems but cannot reach external addresses on the Internet. Which of the following Is most likely the root cause?
Which of the following enables an organization to leverage an identity provider to manage access across SaaS applications?
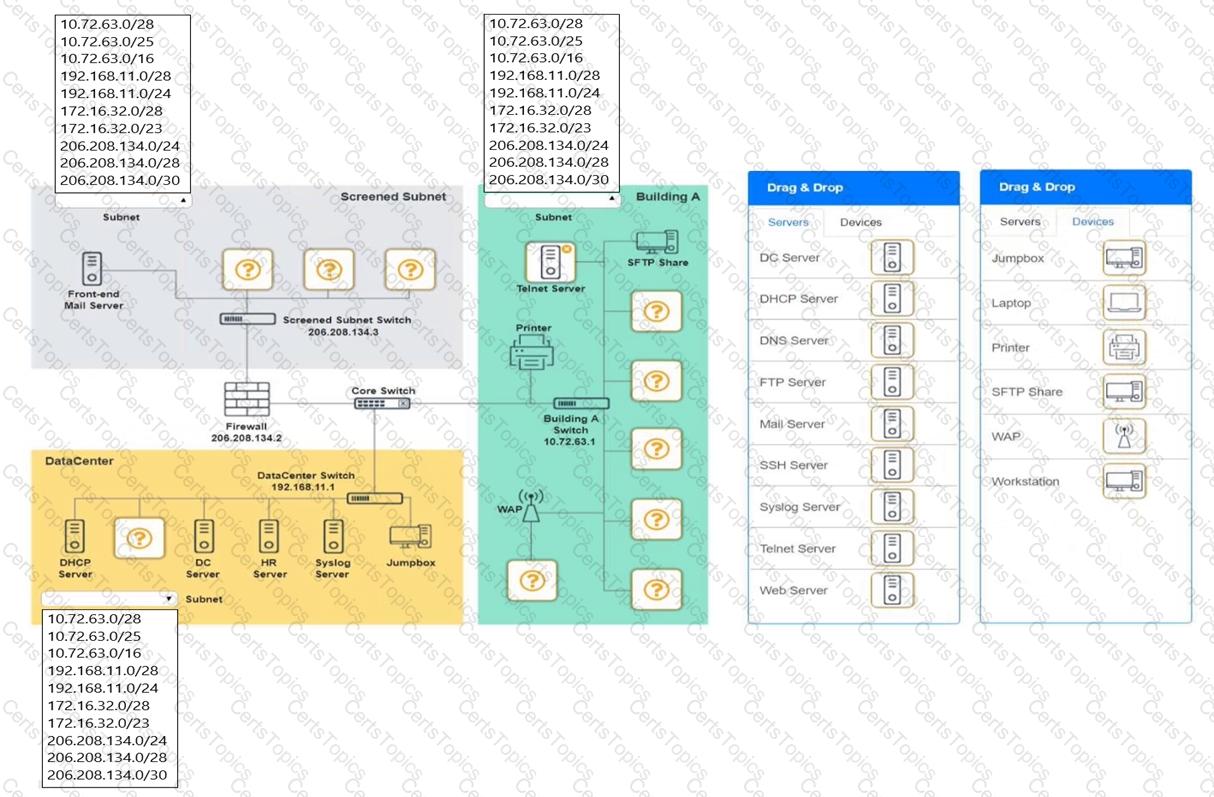
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following protocols is used to send networking status messages between clients and servers?
A network administrator is configuring a wireless network with an ESSID. Which of the following is a user benefit of ESSID compared to SSID?
Which of the following tools uses ICMP to help determine whether a network host is reachable?
Which of the following steps in the troubleshooting methodology includes checking logs for recent changes?
A network engineer is deploying switches at a new remote office. The switches have been preconfigured with hostnames and STP priority values. Based on the following table:
Switch Name
Priority
core-sw01
24576
access-sw01
28672
distribution-sw01
32768
access-sw02
36864
Which of the following switches will become the root bridge?
A network consultant needs to decide between running an ethernet uplink or using the built-in 5GHz-to-point functionality on a WAP. Which of the following documents provides the best information to assist the consultant with this decision?
A customer purchases a new UTM device and wants the development team to integrate some of the device’s data-reporting capabilities into the company’s custom internal support software. Which of the following features should the development team use to obtain the device’s data?
Which of the following disaster recovery concepts is calculated by dividing the total hours of operation by the total number of units?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
A user calls the help desk after business hours to complain that files on a device are inaccessible and the wallpaper was changed. The network administrator thinks that this issue is an isolated incident, but the security analyst thinks the issue might be a ransomware attack. Which of the following troubleshooting steps should be taken first?
A medical clinic recently configured a guest wireless network on the existing router. Since then, guests have been changing the music on the speaker system. Which of the following actions should the clinic take to prevent unauthorized access? (Select two).
Which of the following protocols is used to route traffic on the public internet?
Which of the following is the final step in the ticket management process?
A company is purchasing a 40Gbps broadband connection service from an ISP. Which of the following should most likely be configured on the 10G switch to take advantage of the new service?
Which of the following facilities is the best example of a warm site in the event of information system disruption?
A network technician is designing a LAN for a new facility. The company is expecting more than 300 devices to connect to the network. Which of the following masks will provide the most efficient subnet?
Which of the following network cables involves bouncing light off of protective cladding?
A network administrator is notified that a user cannot access resources on the network. The network administrator checks the physical connections to the workstation labeled User 3 and sees the Ethernet is properly connected. However, the network interface’s indicator lights are not blinking on either the computer or the switch. Which of the following Is the most likely cause?
A small business is choosing between static and dynamic routing for its network. Which of the following is the best reason to use dynamic routing in a growing network?
Which of the following protocols has a default administrative distance value of 90?
Which of the following VPN configurations forces a remote user to access internet resources through the corporate network?
A network administrator wants to update a geofencing policy to limit remote access to the corporate network based on country location. Which of the following would the administrator most likely leverage?
A customer calls the help desk to report issues connection to the internet. The customer can reach a local database server. A technician goes to the site and examines the configuration:
Which of the following is causing the user's issue?
Which of the following allows for the interception of traffic between the source and destination?
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches:
Switch 1
Port State Cost
1 Forward 2
2 Forward 2
Switch 2
Port State Cost
1 Forward 2
2 Forward 2
Which of the following best describes the issue?
A network technician is attempting to harden a commercial switch that was recently purchased. Which of the following hardening techniques best mitigates the use of publicly available information?
A network administrator suspects users are being sent to malware sites that are posing as legitimate sites. The network administrator investigates and discovers that user workstations are configured with incorrect DNS IP addresses. Which of the following should the network administrator implement to prevent this from happening again?
A network administrator is reviewing a production web server and observes the following output from the netstat command:
Which of the following actions should the network administrator take to harden the security of the web server?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host's TCP/IP stack first. Which of the following commands should the network administrator run?
A network administrator needs to add 255 useable IP addresses to the network. A /24 is currently in use. Which of the following prefixes would fulfill this need?
Which of the following layers in the OSI model is responsible for establishing, maintaining, and terminating connections between nodes?
A network rack has four servers and four switches with dual power supplies. Only one intelligent PDU is installed in the rack. Which of the following is the reason to add a second PDU?
Which of the following is used to store and deliver content to clients in a geographically distributed manner using edge servers?
A technician needs to set up a wireless connection that utilizes MIMO on non-overlapping channels. Which of the following would be the best choice?
A network administrator prepares a VLAN for a new office while planning for minimal IP address waste. The new office will have approximately 800 workstations. Which of the following network schemes meets the requirements?
Which of the following troubleshooting steps provides a change advisory board with the information needed to make a decision?
A company is implementing a new internal network in which all devices use IPv6 addresses. Which of the following routing protocols will be best for this setup?