A company recently deployed a SIEM and began importing logs from a firewall, a file server, a domain controller a web server, and a laptop. A security analyst receives a series of SIEM alerts and prepares to respond. The following is the alert information:
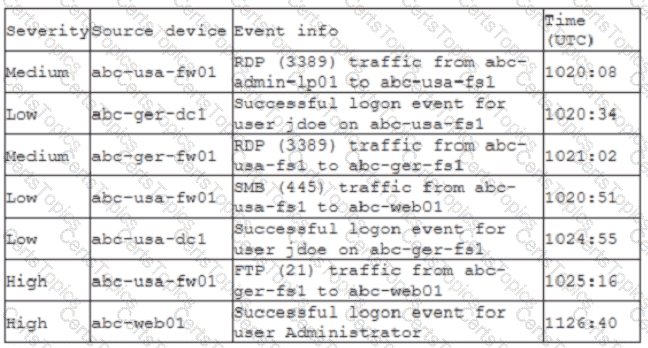
Which of the following should the security analyst do FIRST?
A technology company developed an in-house chat application that is used only by developers. An open-source library within the application has been deprecated. The facts below are provided:
•The cost of replacing this system is nominal.
•The system provides no revenue to the business.
•The system is not a critical part of the business.
Which of the following is the best risk mitigation strategy?
A company uses a CSP to provide a front end for its new payment system offering. The new offering is currently certified as PCI compliant. In order for the integrated solution to be
compliant, the customer:
A common industrial protocol has the following characteristics:
• Provides for no authentication/security
• Is often implemented in a client/server relationship
• Is implemented as either RTU or TCP/IP
Which of the following is being described?