A SOC analyst received an alert about a potential compromise and is reviewing the following SIEM logs:
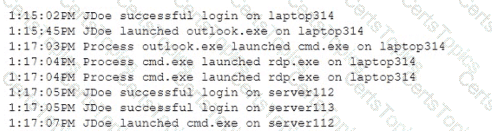
Which of the following is the most appropriate action for the SOC analyst to recommend?
A new VM server (Web Server C) was spun up in the cloud and added to the load balancer to an existing web application (Application A) that does not require internet access. Sales users arereporting intermittent issues with this application when processing orders that require access to the warehouse department.
Given the following information:
Firewall rules: Existing rules do not account for Web Server C’s IP address (10.2.0.92).
Application A Security Group: Inbound rules and outbound rules are insufficient for the new server.
The security team wants to minimize the firewall rule set by avoiding specific host rules whenever possible. Which of the following actions must be taken to resolve the issue and meet the security team's requirements?
A junior security researcher has identified a buffer overflow vulnerability leading to remote code execution in a former employer's software. The security researcher asks for the manager's advice on the vulnerability submission process. Which of the following is the best advice the current manager can provide the security researcher?
A software developer must choose encryption algorithms to secure two parts of a mobile application. Given the following part descriptions and requirements:
•The first part of the application is used to transfer large files and must support file parts with transfer start/stop/resume. This part requires strong file encryption.
•The second part of the application uses a bit stream to continuously authenticate both ends of the connection. This part must implement confidentiality for the stream.
Which of the following encryption algorithms should the developer implement in the code to support both parts of the application? (Select two).