A large number of routes typically exist in a BGP routing table, and transmitting such extensive routing information brings a heavy burden to a device. In order to address this problem, it is necessary to filter those routes to be advertised. You can configure a device to advertise only necessary routes or those that its peers require.
On an OSPF network, routers learn routing information on the entire network by exchanging LSAs. Which of the following values is the LS Age in the LSA header when an LSA is deleted?
As shown in the figure, data traffic is forwarded in tunnel mode along the path of STA -> HAP -> HAC -> upper-layer network before roaming. What is the flow direction of data traffic after Layer 3 roaming?
On an office network of an enterprise, OSPF is enabled on two directly connected routers. During adjacency establishment, the state machine stays in the 2-way state. Which of the following statements are not possible causes?
When configuring an ACL on a router, you can specify a unique number or name to identify the ACL. Once a named ACL is created, it cannot be modified. You can only delete the named ACL and reconfigure it.
A campus network uses OSPF for network communication. The display ospf peer command is run on a router, and the command output is as follows:
vbnet
Copy
Edit
OSPF Process 1 with Router ID 10.0.2.2
Area 0.0.0.0 interface 10.0.235.2 (GigabitEthernet0/0/1)'s neighbors
Router ID: 10.0.5.5 Address: 10.0.235.5
State: Full Mode: Nbr is Master Priority: 1
DR: 10.0.235.5 BDR: 10.0.235.3 MTU: 0
Dead timer due in 40 sec
Area 0.0.0.0 interface 10.0.24.2 (Serial1/0/1)'s neighbors
Router ID: 10.0.4.4 Address: 10.0.24.4
State: Full Mode: Nbr is Master Priority: 1
DR: None BDR: None MTU: 0
Dead timer due in 35 sec
Which of the following statements are true about the device?
On a WLAN, the HSB service sets up an HSB channel between two devices that back up each other, maintains the channel status, and backs up data. Which of the following can HSB back up in real time?
ICMPv6 messages are classified as error or informational messages.
Which of the following statements regarding IGMPv1 and IGMPv2 are true?
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
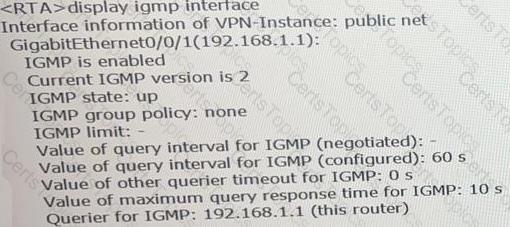
Which of the following statements is false, based on the following IGMP information on an interface of RTA?XC
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
Which of the following statements regarding OSPF multi-instance is false?
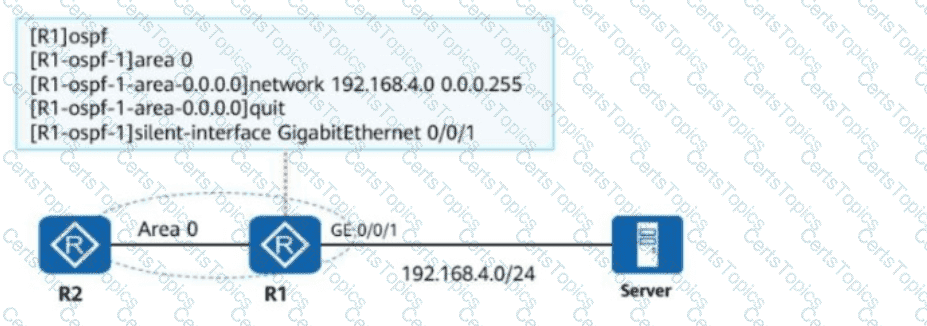
The following figure shows the OSPF network of an enterprise and the OSPF configurations of R1. Which of the following statements is false about the network?
According to BGP route selection rules, the route with the higher Local_Pref is preferred.
In PIM-DM, which of the following processes are involved in SPT establishment?
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
If a router ID is configured in both the system via and the BGP view, BGP uses the router ID configured in the BGP view because the BGP view takes precedence over the system view.
Which of the following attacks is not the network layer attack?
On an OSPF or IS-IS network, the filter-policy import command can be run on a router to filter out the LSAs forwarded by its neighbors.
In the OSPF protocol, inter-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
Compress the 2001:0DBB:B8:0000:C030:0000:0000:09A0:CDEF address.___________(if the answer contains letters, capitalize them.)
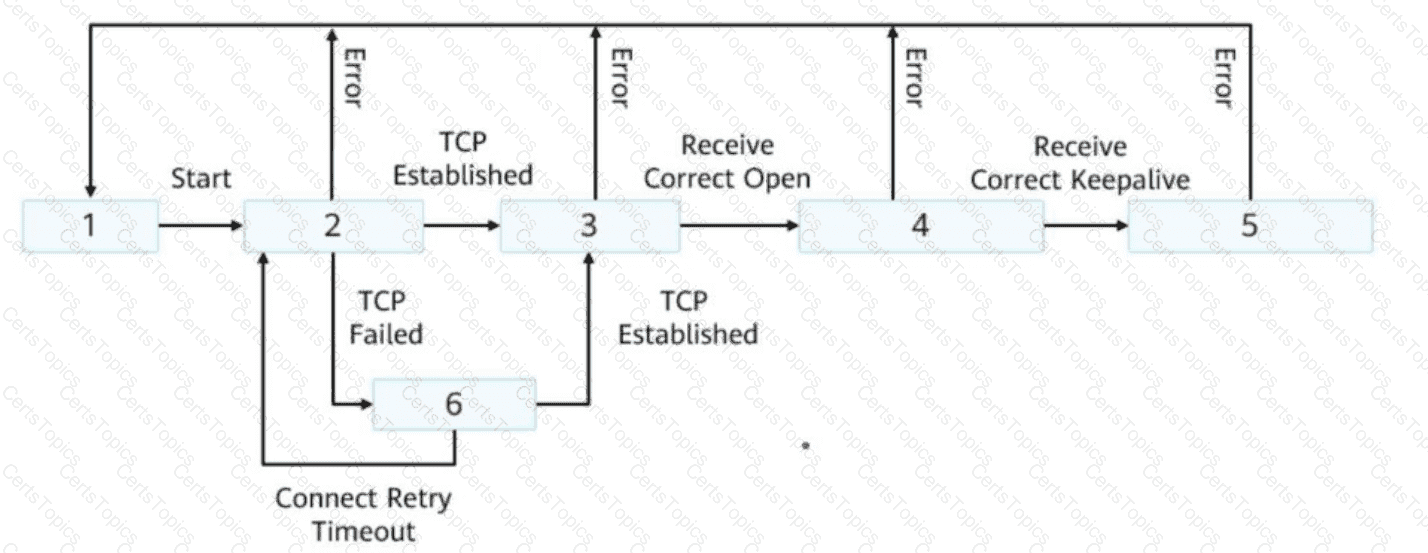
The following figure shows the BGP state switching mechanism. Drag the following BGP states to the corresponding sequence numbers.

GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
There are two types of routing entries on a PIM network. (S, G) routing entries are used to set up on a PIM network and are applicable to both PIM-DM and PIM-SM networks.
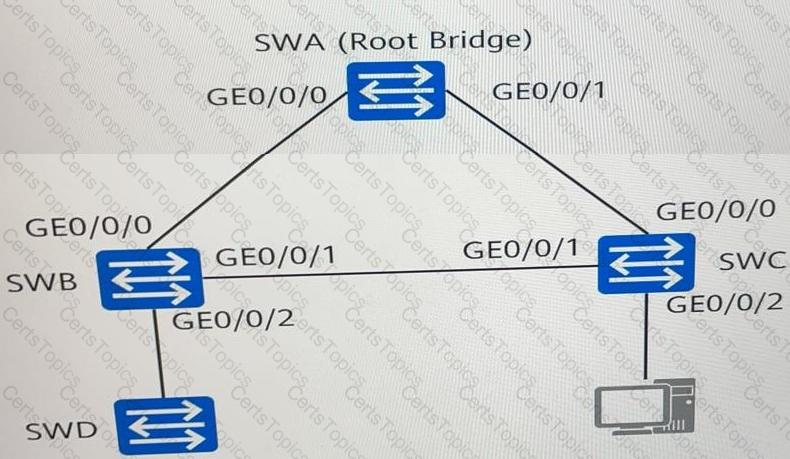
As shown in the figure, SWA, SWB, SWC, and SWD run the Rapid Spanning Tree Protocol (RSTP). Which of the following statements are true?
On an enterprise network, the directly connected interfaces of two OSPF routers are on different network segments and have different masks. To establish an OSPF neighbor relationship between the two interfaces, you can change their network types to which of the following?
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
On an STP network, parameters used for role election, such as the root bridge ID, root path cost, and bridge ID, are all fields in BPDUs.
A session is an entry used to record the connection status of a protocol and is fundamental for the firewall to forward packets. Which of the following protocol packets will the firewall create sessions for?
OSPF supports area authentication and interface authentication. If both authentication modes are configured, Interface authentication takes preference over area authentication.
The native AC function allows an agile switch to integrate AC capabilities, achieving wired and wireless convergence. The agile switch centrally manages wired and wireless service traffic.
A filter named si is configured on a device using the as-path-filter command and is applied to a specified BGP peer. The detailed configurations are as follows:
csharp
Copy
[SW1] ip as-path-filter si permit _65500$
[SW1] bgp 65100
[SW1-bgp] ipv4-family unicast
[SW1-bgp-af-ipv4] peer 10.1.1.2 as-path-filter si import
After the configuration is complete, which of the following statements is true about the way the local device processes the routes received from the peer?
Which Of the following IEEE 802.11 standards is also known as Wi-Fi 6?
As shown in the following figure, a new AP is deployed In dual link MSB networking (load balancing mode). Which AC will the connect to?
Link aggregation is a common network technology. Which of the following are advantages of link aggregation?
Which of the following scenarios is not suitable for deploying interface PBR?
When receiving a packet that does not match any session table entry, the firewall discards the packet to prevent external attacks and ensure internal information security.
Which of the following statements about BFD operating modes are true?
Which of the following protocols are multi-channel protocols?
BFD for OSPF is deployed on a directly connected link. If the physical link is disconnected, drag the following BFD processes to the corresponding sequence numbers.
If the interval for two consecutive packets of a TCP session reaching the firewall is longer than the aging time of the session, the firewall deletes the session information from the session table to ensure network security.
When two routers exchange LSDB information using DD packets, a master/slave relationship is formed first, the router with a larger router ID is the master, and determine the MS bit.
When a packet passes through a firewall, the firewall creates a session connection for the packet to guide subsequent forwarding of the packet. However, the firewall does not create session entries for all packets. For which of the following packets does the firewall not create session entries when the packet reaches the firewall?
On an OSPF network, if a router receives an update of an LSA that exists in the local LSDB, the router updates the LSDB and floods the LSA.
Which of the following statements regarding different LSA types is false?
In IP multicast, RPF routes can be elected only from among unicast routes and multicast static routes.
Which of the following attributes cannot be directly referenced in an apply clause of a route-policy?
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
Which of the following statements regarding the BGP error display of a router is false?
In BGP, the AS_Path attribute records the numbers of all ASs that a route passes through from the local end to the destination in the vector order.
Which of the following statements is false about the attribute change during route transmission?
In BGP, the origin attribute of the routes imported using the import-route command is incomplete.
When an SSH client accesses an SSH server for the first time and the SSH server's public key is not configured on the SSH client, you can enable first-time authentication on the SSH client. This allows the SSH client to access the SSH server and saves the SSH server's public key on the SSH client. In this way, the next time the SSH client accesses the SSH server, the SSH client can use the saved public key to authenticate the SSH server.
After HSB is configured, the HSB channel fails to be established and cannot back up information on the active device to the standby device. What are the possible causes for this HSB function failure?
Based on IGMP snooping, IGMP snooping proxy enables a switch to act as a substitute for an upstream Layer 3 device to send IGMP Query messages to downstream hosts, and also to act as a substitute for downstream hosts to send IGMP Report/Leave messages to an upstream device. As such, this function conserves bandwidth between the upstream device and the local device.
In which of the following scenarios can a neighbor relationshipnotbe established between two directly connected Huawei routers after IS-IS is configured?
On an RSTP network, you can set the STP priority of a switch to specify the switch as the root bridge.
Which of the following values is thedefault STP priorityof a Huawei switch?
On an enterprise WLAN where Portal authentication is deployed, an AC functions as an access device and communicates with a Portal server using the Portal protocol. Which of the following statements are true about the Portal protocol?
On an IS-IS network, routers send LSPs to exchange link state information. LSPs are classified into Level-1 LSPs and Level-2 LSPs and have the same format. Which of the following parts constitute the LSP ID in an LSP?
A route-policy can have multiple nodes, and each node can have multiple if-match and apply clauses. Which of the following statements are false?
During routine O&M, an engineer finds that theHold Timeparameters of two devices are inconsistent. In this case, which of the following situations occurs?
There are two BFD operating modes. In_______mode, the local end sends BFD Control packets at specified intervals, and the remote end checks whether the local end periodically sends BFD Control packets. (Use lowercase letters.)
As shown in the figure, R1 imports the direct route 10.1.1.0/24 to OSPF. An engineer enables bidirectional route re-advertisement on R2 and R3, and configures the following commands on R3. After the network becomes stable, which of the following is thePrevalue of the route 10.1.1.0/24 in the routing table of R4?
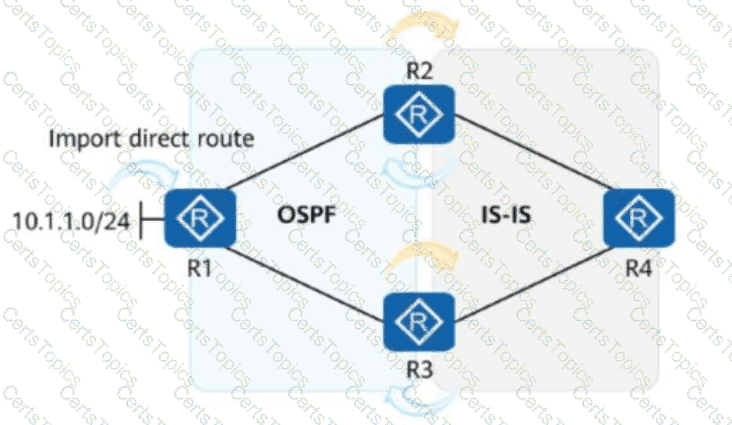
[R3]acl 2000
[R3-acl-basic-2000] rule permit source 10.1.1.0 0
[R3-acl-basic-2000] quit
[R3]route-policy hcip permit node 10
[R3-route-policy-10] if-match acl 2000
[R3-route-policy-10] apply preference 14
[R3-route-policy-10] quit
[R3]ospf 1
[R3-ospf-1] preference ase route-policy hcip
In BGP, Keepalive messages are used to maintain BGP peer relationships. When a BGP router receives a Keepalive message from a peer, the BGP router sets the state of the peer to Established and periodically sends Keepalive messages to maintain the connection. By default, the device sends Keepalive messages every seconds.
When deploying BFD, you need to adjust some parameters so that it can better detect the network status. Which of the following statements isfalseabout BFD optimization?
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
Compared with RSTP, which of the following port roles are added to MSTP?
An IP prefix list is a common matching tool used in routing policies. Which of the following cannot be configured as matching conditions in an IP prefix list on a Huawei router?
On the campus OSPF network shown in the following figure, the interfaces connecting the five routers are GE interfaces, and their costs are not changed. The import-route command is run on R1. After the network converges, the route to the server at 192.168.1.0/24 is queried on R2. Which of the following is the cost of this route?
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
Preferences of routing protocols determine the sequence In which a router selects a route among routes to the same destination /earned through different routing protocols.
An enterprise uses Huawei routers to deploy an IS-IS network for network-wide communication. An engineer wants to change the interface cost to control route selection. By default, which of the following values is the maximum cost that can be configured?
On the OSPF network shown in the figure, an adjacency has been established between R1 and R2. An engineer configures the commands in the figure on R2. In this case, which of the following routing entries may exist in the routing table of R2?
Which of the following routing protocols support the default route through command configuration?
Which of the following statements about stack split is false?
As shown in the figure, SWA, SWB, and SWC run the Rapid Spanning Tree Protocol (RSTP). What are the roles of SWB's GE0/0/2 and SWC's GE0/0/1?
To inject IGP routes into BGP routes, you can only use the network command.
OSPF has multiple types of routes with varying priorities. Which of the following types of routes has the lowest priority when they have the same prefix?
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
IPv6 defines multiple types of addresses. Which of the following statements is false about these addresses?
Which of the following statements regarding the firewall zone security level is false?
Which of the following statements regarding OSPF is true?
In addition to a route reflector, the confederation is another method that reduces the number of IBGP connections in an AS.
Which of the following statements are true about the confederation technology? (Choose all that apply)
The traffic limiting policy feature only supports the number of connections initiated by the specified IP or the number of connections received.
Which of the following statements is true about BGP?
Security policy is the core feature of firewalls. Only valid traffic that complies with security policies can be forwarded by firewalls. Which of the following statements are true about security policy matching rules?
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
Which three transmission modes are supported for IPv4 packets?
In an MST region, MSTP independently calculates an MSTI for each VLAN based on mappings between VLANs and MSTIs.
Which of the following statements is false about the characteristics of MSTIs?