During a black-box pen test you attempt to pass IRC traffic over port 80/TCP from a compromised web enabled host. The traffic gets blocked; however, outbound HTTP traffic is unimpeded. What type of firewall is inspecting outbound traffic?
The security team of Debry Inc. decided to upgrade Wi-Fi security to thwart attacks such as dictionary attacks and key recovery attacks. For this purpose, the security team started implementing cutting-edge technology that uses a modern key establishment protocol called the simultaneous authentication of equals (SAE), also known as dragonfly key exchange, which replaces the PSK concept.
What is the Wi-Fi encryption technology implemented by Debry Inc.?
During a red team operation on a segmented enterprise network, the testers discover that the organization’s perimeter devices deeply inspect only connection-initiation packets (such as TCP SYN and HTTP requests). Response packets and ACK packets within established sessions, however, are minimally inspected. The red team needs to covertly transmit payloads to an internal compromised host by blending into normal session traffic. Which approach should they take to bypass these defensive mechanisms?
If executives are found liable for not properly protecting their company’s assets and information systems, what type of law would apply in this situation?
Jim, a professional hacker, targeted an organization that is operating critical Industrial Infrastructure. Jim used Nmap to scan open pons and running services on systems connected to the organization's OT network. He used an Nmap command to identify Ethernet/IP devices connected to the Internet and further gathered Information such as the vendor name, product code and name, device name, and IP address. Which of the following Nmap commands helped Jim retrieve the required information?
Clark, a professional hacker, attempted to perform a Btlejacking attack using an automated tool, Btlejack, and hardware tool, micro:bit. This attack allowed Clark to hijack, read, and export sensitive information shared between connected devices. To perform this attack, Clark executed various btlejack commands. Which of the following commands was used by Clark to hijack the connections?
An organization uses SHA-256 for data integrity verification but still experiences unauthorized data modification. Which cryptographic tool would best resolve this issue?
Which of the following Linux commands will resolve a domain name into IP address?
Clark is gathering sensitive information about a competitor and uses a tool to input the target’s server IP address to identify network range, OS, and topology. What tool is he using?
David is a security professional working in an organization, and he is implementing a vulnerability management program in the organization to evaluate and control the risks and vulnerabilities in its IT infrastructure. He is currently executing the process of applying fixes on vulnerable systems to reduce the impact and severity of vulnerabilities. Which phase of the vulnerability-management life cycle is David currently in?
You have the SOA presented below in your Zone.
Your secondary servers have not been able to contact your primary server to synchronize information.
How long will the secondary servers attempt to contact the primary server before it considers that zone is dead and stops responding to queries?
collegae.edu. SOA, cikkye.edu ipad.college.edu. (200302028 3600 3600 604800 3600)
Which type of malware spreads from one system to another or from one network to another and causes similar types of damage as viruses do to the infected system?
Widespread fraud ac Enron. WorldCom, and Tyco led to the creation of a law that was designed to improve the accuracy and accountability of corporate disclosures. It covers accounting firms and third parties that provide financial services to some organizations and came into effect in 2002. This law is known by what acronym?
There are multiple cloud deployment options depending on how isolated a customer's resources are from those of other customers. Shared environments share the costs and allow each customer to enjoy lower operations expenses. One solution Is for a customer to Join with a group of users or organizations to share a cloud environment. What is this cloud deployment option called?
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A corporation uses both hardware-based and cloud-based solutions to distribute incoming traffic and absorb DDoS attacks, ensuring legitimate requests remain unaffected. Which DDoS mitigation strategy is being utilized?
During an internal security assessment of a medium-sized enterprise network, a security analyst notices an unusual spike in ARP traffic. Closer inspection reveals that one particular MAC address is associated with multiple IP addresses across different subnets. The ARP packets were unsolicited replies rather than requests, and several employees from different departments have reported intermittent connection drops, failed logins, and broken intranet sessions. The analyst suspects an intentional interference on the local network segment. What is the most likely cause of this abnormal behavior?
Gavin owns a white-hat firm and is performing a website security audit. He begins with a scan looking for misconfigurations and outdated software versions. Which tool is he most likely using?
During a security audit, a penetration tester observes abnormal redirection of all traffic for a financial institution’s primary domain. Users are being redirected to a phishing clone of the website. Investigation shows the authoritative DNS server was compromised and its zone records modified to point to the attacker’s server. This demonstrates total manipulation of domain-level resolution, not cache poisoning or client-side attacks. Which technique is being used in this scenario?
During an internal assessment, a penetration tester gains access to a hash dump containing NTLM password hashes from a compromised Windows system. To crack the passwords efficiently, the tester uses a high-performance CPU setup with Hashcat, attempting millions of password combinations per second. Which technique is being optimized in this scenario?
A penetration tester is hired by a company to assess its vulnerability to social engineering attacks targeting its IT department. The tester decides to use a sophisticated pretext involving technical jargon and insider information to deceive employees into revealing their network credentials. What is the most effective social engineering technique the tester should employ to maximize the chances of obtaining valid credentials without raising suspicion?
An organization uses SHA-256 for data integrity checks but still experiences unauthorized data modification. Which cryptographic tool can help resolve this issue?
which type of virus can change its own code and then cipher itself multiple times as it replicates?
A penetration tester is tasked with mapping an organization's network while avoiding detection by sophisticated intrusion detection systems (IDS). The organization employs advanced IDS capable of recognizing common scanning patterns. Which scanning technique should the tester use to effectively discover live hosts and open ports without triggering the IDS?
Ethical hacker jane Smith is attempting to perform an SQL injection attach. She wants to test the response time of a true or false response and wants to use a second command to determine whether the database will return true or false results for user IDs. which two SQL Injection types would give her the results she is looking for?
A penetration tester evaluates an industrial control system (ICS) that manages critical infrastructure. The tester discovers that the system uses weak default passwords for remote access. What is the most effective method to exploit this vulnerability?
Fleet vehicles with smart locking systems were compromised after attackers captured unique signals from key fobs. What should the security team prioritize to confirm and prevent this attack?
You are a security analyst conducting a footprinting exercise for a new client to gather information without direct interaction. After using search engines and public databases, you consider using Google Hacking (Google Dorking) techniques to uncover further vulnerabilities. Which option best justifies this decision?
A penetration tester discovers that a system is infected with malware that encrypts all files and demands payment for decryption. What type of malware is this?
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
A Nessus scan reveals a critical SSH vulnerability (CVSS 9.0) allowing potential remote code execution on a Linux server. What action should be immediately prioritized?
A penetration tester identifies malware on a system that hides its presence and gives an attacker access to administrative functions without being detected. What type of malware is this?
Which advanced mobile attack is hardest to detect and mitigate?
Suppose your company has just passed a security risk assessment exercise. The results display that the risk of the breach in the main company application is 50%. Security staff has taken some measures and
implemented the necessary controls. After that, another security risk assessment was performed showing that risk has decreased to 10%. The risk threshold for the application is 20%. Which of the following risk decisions will be the best for the project in terms of its successful continuation with the most business profit?
Attacker Simon targeted the communication network of an organization and disabled the security controls of NetNTLMvl by modifying the values of LMCompatibilityLevel, NTLMMinClientSec, and RestrictSendingNTLMTraffic. He then extracted all the non-network logon tokens from all the active processes to masquerade as a legitimate user to launch further attacks. What is the type of attack performed by Simon?
The tools which receive event logs from servers, network equipment, and applications, and perform analysis and correlation on those logs, and can generate alarms for security relevant issues, are known as what?
Which of the following incident handling process phases is responsible for defining rules, collaborating human workforce, creating a back-up plan, and testing the plans for an organization?
An experienced cyber attacker has created a fake Linkedin profile, successfully impersonating a high-ranking official from a well-established company, to execute a social engineering attack. The attacker then connected with other employees within the organization, receiving invitations to exclusive corporate events and gaining
access to proprietary project details shared within the network. What advanced social engineering technique has the attacker primarily used to exploit the system and what is the most likely immediate threat to the organization?
What is the first step for a hacker conducting a DNS cache poisoning (DNS spoofing) attack against an organization?
is a set of extensions to DNS that provide the origin authentication of DNS data to DNS clients (resolvers) so as to reduce the threat of DNS poisoning, spoofing, and similar types of attacks.
In the context of Windows Security, what is a 'null' user?
Which DNS resource record can indicate how long any "DNS poisoning" could last?
You discover an unpatched Android permission-handling vulnerability on a device with fully updated antivirus software. What is the most effective exploitation approach that avoids antivirus detection?
A penetration tester suspects that a web application's product search feature is vulnerable to SQL injection. The tester needs to confirm this by manipulating the SQL query. What is the best technique to test for SQL injection?
You are a cybersecurlty consultant for a smart city project. The project involves deploying a vast network of loT devices for public utilities like traffic control, water supply, and power grid management The city administration is concerned about the possibility of a Distributed Denial of Service (DDoS) attack crippling these critical services. They have asked you for advice on how to prevent such an attack. What would be your primary recommendation?
You have compromised a server on a network and successfully opened a shell. You aimed to identify all operating systems running on the network. However, as you attempt to fingerprint all machines in the network using the nmap syntax below, it is not going through.
invictus@victim_server:~$ nmap -T4 -O 10.10.0.0/24
TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING!
What seems to be wrong?
An attacker changes the profile information of a particular user (victim) on the target website. The attacker uses this string to update the victim’s profile to a text file and then submit the data to the attacker’s database.
< iframe style=““display:none”” > < /iframe >
What is this type of attack (that can use either HTTP GET or HTTP POST) called?
Which of the following tools can be used for passive OS fingerprinting?
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of control objectives. Each objective contains one or more requirements, which must be followed in order to achieve compliance. Which of the following requirements would best fit under the objective, "Implement strong access control measures"?
in this form of encryption algorithm, every Individual block contains 64-bit data, and three keys are used, where each key consists of 56 bits. Which is this encryption algorithm?
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet. What is the recommended architecture in terms of server placement?
Which Intrusion Detection System is the best applicable for large environments where critical assets on the network need extra scrutiny and is ideal for observing sensitive network segments?
Attacker Rony Installed a rogue access point within an organization's perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
Tremp is an IT Security Manager planning to deploy an IDS. He needs a solution that:
Verifies success/failure of an attack
Monitors system activities
Detects local (host-based) attacks
Provides near real-time detection
Doesn’t require additional hardware
Has a lower entry cost
Which type of IDS is best suited for Tremp’s requirements?
A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what driver and library are required to allow the NIC to work in promiscuous mode?
George is a security professional working for iTech Solutions. He was tasked with securely transferring sensitive data of the organization between industrial systems. In this process, he used a short-range communication protocol based on the IEEE 203.15.4 standard. This protocol is used in devices that transfer data infrequently at a low rate in a restricted area, within a range of 10-100 m. What is the short-range wireless communication technology George employed in the above scenario?
During a cryptographic audit of a legacy system, a security analyst observes that an outdated block cipher is leaking key-related information when analyzing large sets of plaintext–ciphertext pairs. What approach might an attacker exploit here?
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
A penetration tester is conducting an external assessment of a corporate web server. They start by accessing and observe multiple Disallow entries that reference directories such as /admin-panel/, /backup/, and /confidentialdocs/. When the tester directly visits these paths via a browser, they find that access is not restricted by authentication and gain access to sensitive files, including server configuration and unprotected credentials. Which stage of the web server attack methodology is demonstrated in this scenario?
A penetration tester needs to identify open ports and services on a target network without triggering the organization's intrusion detection systems, which are configured to detect high-volume traffic and common scanning techniques. To achieve stealth, the tester decides to use a method that spreads out the scan over an extended period. Which scanning technique should the tester employ to minimize the risk of detection?
A zero-day vulnerability is actively exploited in a critical web server, but no vendor patch is available. What should be the FIRST step to manage this risk?
which of the following protocols can be used to secure an LDAP service against anonymous queries?
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
During testing against a network protected by a signature-based IDS, the tester notices that standard scans are blocked. To evade detection, the tester sends TCP headers split into multiple small IP fragments so the IDS cannot reassemble or interpret them, but the destination host can. What technique is being used?
Robin, a professional hacker, targeted an organization's network to sniff all the traffic. During this process.
Robin plugged in a rogue switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network.
What is the attack performed by Robin in the above scenario?
A technician is resolving an issue where a computer is unable to connect to the Internet using a wireless access point. The computer is able to transfer files locally to other machines, but cannot successfully reach the Internet. When the technician examines the IP address and default gateway they are both on the 192.168.1.0/24. Which of the following has occurred?
What would be the purpose of running "wget 192.168.0.15 -q -S" against a web server?
Miley, a professional hacker, decided to attack a target organization's network. To perform the attack, she used a tool to send fake ARP messages over the target network to link her MAC address with the target system's IP address. By performing this, Miley received messages directed to the victim's MAC address and further used the tool to intercept, steal, modify, and block sensitive communication to the target system.
What is the tool employed by Miley to perform the above attack?
Why is using Google Hacking justified during passive footprinting?
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice’s machine. From the command prompt, she types the following command:
What is Eve trying to do?
John, a professional hacker, targeted CyberSol Inc., an MNC. He decided to discover the IoT devices connected in the target network that are using default credentials and are vulnerable to various hijacking attacks. For this purpose, he used an automated tool to scan the target network for specific types of IoT devices and detect whether they are using the default, factory-set credentials. What is the tool employed by John in the above scenario?
An ethical hacker needs to gather detailed information about a company's internal network without initiating any direct interaction that could be logged or raise suspicion. Which approach should be used to obtain this information covertly?
Which method of password cracking takes the most time and effort?
A penetration tester is investigating a web server that allows unrestricted file uploads without validating file types. Which technique should be used to exploit this vulnerability and potentially gain control of the server?
A penetration tester is tasked with uncovering historical content from a company’s website, including previously exposed login portals or sensitive internal pages. Direct interaction with the live site is prohibited due to strict monitoring policies. To stay undetected, the tester decides to explore previously indexed snapshots of the organization’s web content saved by external sources. Which approach would most effectively support this passive information-gathering objective?
Vlady wants to improve security awareness among non-technical employees who demonstrate poor security practices. What should be his first step?
An ethical hacker conducts testing with full knowledge and permission. What type of hacking is this?
What type of analysis is performed when an attacker has partial knowledge of inner-workings of the application?
Tess King is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc.) for a Domain.
What do you think Tess King is trying to accomplish? Select the best answer.
Which results will be returned with the following Google search query?
site:target.com –site:Marketing.target.com accounting
An organization decided to harden its security against web-application and web-server attacks. John, a security personnel in the organization, employed a security scanner to automate web-application security testing and to guard the organization's web infrastructure against web-application threats. Using that tool, he also wants to detect XSS, directory transversal problems, fault injection, SQL injection, attempts to execute commands, and several other attacks. Which of the following security scanners will help John perform the above task?
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems, and intrusion detection/prevention tools in your company's network. You are confident that hackers will never be able to gain access. Your peer, Peter Smith, disagrees and says the presence of a “weakest link” still exposes the network.
What is Peter Smith talking about?
A financial services firm is experiencing a sophisticated DoS attack on their DNS servers using DNS amplification and on their web servers using HTTP floods. Traditional firewall rules and IDS are failing to mitigate the attack effectively. To protect their infrastructure without impacting legitimate users, which advanced mitigation strategy should the firm implement?
A tester evaluates a login form that builds SQL queries using unsanitized input. By submitting a single quote ('), the tester bypasses authentication and logs in. What type of SQL injection occurred?
An attacker gained escalated privileges on a critical server. What should be done FIRST to contain the threat with minimal disruption?
Which of the following scanning method splits the TCP header into several packets and makes it difficult for packet filters to detect the purpose of the packet?
As a Certified Ethical Hacker assessing session management vulnerabilities in a secure web application using MFA, encrypted cookies, and a WAF, which technique would most effectively exploit a session management weakness while bypassing these defenses?
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
[Note: Since the log extract is not shown in your message, we must rely on common indicators in similar scenarios.]
If the log shows paths such as:
Then the correct answer is:
Scenario: Joe turns on his home computer to access personal online banking. When he enters the URL the website is displayed, but it prompts him to re-enter his credentials as if he has never visited the site before. When he examines the website URL closer, he finds that the site is not secure and the web address appears different. What type of attack he is experiencing?.
A certified ethical hacker is conducting a Whois footprinting activity on a specific domain. The individual is leveraging various tools such as Batch IP Converter and Whols Analyzer Pro to retrieve vital details but is unable to gather complete Whois information from the registrar for a particular set of data. As the hacker, what might be the probable data model being utilized by the domain's registrar for storing and looking up
Who is information?
You discover a Web API integrated with webhooks and an existing administrative web shell. Your objective is to compromise the system while leaving minimal traces. Which technique is most effective?
what are common files on a web server that can be misconfigured and provide useful Information for a hacker such as verbose error messages?
PGP, SSL, and IKE are all examples of which type of cryptography?
During an Xmas scan, what indicates a port is closed?
During a reconnaissance mission, an ethical hacker uses Maltego, a popular footprinting tool, to collect information about a target organization. The information includes the target's Internet infrastructure details (domains, DNS names, Netblocks, IP address information). The hacker decides to use social engineering
techniques to gain further information. Which of the following would be the least likely method of social engineering to yield beneficial information based on the data collected?
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity. What tool would you most likely select?
Which advanced session hijacking technique is hardest to detect and mitigate in a remote-access environment?
Allen, a professional pen tester, was hired by xpertTech solutWns to perform an attack simul-ation on the organization's network resources. To perform the attack, he took advantage of the NetBIOS API and targeted the NetBIOS service. B/enumerating NetBIOS, he found that port 139 was open and could see the resources that could be accessed or viewed on a remote system. He came across many NetBIOS codes during enumeration.
identify the NetBIOS code used for obtaining the messenger service running for the logged-in user?
Tony wants to integrate a 128-bit symmetric block cipher with key sizes of 128, 192, or 256 bits into a software program, which involves 32 rounds of computational operations that include substitution and permutation operations on four 32-bit word blocks using 8-variable S-boxes with 4-bit entry and 4-bit exit.
Which of the following algorithms includes all the above features and can be integrated by Tony into the software program?
An ethical hacker is testing the security of a website's database system against SQL Injection attacks. They discover that the IDS has a strong signature detection mechanism to detect typical SQL injection patterns.
Which evasion technique can be most effectively used to bypass the IDS signature detection while performing a SQL Injection attack?
Which technique best exploits session management despite MFA, encrypted cookies, and WAFs?
BitLocker encryption has been implemented for all the Windows-based computers in an organization. You are concerned that someone might lose their cryptographic key. Therefore, a mechanism was implemented to recover the keys from Active Directory.
What is this mechanism called in cryptography?
A red team member uses an access token obtained from an Azure function to authenticate with Azure PowerShell and retrieve storage account keys. What kind of abuse does this scenario demonstrate?
A penetration tester has gained access to a target system using default credentials. What is the most effective next step to escalate privileges on the system?
While using your bank’s online servicing you notice the following string in the URL bar:
" &Damount=10980&Camount=21"
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
Which of the following steps for risk assessment methodology refers to vulnerability identification?
An organization is performing a vulnerability assessment tor mitigating threats. James, a pen tester, scanned the organization by building an inventory of the protocols found on the organization's machines to detect which ports are attached to services such as an email server, a web server or a database server. After identifying the services, he selected the vulnerabilities on each machine and started executing only the relevant tests. What is the type of vulnerability assessment solution that James employed in the above scenario?
An Nmap SMTP enumeration script returns valid usernames. What misconfiguration is being exploited?
During an internal red team engagement, an operator discovers that TCP port 389 is open on a target system identified as a domain controller. To assess the extent of LDAP exposure, the operator runs the command ldapsearch -h
Alice needs to send a confidential document to her coworker. Bryan. Their company has public key infrastructure set up. Therefore. Alice both encrypts the message and digitally signs it. Alice uses_______to encrypt the message, and Bryan uses__________to confirm the digital signature.
During a cloud security assessment, you discover a former employee still has access to critical cloud resources months after leaving. Which practice would most effectively prevent this?
Infected systems receive external instructions over HTTP and DNS, with fileless payloads modifying system components. What is the most effective action to detect and disrupt this malware?
A critical flaw exists in a cloud provider’s API. What is the most likely threat?
During a routine security audit, administrators found that cloud storage backups were illegally accessed and modified. What countermeasure would most directly mitigate such incidents in the future?
You receive an email prompting you to download “Antivirus 2010” software using a suspicious link. The software claims to provide protection but redirects you to an unknown site.
How will you determine if this is a Real or Fake Antivirus website?
Which technique is commonly used by attackers to evade firewall detection?
When conducting a penetration test, it is crucial to use all means to get all available information about the target network. One of the ways to do that is by sniffing the network. Which of the following cannot be performed by passive network sniffing?
What is the main difference between ethical hacking and malicious hacking?
A Certified Ethical Hacker (CEH) is given the task to perform an LDAP enumeration on a target system. The system is secured and accepts connections only on secure LDAP. The CEH uses Python for the enumeration process. After successfully installing LDAP and establishing a connection with the target, he attempts to fetch details like the domain name and naming context but is unable to receive the expected response. Considering the circumstances, which of the following is the most plausible reason for this situation?
How can rainbow tables be defeated?
Attackers abused Android Debug Bridge (ADB) to issue unauthorized commands. What is the strongest countermeasure?
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SYN ping scan?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
What is this attack?
A kernel-level rootkit is discovered. What is the safest remediation strategy?
While testing a web application in development, you notice that the web server does not properly ignore the “dot dot slash” (../) character string and instead returns the file listing of a folder structure of the server.
What kind of attack is possible in this scenario?
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly.
What is the best Nmap command you will use?
As an IT Security Analyst, you’ve been asked to review the security measures of an e-commerce website that relies on a SQL database for storing sensitive customer data. Recently, an anonymous tip has alerted you to a possible threat: a seasoned hacker who specializes in SQL Injection attacks may be targeting your system. The site already employs input validation measures to prevent basic injection attacks, and it blocks any user inputs containing suspicious patterns. However, this hacker is known to use advanced SQL Injection techniques. Given this situation, which of the following strategies would the hacker most likely adopt to bypass your security measures?
Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications. He installed a fake communication tower between two authentic endpoints to mislead the victim. Bobby used this virtual tower to interrupt the data transmission between the user and real tower, attempting to hijack an active session, upon receiving the users request. Bobby manipulated the traffic with the virtual tower and redirected the victim to a malicious website. What is the attack performed by Bobby in the above scenario?
In an attempt to damage the reputation of a competitor organization, Hailey, a professional hacker, gathers a list of employee and client email addresses and other related information by using various search engines, social networking sites, and web spidering tools. In this process, she also uses an automated tool to gather a list of words from the target website to further perform a brute-force attack on the previously gathered email addresses.
What is the tool used by Hailey for gathering a list of words from the target website?
Firewalls are the software or hardware systems that are able to control and monitor the traffic coming in and out the target network based on pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
If you send a TCP ACK segment to a known closed port on a firewall but it does not respond with an RST, what do you know about the firewall you are scanning?
A cyber adversary wants to enumerate firewall rules while minimizing noise and mimicking normal traffic behavior. Which reconnaissance technique enables mapping of firewall filtering behavior using TTL-manipulated packets?
Stella, a professional hacker, performs an attack on web services by exploiting a vulnerability that provides additional routing information in the SOAP header to support asynchronous communication. This further allows the transmission of web-service requests and response messages using different TCP connections. Which of the following attack techniques is used by Stella to compromise the web services?
Steve, a scientist who works in a governmental security agency, developed a technological solution to identify people based on walking patterns and implemented this approach to a physical control access.
A camera captures people walking and identifies the individuals using Steve’s approach.
After that, people must approximate their RFID badges. Both the identifications are required to open the door. In this case, we can say:
During a covert red team engagement, a penetration tester is tasked with identifying live hosts in a target organization’s internal subnet (10.0.0.0/24) without triggering intrusion detection systems (IDS). To remain undetected, the tester opts to use the command nmap -sn -PE 10.0.0.0/24, which results in several "Host is up" responses, even though the organization’s IDS is tuned to detect high-volume scans. After the engagement, the client reviews the logs and is surprised that the scan was not flagged. What allowed the scan to complete without triggering alerts?
What type of a vulnerability/attack is it when the malicious person forces the user’s browser to send an authenticated request to a server?
During LDAP-based enumeration, you observe that some critical information cannot be retrieved. What is the most likely reason?
Which of the following antennas is commonly used in communications for a frequency band of 10 MHz to VHF and UHF?
Robert, a professional hacker, is attempting to execute a fault injection attack on a target IoT device. In this process, he injects faults into the power supply that can be used for remote execution, also causing the skipping of key instructions. He also injects faults into the clock network used for delivering a synchronized signal across the chip.
Which of the following types of fault injection attack is performed by Robert in the above scenario?
A security researcher reviewing an organization's website source code finds references to Amazon S3 file locations. What is the most effective way to identify additional publicly accessible S3 bucket URLs used by the target?
Joseph was the Web site administrator for the Mason Insurance in New York, whose main website was located at Joseph uses his laptop computer regularly to administer the website. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance website had been vandalized! All of its normal content was removed and replaced with an attacker’s message:
“H@cker Mess@ge: Y0u @re De@d! Fre@ks!”
From his office network (internal), Joseph saw the normal site. But from an external DSL connection, users saw the defaced site. Joseph checked the web server with Tripwire and found no system file or content change.
How did the attacker accomplish this hack?
As an IT technician in a small software development company, you are responsible for protecting the network against various cyber threats. You learn that attackers often try to bypass firewalls. Which of the following is a common technique used by attackers to evade firewall detection?
To create a botnet. the attacker can use several techniques to scan vulnerable machines. The attacker first collects Information about a large number of vulnerable machines to create a list. Subsequently, they infect the machines. The list Is divided by assigning half of the list to the newly compromised machines. The scanning process runs simultaneously. This technique ensures the spreading and installation of malicious code in little time.
Which technique is discussed here?
You are analyzing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command would you use?
DHCP snooping is a great solution to prevent rogue DHCP servers on your network. Which security feature on switchers leverages the DHCP snooping database to help prevent man-in-the-middle attacks?
A major financial institution is experiencing persistent DoS attacks against online banking, disrupting transactions. Which sophisticated DoS technique poses the greatest challenge to detect and mitigate effectively, potentially jeopardizing service availability?
Dorian Is sending a digitally signed email to Polly, with which key is Dorian signing this message and how is Poly validating It?
What is the main security service a cryptographic hash provides?
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host
10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he
applied his ACL configuration in the router, nobody can access the ftp, and the permitted hosts cannot access
the Internet. According to the next configuration, what is happening in the network?
access-list 102 deny tcp any any
access-list 104 permit udp host 10.0.0.3 any
access-list 110 permit tcp host 10.0.0.2 eq www any
access-list 108 permit tcp any eq ftp any
Which best describes the role of a penetration tester?
Which Metasploit Framework tool can help penetration tester for evading Anti-virus Systems?
There have been concerns in your network that the wireless network component is not sufficiently secure. You perform a vulnerability scan of the wireless network and find that it is using an old encryption protocol that was designed to mimic wired encryption, what encryption protocol is being used?
Taylor, a security professional, uses a tool to monitor her company's website, analyze the website's traffic, and track the geographical location of the users visiting the company's website. Which of the following tools did Taylor employ in the above scenario?
John is an incident handler at a financial institution. His steps in a recent incident are not up to the standards of the company. John frequently forgets some steps and procedures while handling responses as they are very stressful to perform. Which of the following actions should John take to overcome this problem with the least administrative effort?
A penetration tester is evaluating a secure web application that uses HTTPS, secure cookie flags, and regenerates session IDs only during specific user actions. To hijack a legitimate user's session without triggering security alerts, which advanced session hijacking technique should the tester employ?
A penetration tester detects malware on a system that secretly records all keystrokes entered by the user. What type of malware is this?
A penetration tester identifies malware that monitors the activities of a user and secretly collects personal information, such as login credentials and browsing habits. What type of malware is this?
John, a disgruntled ex-employee of an organization, contacted a professional hacker to exploit the organization. In the attack process, the professional hacker Installed a scanner on a machine belonging to one of the vktims and scanned several machines on the same network to Identify vulnerabilities to perform further exploitation. What is the type of vulnerability assessment tool employed by John in the above scenario?
In the field of cryptanalysis, what is meant by a “rubber-hose" attack?
By performing a penetration test, you gained access under a user account. During the test, you established a connection with your own machine via the SMB service and occasionally entered your login and password in plaintext.
Which file do you have to clean to clear the password?
During a black-box penetration test, an attacker runs the following command:
nmap -p25 --script smtp-enum-users --script-args EXPN,RCPT
The script successfully returns multiple valid usernames. Which server misconfiguration is being exploited?
During security awareness training, which scenario best describes a tailgating social engineering attack?
These hackers have limited or no training and know how to use only basic techniques or tools. What kind of hackers are we talking about?
During the process of encryption and decryption, what keys are shared?
Working as an Information Security Analyst, you are creating training material on session hijacking. Which scenario best describes a side jacking attack?
While performing a SYN (half-open) scan using Nmap, you send a SYN packet to a target IP address and receive a SYN/ACK response. How should this result be interpreted?
You are a penetration tester and are about to perform a scan on a specific server. The agreement that you signed with the client contains the following specific condition for the scan: “The attacker must scan every port on the server several times using a set of spoofed sources IP addresses. ” Suppose that you are using Nmap to perform this scan. What flag will you use to satisfy this requirement?
jane invites her friends Alice and John over for a LAN party. Alice and John access Jane's wireless network without a password. However. Jane has a long, complex password on her router. What attack has likely occurred?
An attacker extracts the initial bytes from an encrypted file container and uses a tool to iterate through numeric combinations. What type of cryptanalytic technique is being utilized?
A penetration tester is assessing an IoT thermostat used in a smart home system. The device communicates with a cloud server for updates and commands. The tester discovers that communication between the device and the cloud server is not encrypted. What is the most effective way to exploit this vulnerability?
What useful information is gathered during a successful Simple Mail Transfer Protocol (SMTP) enumeration?
While analyzing logs, you observe a large number of TCP SYN packets sent to various ports with no corresponding ACKs. What scanning technique was likely used?
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
As a cybersecurity professional at XYZ Corporation, you are tasked with investigating anomalies in system logs that suggest potential unauthorized activity. System administrators have detected repeated failed login attempts on a critical server, followed by a sudden surge in outbound data traffic. These indicators suggest a possible compromise. Given the sensitive nature of the system and the sophistication of the threat, what should be your initial course of action?
John, a professional hacker, decided to use DNS to perform data exfiltration on a target network, in this process, he embedded malicious data into the DNS protocol packets that even DNSSEC cannot detect. Using this technique. John successfully injected malware to bypass a firewall and maintained communication with the victim machine and C&C server. What is the technique employed by John to bypass the firewall?
You are the chief cybersecurity officer at CloudSecure Inc., and your team is responsible for securing a cloudbased application that handles sensitive customer data. To ensure that the data is protected from breaches, you
have decided to implement encryption for both data-at-rest and data-in-transit. The development team suggests using SSL/TLS for securing data in transit. However, you want to also implement a mechanism to detect if the data was tampered with during transmission. Which of the following should you propose?
An IT security team is conducting an internal review of security protocols in their organization to identify
potential vulnerabilities. During their investigation, they encounter a suspicious program running on several
computers. Further examination reveals that the program has been logging all user keystrokes. How can the
security team confirm the type of program and what countermeasures should be taken to ensure the same
attack does not occur in the future?
Harry. a professional hacker, targets the IT infrastructure of an organization. After preparing for the attack, he attempts to enter the target network using techniques such as sending spear-phishing emails and exploiting vulnerabilities on publicly available servers. Using these techniques, he successfully deployed malware on the target system to establish an outbound connection. What is the APT lifecycle phase that Harry is currently executing?
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
This wireless security protocol allows 192-bit minimum-strength security protocols and cryptographic tools to protect sensitive data, such as GCMP-2S6. MMAC-SHA384, and ECDSA using a 384-bit elliptic curve. Which is this wireless security protocol?
You detect the presence of a kernel-level rootkit embedded deeply within an operating system. Given the critical nature of the infection, which remediation strategy should be followed to effectively remove the rootkit while minimizing long-term risk?
#!/usr/bin/python
import socket
buffer=["A"]
counter=50
while len(buffer)<=100:
buffer.append("A"*counter)
counter=counter+50
commands=["HELP","STATS","RTIME","LTIME","SRUN","TRUN","GMON","GDOG","KSTET","GTER","HTER","LTER","KSTAN"]
for command in commands:
for buffstring in buffer:
print "Exploiting " + command + ": " + str(len(buffstring))
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('127.0.0.1', 9999))
s.recv(50)
s.send(command + buffstring)
s.close()
What is the code written for?
During the enumeration phase. Lawrence performs banner grabbing to obtain information such as OS details and versions of services running. The service that he enumerated runs directly on TCP port 445.
Which of the following services is enumerated by Lawrence in this scenario?
Ben purchased a new smartphone and received some updates on it through the OTA method. He received two messages: one with a PIN from the network operator and another asking him to enter the PIN received from the operator. As soon as he entered the PIN, the smartphone started functioning in an abnormal manner.
What is the type of attack performed on Ben in the above scenario?
What is the most plausible attack vector an APT group would use to compromise an IoT-based environmental control system?
Attackers persisted by modifying legitimate system utilities and services. What key step helps prevent similar threats?
A security analyst uses Zenmap to perform an ICMP timestamp ping scan to acquire information related to the current time from the target host machine.
Which of the following Zenmap options must the analyst use to perform the ICMP timestamp ping scan?
Which advanced evasion technique poses the greatest challenge to detect and mitigate?
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist’s email, and you send her an email changing the source email to her boss’s email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network. What testing method did you use?
What two conditions must a digital signature meet?
A penetration tester evaluates a company's susceptibility to advanced social engineering attacks targeting its executive team. Using detailed knowledge of recent financial audits and ongoing projects, the tester crafts a highly credible pretext to deceive executives into revealing their network credentials. What is the most effective social engineering technique the tester should employ to obtain the necessary credentials without raising suspicion?
A system analyst wants to implement an encryption solution that allows secure key distribution between communicating parties. Which encryption method should the analyst consider?
Your network infrastructure is under a SYN flood attack. The attacker has crafted an automated botnet to
simultaneously send 's' SYN packets per second to the server. You have put measures in place to manage ‘f
SYN packets per second, and the system is designed to deal with this number without any performance issues.
If 's' exceeds ‘f', the network infrastructure begins to show signs of overload. The system's response time
increases exponentially (24k), where 'k' represents each additional SYN packet above the ff limit. Now, considering 's=500' and different 'f values, in which scenario is the server most likely to experience overload and significantly increased response times?
A penetration tester is tasked with assessing the security of an Android mobile application that stores sensitive user data. The tester finds that the application does not use proper encryption to secure data at rest. What is the most effective way to exploit this vulnerability?
Which of the following statements about a zone transfer is correct? (Choose three.)
Daniel Is a professional hacker who Is attempting to perform an SQL injection attack on a target website. During this process, he encountered an IDS that detects SQL Injection attempts based on predefined signatures. To evade any comparison statement, he attempted placing characters such as ‘ 'or '1'='1" In any bask injection statement such as "or 1=1." Identify the evasion technique used by Daniel in the above scenario.
Which algorithm best protects encrypted traffic patterns?
During a security assessment of a cloud-hosted application using SOAP-based web services, a red team operator intercepts a valid SOAP request, duplicates the signed message body, inserts it into the same envelope, and forwards it. Due to improper validation, the server accepts the duplicated body and executes unauthorized code. What type of attack does this represent?
A malware analyst finds JavaScript and /OpenAction keywords in a suspicious PDF using pdfid. What should be the next step to assess the potential impact?
Johnson, an attacker, performed online research for the contact details of reputed cybersecurity firms. He found the contact number of sibertech.org and dialed the number, claiming himself to represent a technical support team from a vendor. He warned that a specific server is about to be compromised and requested sibertech.org to follow the provided instructions. Consequently, he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical Information to Johnson's machine. What is the social engineering technique Steve employed in the above scenario?
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet 10.1.4.0/23. Which of the following IP addresses could be leased as a result of the new configuration?
What does the –oX flag do in an Nmap scan?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
Mike, a security engineer, was recently hired by BigFox Ltd. The company recently experienced disastrous DoS attacks. The management had instructed Mike to build defensive strategies for the company's IT infrastructure to thwart DoS/DDoS attacks. Mike deployed some countermeasures to handle jamming and scrambling attacks. What is the countermeasure Mike applied to defend against jamming and scrambling attacks?
Richard, an attacker, targets an MNC. In this process, he uses a footprinting technique to gather as much information as possible. Using this technique, he gathers domain information such as the target domain name, contact details of its owner, expiry date, and creation date. With this information, he creates a map of the organization's network and misleads domain owners with social engineering to obtain internal details of its network.
What type of footprinting technique is employed by Richard?
An Internet Service Provider (ISP) has a need to authenticate users connecting via analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network.
Which AAA protocol is the most likely able to handle this requirement?
A penetration tester suspects that the web application's "Order History" page is vulnerable to SQL injection because it displays user orders based on an unprotected user ID parameter in the URL. What is the most appropriate approach to test this?
Kevin, a professional hacker, wants to penetrate CyberTech Inc.’s network. He employed a technique, using which he encoded packets with Unicode characters. The company’s IDS cannot recognize the packet, but the target web server can decode them.
What is the technique used by Kevin to evade the IDS system?
Eric, a cloud security engineer, implements a technique for securing the cloud resources used by his organization. This technique assumes by default that a user attempting to access the network is not an authentic entity and verifies every incoming connection before allowing access to the network. Using this technique, he also imposed conditions such that employees can access only the resources required for their role.
What is the technique employed by Eric to secure cloud resources?
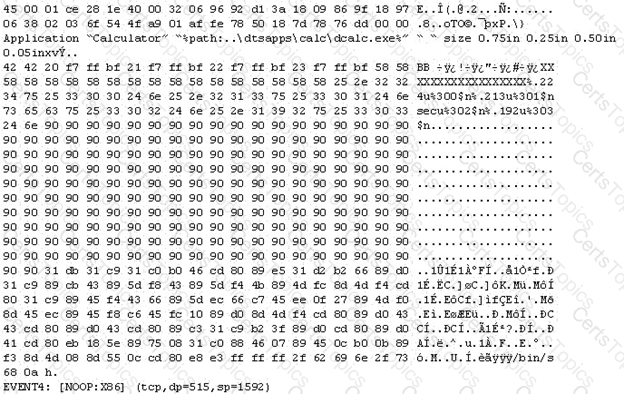
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry.
You notice the value 0x90, which is the most common NOOP instruction for the Intel processor.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst, what would you conclude about the attack?
What is the minimum number of network connections in a multihomed firewall?
In ethical hacking, what is black box testing?
Sophia is a shopping enthusiast who spends significant time searching for trendy outfits online. Clark, an attacker, noticed her activities several times and sent a fake email containing a deceptive page link to her social media page displaying all-new and trendy outfits. In excitement, Sophia clicked on the malicious link and logged in to that page using her valid credentials. Which of the following tools is employed by Clark to create the spoofed email?
Upon establishing his new startup, Tom hired a cloud service provider (CSP) but was dissatisfied with their service and wanted to move to another CSP.
What part of the contract might prevent him from doing so?
Within the context of Computer Security, which of the following statements describes Social Engineering best?
A government agency trains a group of cybersecurity experts to carry out covert cyber missions against foreign threats and gather intelligence without being detected. These experts work exclusively for national interests. What classification best describes them?
A penetration tester evaluates a secure web application using HTTPS, secure cookies, and multi-factor authentication. To hijack a legitimate user’s session without triggering alerts, which technique should be used?
What is the following command used for?
sqlmap.py -u " &forumaction=search" -dbs
Alice, a professional hacker, targeted an organization's cloud services. She infiltrated the targets MSP provider by sending spear-phishing emails and distributed custom-made malware to compromise user accounts and gain remote access to the cloud service. Further, she accessed the target customer profiles with her MSP account, compressed the customer data, and stored them in the MSP. Then, she used this information to launch further attacks on the target organization. Which of the following cloud attacks did Alice perform in the above scenario?
During a physical penetration test simulating a social engineering attack, a threat actor walks into the lobby of a target organization dressed as a field technician from a known external vendor. Carrying a fake ID badge and referencing a known company name, the attacker confidently claims they’ve been dispatched to perform a routine server room upgrade. Using internal-sounding terminology and referencing real employee names gathered via OSINT, the individual conveys urgency. The receptionist, recognizing the vendor name and the convincing language, allows access without verifying the credentials.
A large enterprise has been experiencing sporadic system crashes and instability, resulting in limited access to its web services. The security team suspects it could be a result of a Denial of Service (DoS) attack. A significant increase in traffic was noticed in the network logs, with patterns suggesting packet sizes exceeding the prescribed size limit. Which among the following DoS attack techniques best describes this scenario?
During an IDS audit, you notice numerous alerts triggered by legitimate user activity. What is the most likely cause?
A zone file consists of which of the following Resource Records (RRs)?
A web server was compromised through DNS hijacking. What would most effectively prevent this in the future?
A penetration tester is running a vulnerability scan on a company’s network. The scan identifies an open port with a high-severity vulnerability linked to outdated software. What is the most appropriate next step for the tester?
An ethical hacker needs to gather sensitive information about a company's internal network without engaging directly with the organization's systems to avoid detection. Which method should be employed to obtain this information discreetly?
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and keyloggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients’ hosts and servers?
joe works as an it administrator in an organization and has recently set up a cloud computing service for the organization. To implement this service, he reached out to a telecom company for providing Internet connectivity and transport services between the organization and the cloud service provider, in the NIST cloud deployment reference architecture, under which category does the telecom company fall in the above scenario?
Which of the following web vulnerabilities would an attacker be attempting to exploit if they delivered the following input?
A penetration tester is mapping a Windows-based internal network. The tester notices that TCP port 139 and UDP port 137 are open on multiple systems. File and printer sharing is enabled. To retrieve hostnames, user details, and domain roles without triggering alerts, which tool and method would be most effective?
A penetration tester is assessing a company's HR department for vulnerability to social engineering attacks using knowledge of recruitment and onboarding processes. What is the most effective technique to obtain network access credentials without raising suspicion?
Email is transmitted across the Internet using the Simple Mail Transport Protocol. SMTP does not encrypt email, leaving the information in the message vulnerable to being read by an unauthorized person. SMTP can upgrade a connection between two mail servers to use TLS. Email transmitted by SMTP over TLS is encrypted. What is the name of the command used by SMTP to transmit email over TLS?
As a Certified Ethical Hacker evaluating a smart city project (traffic lights, public Wi-Fi, and water management), you find anomalous IoT network logs showing high-volume data exchange between a specific traffic light and an external IP address. Further investigation reveals an unexpectedly open port on that traffic light. What should be your subsequent course of action?
A hacker has successfully infected an internet-facing server which he will then use to send junk mail, take part in coordinated attacks, or host junk email content. Which sort of trojan infects this server?
Which scenario best represents a social engineering attack?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
A penetration tester completes a vulnerability scan showing multiple low-risk findings and one high-risk vulnerability tied to outdated server software. What should the tester prioritize as the next step?
Why are containers less secure than virtual machines?
Jane is working as a security professional at CyberSol Inc. She was tasked with ensuring the authentication and integrity of messages being transmitted in the corporate network. To encrypt the messages, she implemented a security model in which every user in the network maintains a ring of public keys. In this model, a user needs to encrypt a message using the receiver's public key, and only the receiver can decrypt the message using their private key. What is the security model implemented by Jane to secure corporate messages?
What is the purpose of a demilitarized zone on a network?
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, small sized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two. What would you call this attack?
Which encryption method supports secure key distribution?
Study the Snort rule given below:
[Image shows two Snort rules with alert messages for NETBIOS DCERPC ISystemActivator bind attempt, targeting TCP ports 135 and 445. References include CVE: CAN-2003-0352.]
An ethical hacker is testing a web application of a financial firm. During the test, a 'Contact Us' form's input field is found to lack proper user input validation, indicating a potential Cross-Site Scripting (XSS) vulnerability. However, the application has a stringent Content Security Policy (CSP) disallowing inline scripts and scripts from external domains but permitting scripts from its own domain. What would be the hacker's next step to confirm the XSS vulnerability?
Which of the following is a component of a risk assessment?
You are a cybersecurity consultant for a global organization. The organization has adopted a Bring Your Own Device (BYOD)policy, but they have recently experienced a phishing incident where an employee's device was compromised. In the investigation, you discovered that the phishing attack occurred through a third-party email app that the employee had installed. Given the need to balance security and user autonomy under the BYOD policy, how should the organization mitigate the risk of such incidents? Moreover, consider a measure that would prevent similar attacks without overly restricting the use of personal devices.
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, DELETE, PUT, TRACE) using NMAP script engine. What Nmap script will help you with this task?
During network analysis, clients are receiving incorrect gateway and DNS settings due to a rogue DHCP server. What security feature should the administrator enable to prevent this in the future?
A vulnerability has a score of 9.8. What does this rating help explain?
You are an ethical hacker tasked with conducting an enumeration of a company’s network. Given a Windows system with NetBIOS enabled, port 139 open, and file and printer sharing active, you are about to run some nbtstat commands to enumerate NetBIOS names. The company uses |Pv6 for its network. Which of the
following actions should you take next?
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
How is the public key distributed in an orderly, controlled fashion so that the users can be sure of the sender’s identity?
A corporation migrates to a public cloud service, and the security team identifies a critical vulnerability in the cloud provider’s API. What is the most likely threat arising from this flaw?
Garry is a network administrator in an organization. He uses SNMP to manage networked devices from a remote location. To manage nodes in the network, he uses MIB. which contains formal descriptions of all network objects managed by SNMP. He accesses the contents of MIB by using a web browser either by entering the IP address and Lseries.mlb or by entering the DNS library name and Lseries.mlb. He is currently retrieving information from an MIB that contains object types for workstations and server services. Which of the following types of MIB is accessed by Garry in the above scenario?
During a penetration test, you perform extensive DNS interrogation to gather intelligence about a target organization. Considering the inherent limitations of DNS-based reconnaissance, which of the following pieces of information cannot be directly obtained through DNS interrogation?
Shiela is an information security analyst working at HiTech Security Solutions. She is performing service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
As part of a college project, you have set up a web server for hosting your team's application. Given your interest in cybersecurity, you have taken the lead in securing the server. You are aware that hackers often attempt to exploit server misconfigurations. Which of the following actions would best protect your web server from potential misconfiguration-based attacks?