What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
Which statement about authentication a RESTCONF API session with a router that runs Cisco IOS XE software is true?
What are two security benefits of a Docker-based application?
Which two statements describe the advantages of using a version control system? (Choose two.)
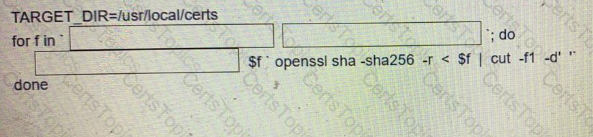
Fill in the blanks to complete the Bash script in which each file in a directory is renamed to Its SHA256 hash?
A Company is looking for cloud deployment which will use the on-premise infrastructure, is user self-service, and easy to scale. Which cloud solution should be selected for these requirements?
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
Refer to the exhibit.
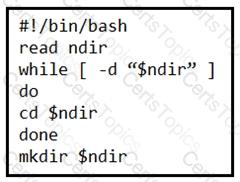
What is the action of the Bash script that is shown?
Refer to the exhibit.
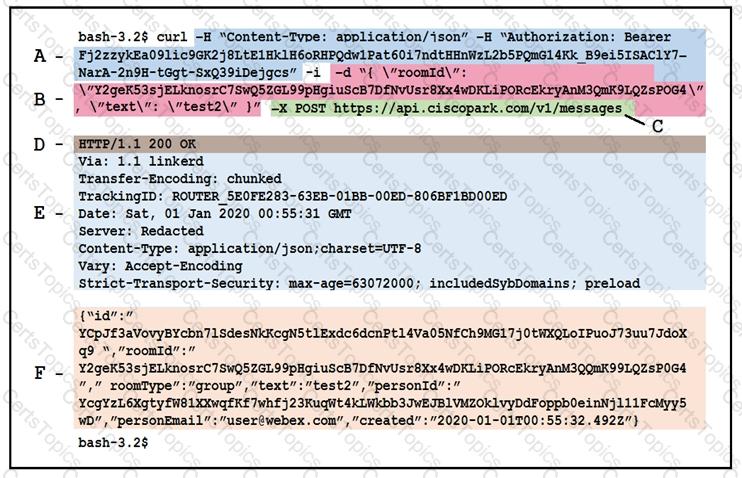
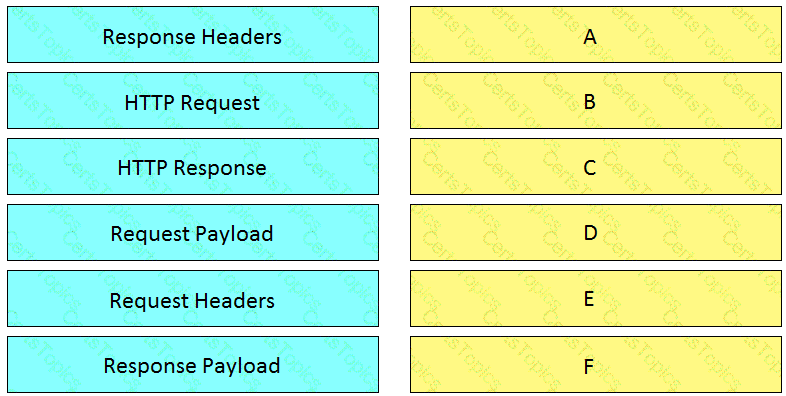
Drag and drop the descriptors from the left onto the correct parts of the API request and response on the right.
Refer to the exhibit.
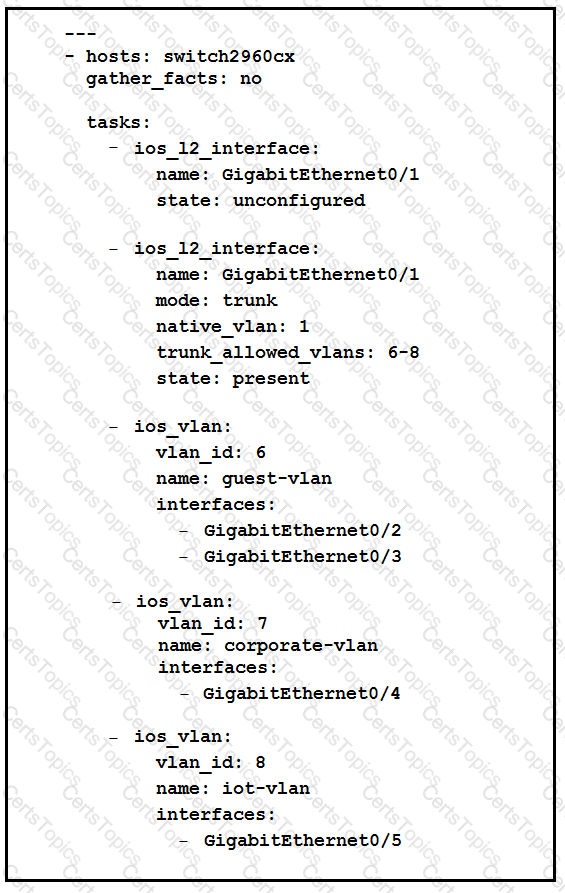
Which two statement describe the configuration of the Ansible script is run? (Choose two.)
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve statement using RESTCONF on a CSR 1000V?
Users cannot access a webserver and after the traffic is captured, the capture too* shows an ICMP packet that reports "communication administratively prohibited" What Is the cause of this webserver access Issue?
What is the benefit of edge computing?
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device mut be at fault?
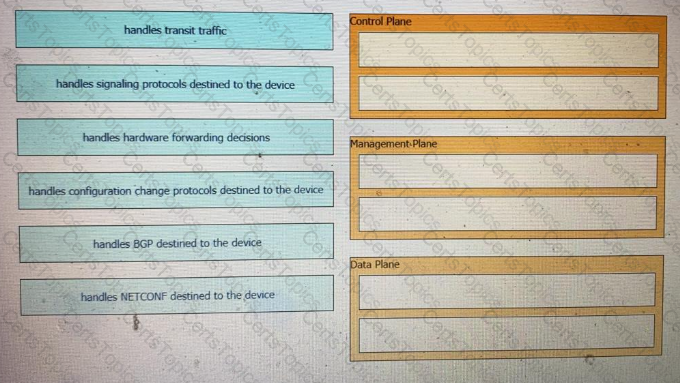
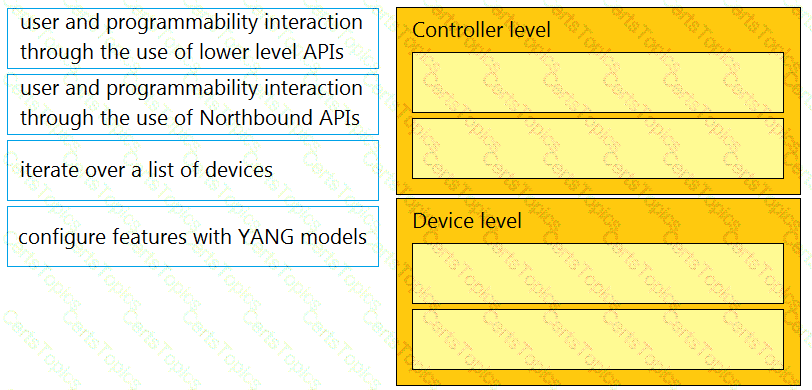
Drag and drop the function on the left onto the type of plane that handles the function on the right.
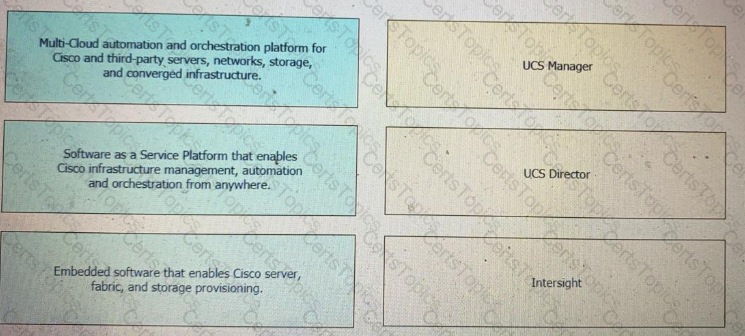
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right.
Which type of threat occur when an attacker can send hostile data to an interpreter within an application?
A developer is writing an application that a REST API and the application requires a valid from the API which element of the response is used in the conditional check?
On which network plane is routing protocol traffic handled?
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
Refer to the exhibit.
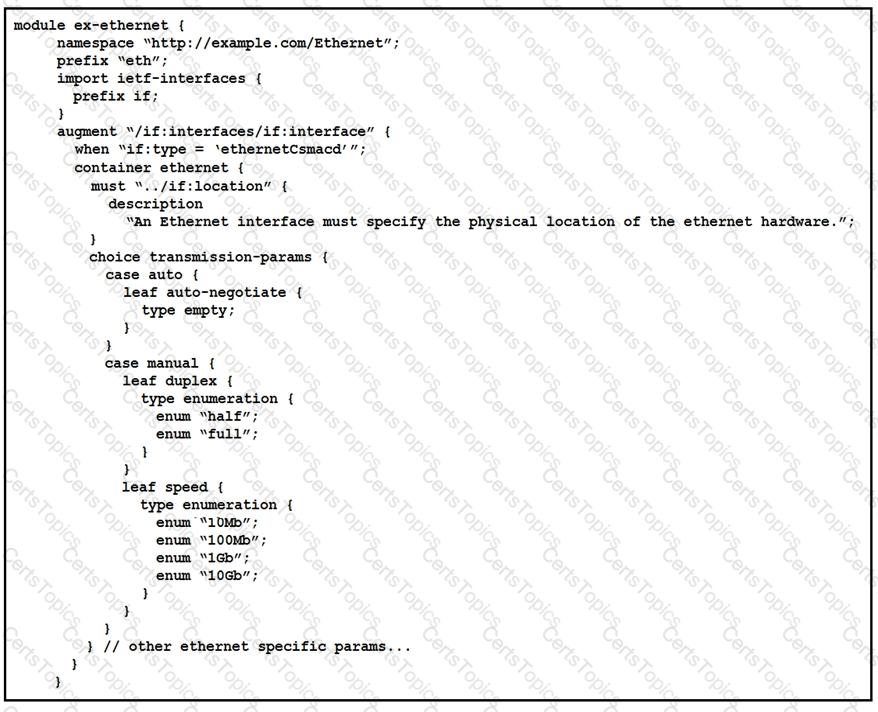
What is represented in this YANG module?
Which description of a default gateway if true?
Refer to the exhibit.
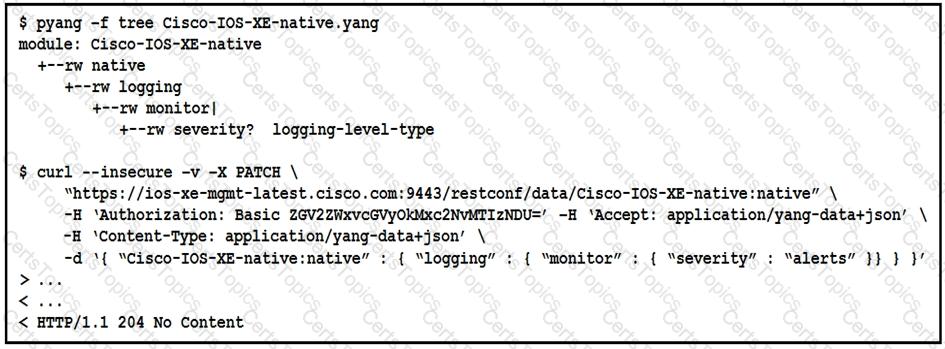
The definition of the YANG module and a RESTCONF query sent to a Cisco IOc XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
A 401 HTTP response code is returned when calling a REST API. What is the error state identified by this response code?
Refer to the exhibit.

A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called “vegetables” Using python, which output is the result of this command?

An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API?
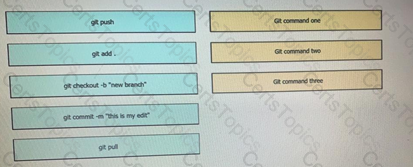
Drag and Drop the GIT commands from the left onto the right that add modified local files to a remote repository. Not all options are used
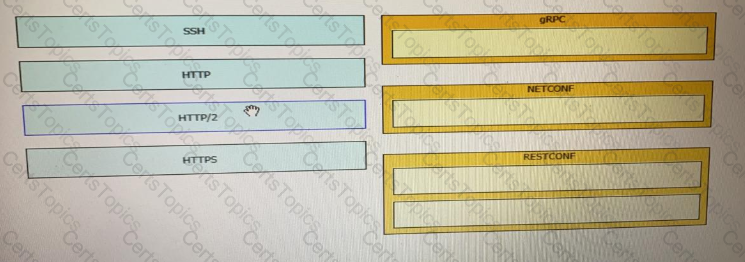
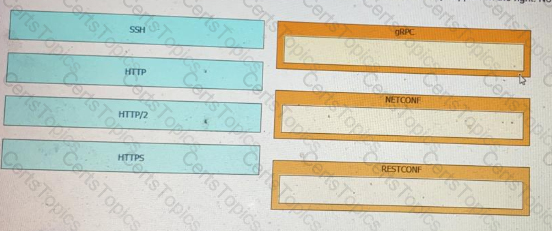
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right.
Which two types of NAT are used in a network? (Choose two.)
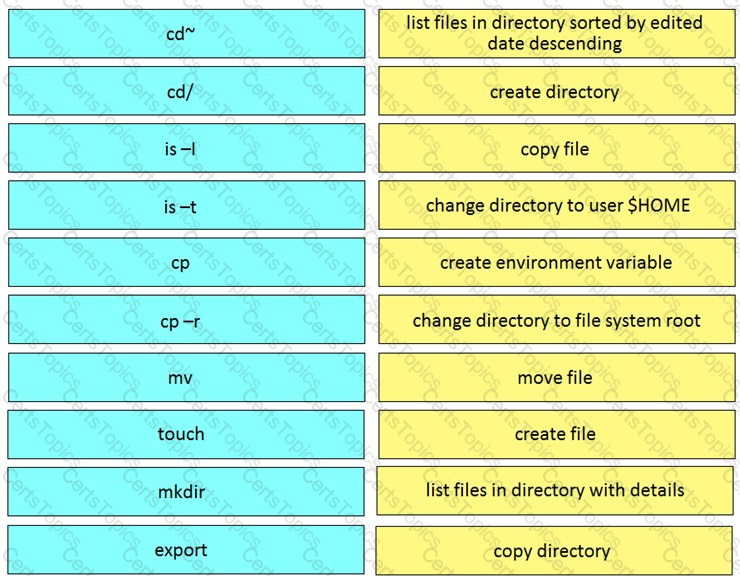
Drag and Drop the Bash commands from the left onto the correct actions on the right.
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
Which platform is run directly using a hypervisor?
What is the Git command to delete a local branch named “experiment” without a warning?
Which principle is a value from the manifesto for Agile software development?
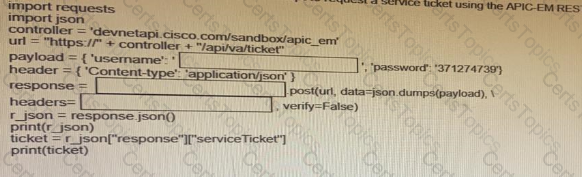
Fill in the blanks to complete the python script to request a service ticket using the APIC-EM rest API for the user “devnetuser”.
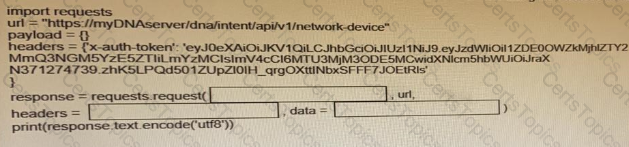
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
Refer to the exhibit.
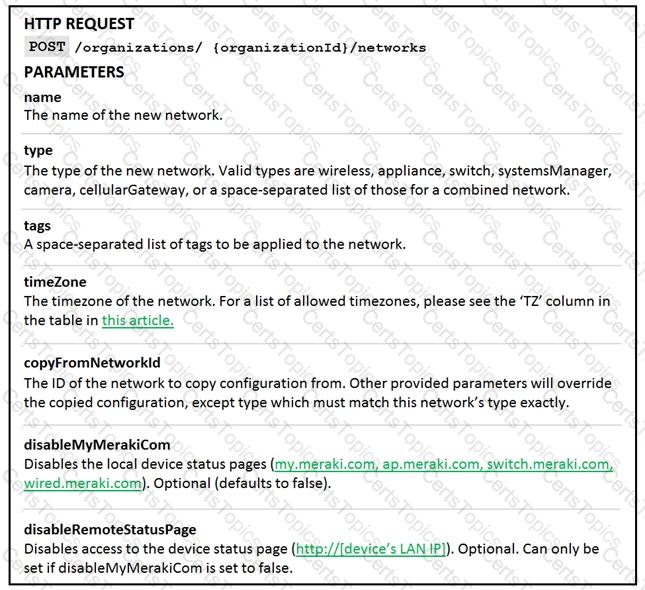
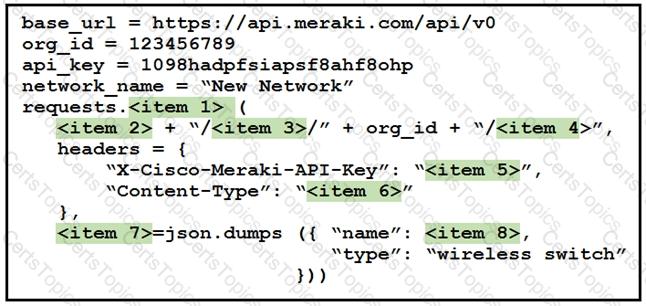
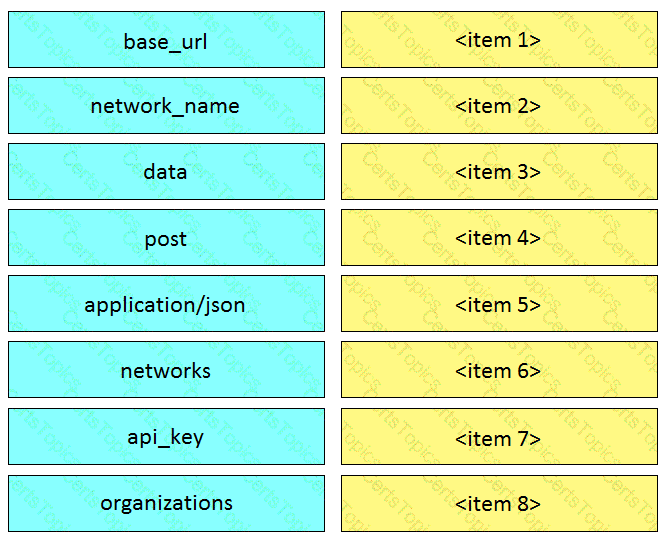
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
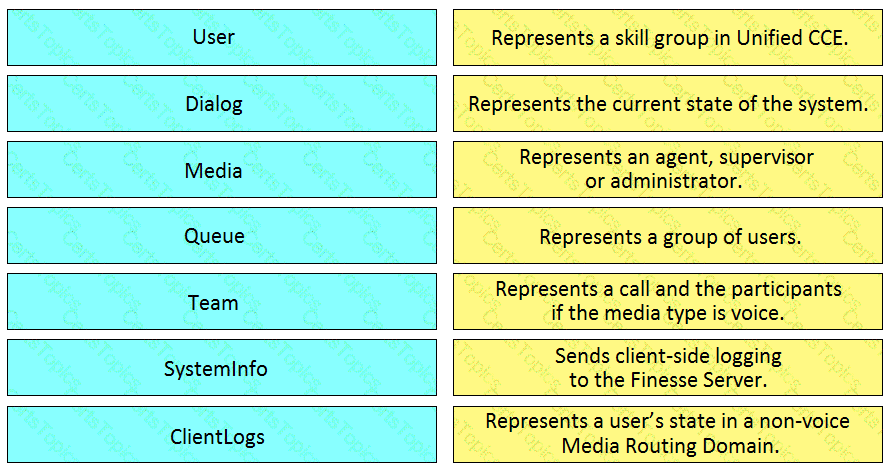
Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
Fill in the blanks to complete the statement.
Given a username of “devnet” And a password “Cisco123”, applications must create a base64 encoding of the string” ____________ ” when sanding HTTP requests to an API that uses _______________ authentication.
Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.)
Refer to Exhibit.
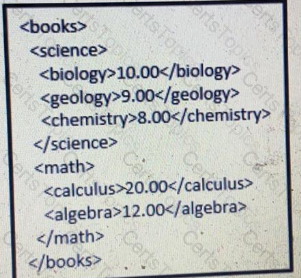
Which JSON is equivalent to the XML-encoded data.
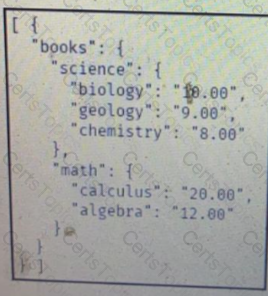
A)

B)
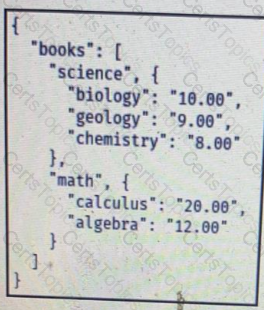
C)
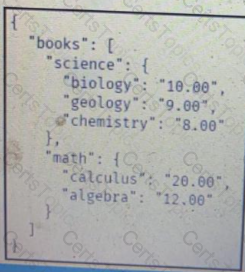
D)
Package updates from a local server fail to download. However, the same updates work when a much slower external repository is used. Way are local updates failing?
Fill in the blanks to complete the statement.
Cisco DNA provide the capability to send an HTTP _______________ request to the API endpoint and receive the network __________ list in __________ format.
Which two statements about JSON and XML are true? (Choose two.)
Which product provides network controller-level management features?
Which two statements describe the traits of an asynchronous API call? (Choose two.)
Refer to the exhibit.
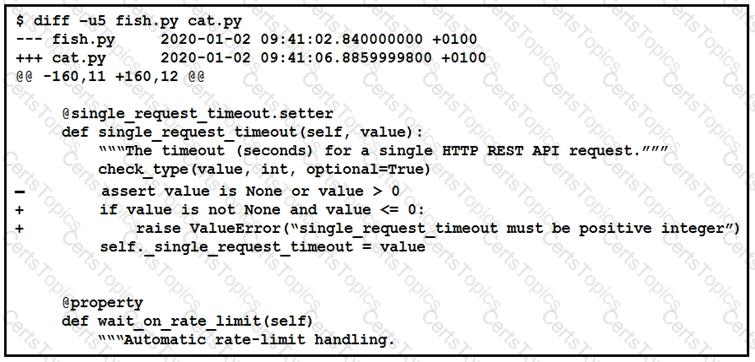
The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”

While developing a real-Time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
What is a functionality of the Waterfall method as compared to the Agile method for software development?
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as “latest”. Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
Which platform is used to programmatically create a space and invite users for collaboration?
Which HTTP code group is issued when a request is received successfully, understood, and processed?
Refer to the exhibit.
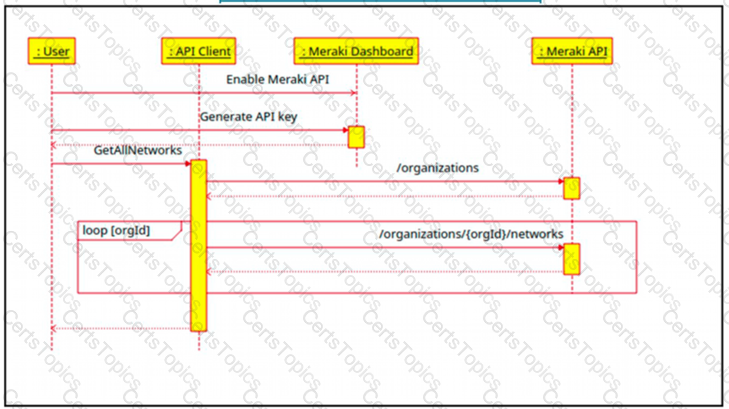
The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the /organizations/(orgid)networks endpoint will be run parallel by the GetAllNetwork function of the API client?
Refer to the exhibit.
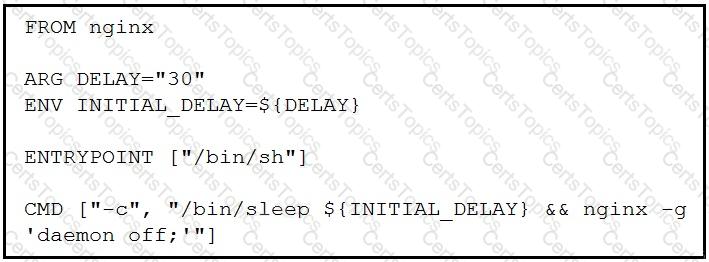
Which command, including arguments, is executed when the container starts?
What is a capability of the NETCONF protocol?
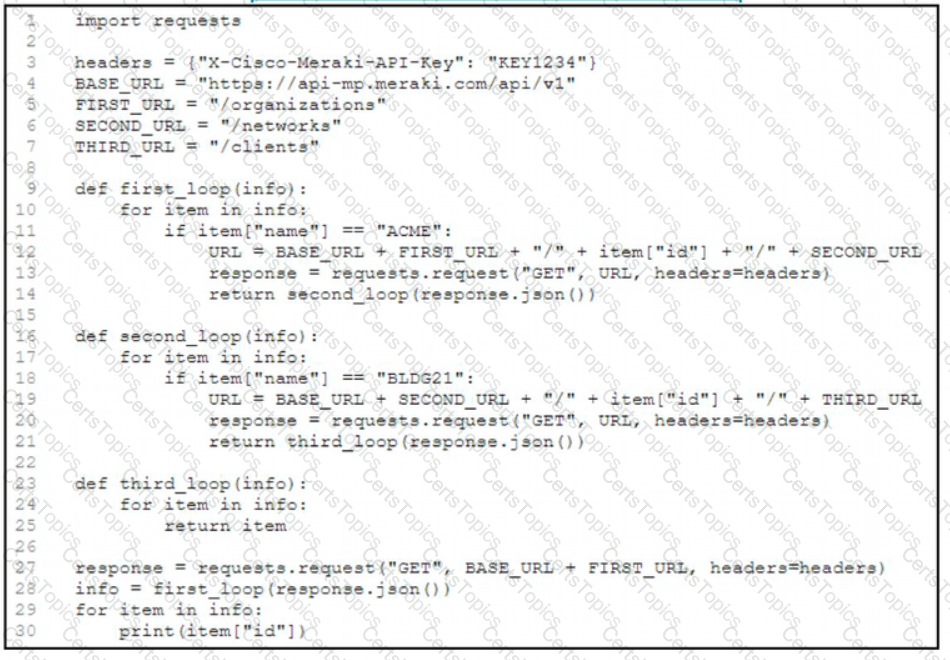
Refer to the exhibit. A network engineer must collect information from the network. The engineer prepares a script to automate workflow by using Cisco Meraki API. The script must run over nested loops to collect organization and network information and uses the collected data for final collection. Which process is being automated by using the Python script?
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command:
$ docker tag 84fe411926287 local/app:0.4
Which command must be executed next to build the Docker image using the tag?
Refer to the exhibit.
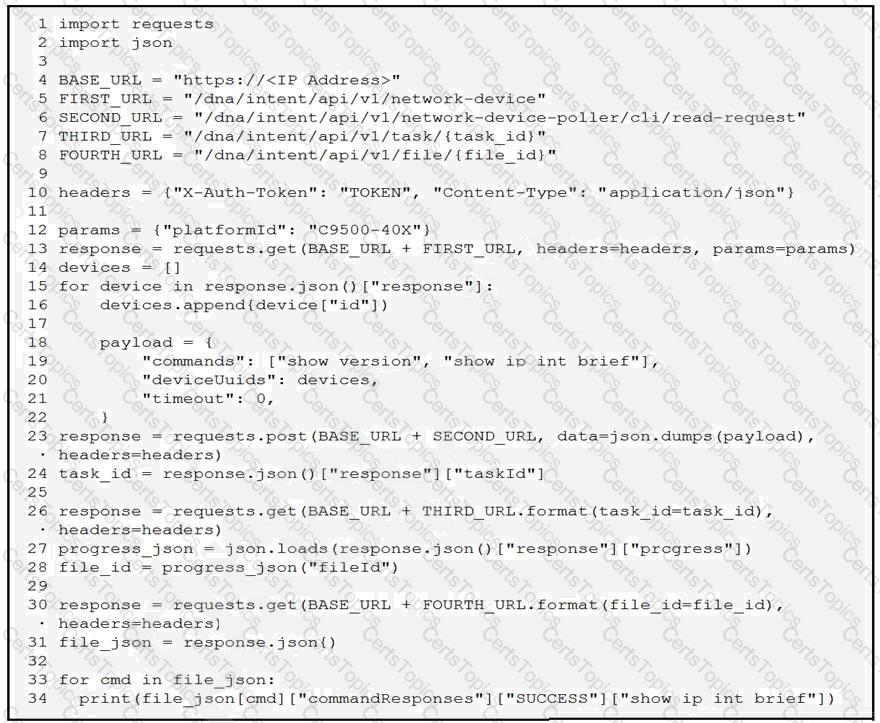
A network engineer must collect information from the network using Cisco DNA Center APIs. The script must query for the devices with 'platformId' 'C9540-x' and then send commands to be executed. Which process is automated by the Python script?
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
Refer to the exhibit.

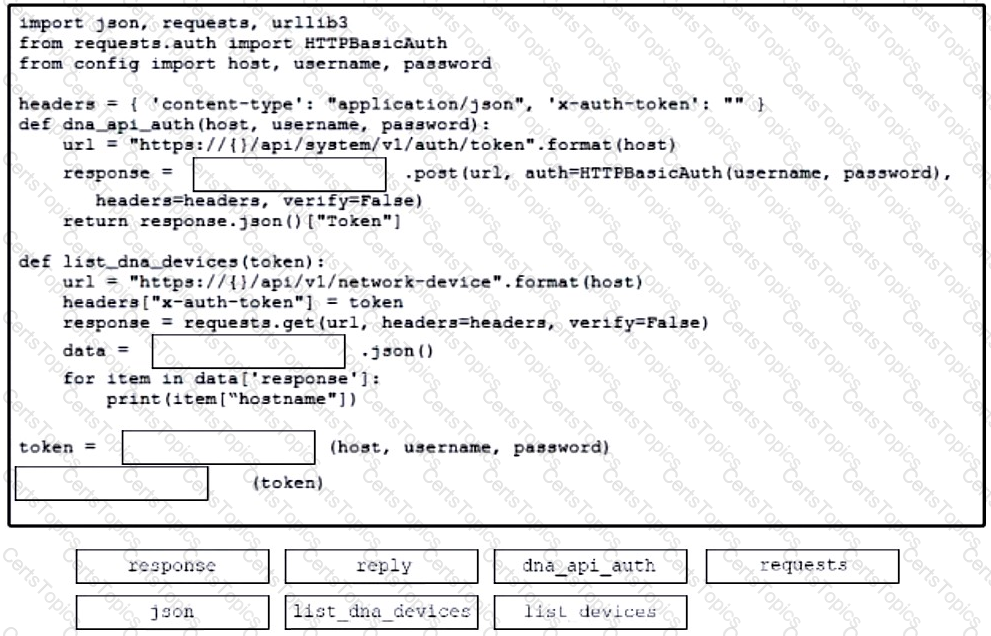
A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
Refer to the exhibit.
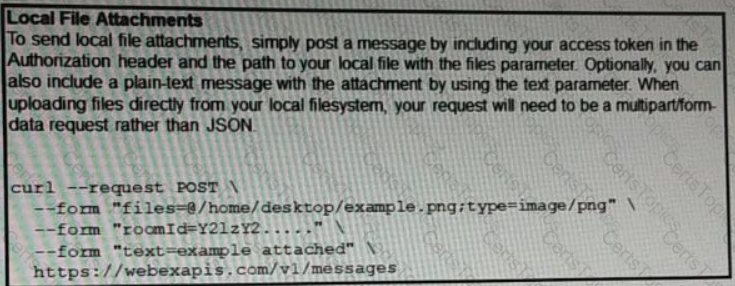
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
What is the purpose of a MAC address on a network device?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
How does a synchronous API request differ from an asynchronous API request?
In the test-driven development model, what is changed after a test fails?
Refer to the exhibit.
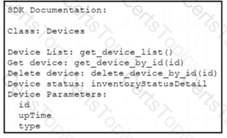
A Python script must delete all Cisco Catayst 9300 Series switches that have an uptime that is greater than 90 days The script must also query for the status of all the other devices Drag and drop the code from the bottom onto the bottom box the code is missing to complete the script Not at options are used

In test-driven development, what are two of the green bar patterns? (Choose two.)
What are two functions of a routing table on a network device? (Choose two.)
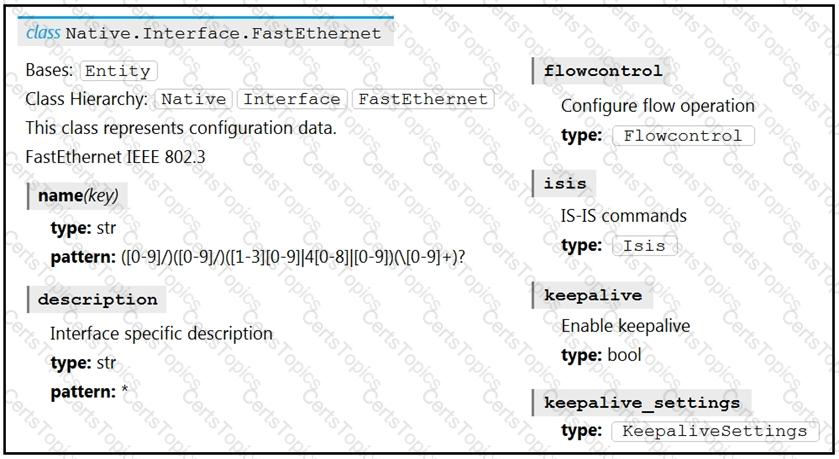
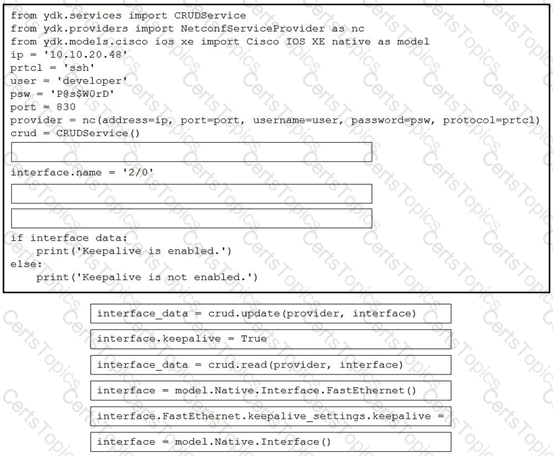
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request?
A company is adopting DevOps as part of an internal transformation, and is reviewing the success of the first deployments. Developers and engineers are working together to resolve any resulting issues. However, this new way of working has increased overhead, and the team is finding it difficult to complete releases in time.
Which area of the CALMS framework must the company target for improvement?
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
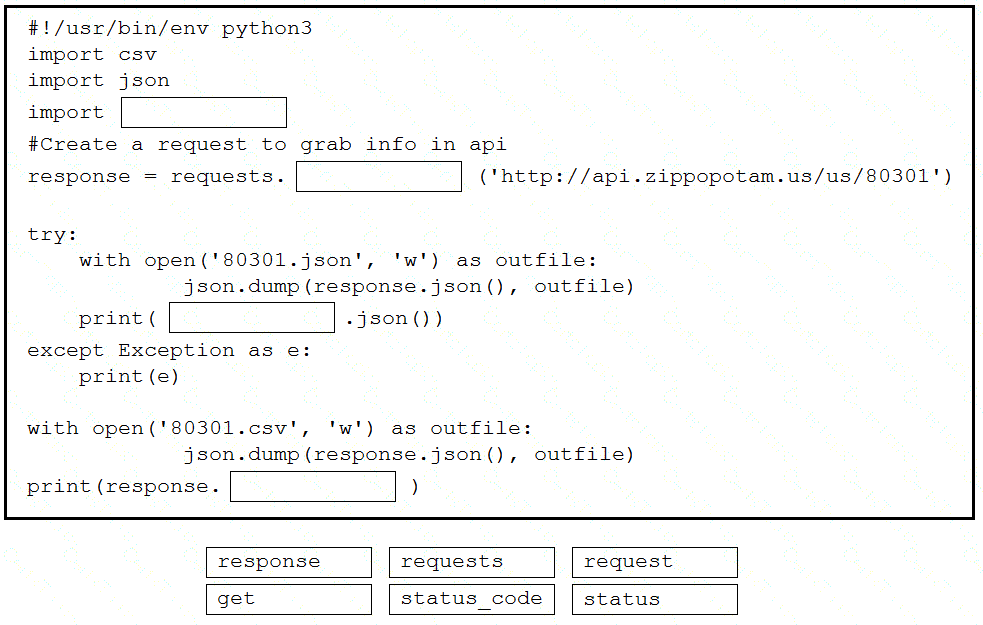
Refer to the exhibit.

A developer must integrate a bot with an internal communication app. The developer wants to replace the webexbot package with the teamsbot package by using Ansible and prepares a playbook In the first two tasks, the playbook stops the webexbot and verifies that the teamsbot is installed. What is accomplished in the last task of the workflow when the developer runs the Ansible playbook?
A company wants to accelerate the adoption of technologies that will simplify its operations. Staff have different skill levels and are looking for a single site to find easy-to-consume beginner, intermediate, and advanced multidomain use cases. Which site should be used?
Refer to the exhibit.
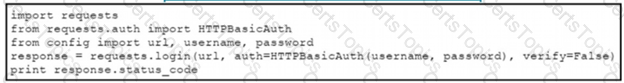
The script returns an output of 401. To use the supplied URL. an HTTP GET request must Be sent with an Authorization header. The header value is a BaseG4 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
In which two ways is an application characterized when interacting with a webhook? (Choose two.)
Refer to the exhibit.

An engineer must configure a load balancer server. The engineer prepares a script to automate workflow by using Bash. The script install the nginx package, moves to the /optAtginx directory, and reads the sites M We (or further processing Based on the script workflow, which process is being automated within the loop by using the information mi sites txt?
Refer to the exhibit.
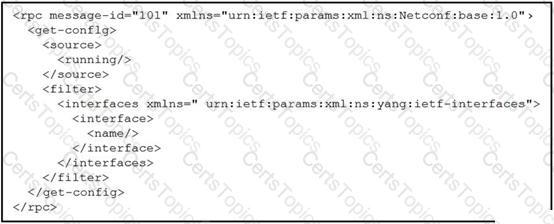
A network engineer uses model-driven programmability to monitor and perform changes on the network. The network engineer decides to use the NETCONF RPC message to complete one of their tasks. What is accomplished by sending the RPC message?
Which HTTP response status code means “Forbidden”?
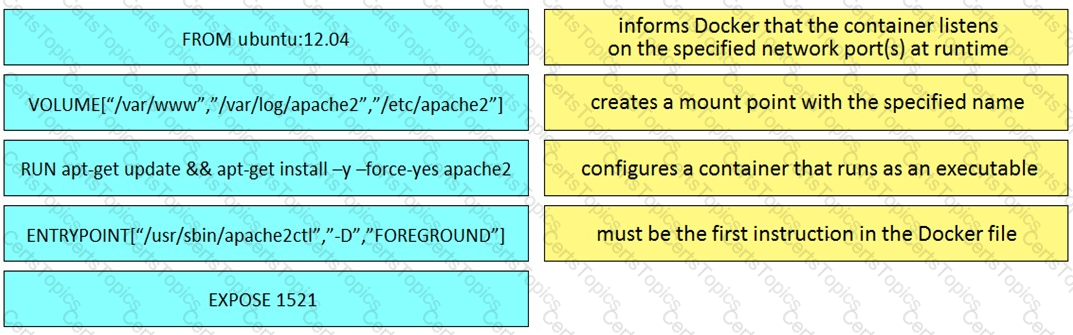
Drag and drop the Dockerfile instructions from the left onto the descriptions on the right. Not at options are used.
Refer to the exhibit.
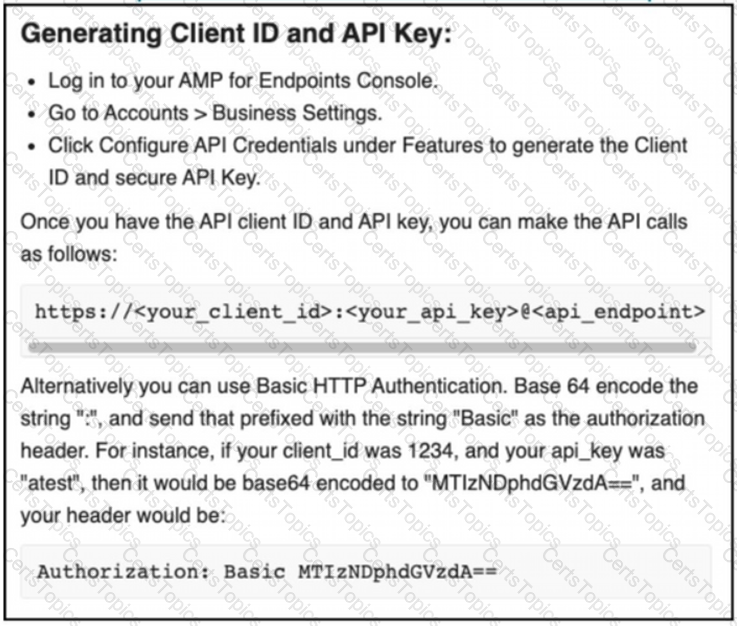
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
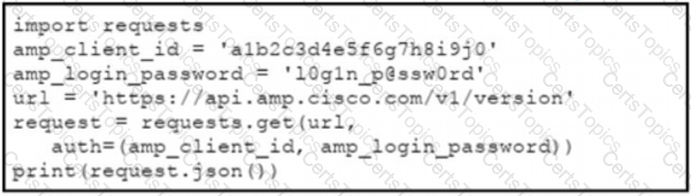
B)
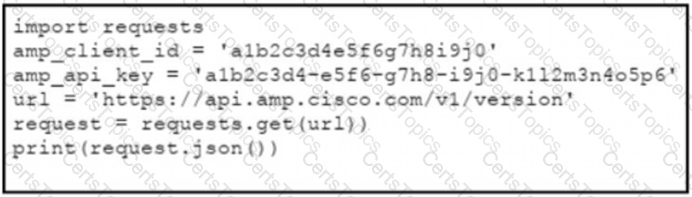
C)
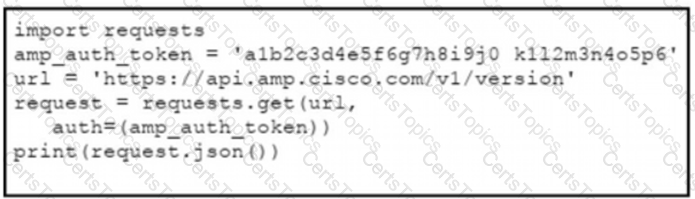
D)
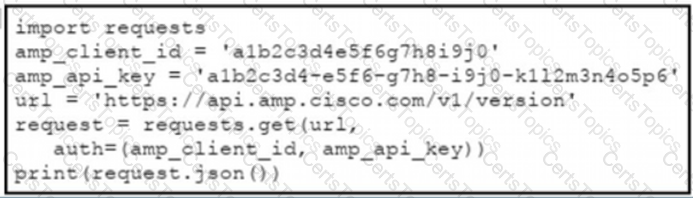
Why is refactoring done during test-driven development?
Refer to the exhibit.
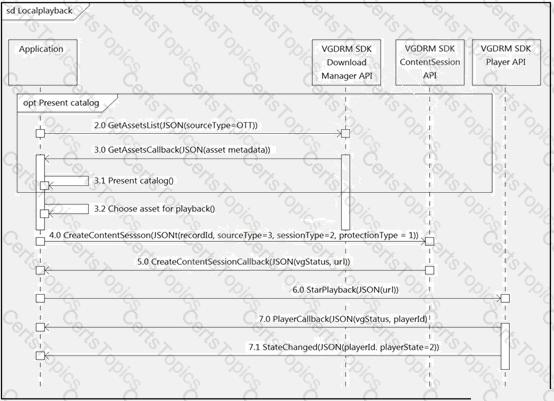
What do all the calls shown in the sequence diagram have in common?
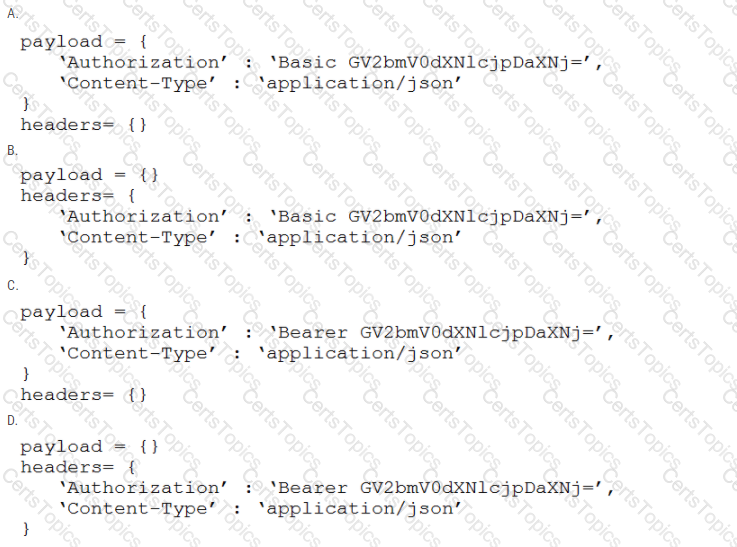
A developer is creating a script to interact with a REST API service which requires basic authentication. The credentials are "devnet:391665405" and the Base64 encoding of the credentials is "GV2bmV0dXNlcjpDaXNj=". Which payload and header combination must be used for authentication?
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
Which API must an engineer use to change a netmask on a Cisco IOS XE device?
Before which process is code review performed when version control is used?
A developer is trying to retrieve data over a REST API. The API server responds with an HTTP client error response code. After investigating the response the developer realizes the realizes the response has a Retry-After header. What is the root cause of this error?
What is a benefit of using edge computing in an IoT implementation?
What is the main purpose of a code review?
Which tool allows changes to the configuration management toolset to be tested?
Which protocol is used for clock synchronization between network devices?
What is a benefit of using Python classes?
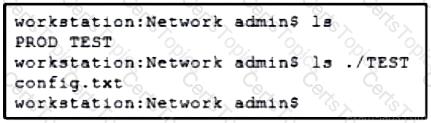
Refer to the exhibit. A network engineer must copy the “config.txt” file from directory TEST to directory PROD. The copied file must also be renamed into “current.txt”. Which command must be used to accomplish these tasks?
How does edge computing analyze sensitive data in the context of privacy control?
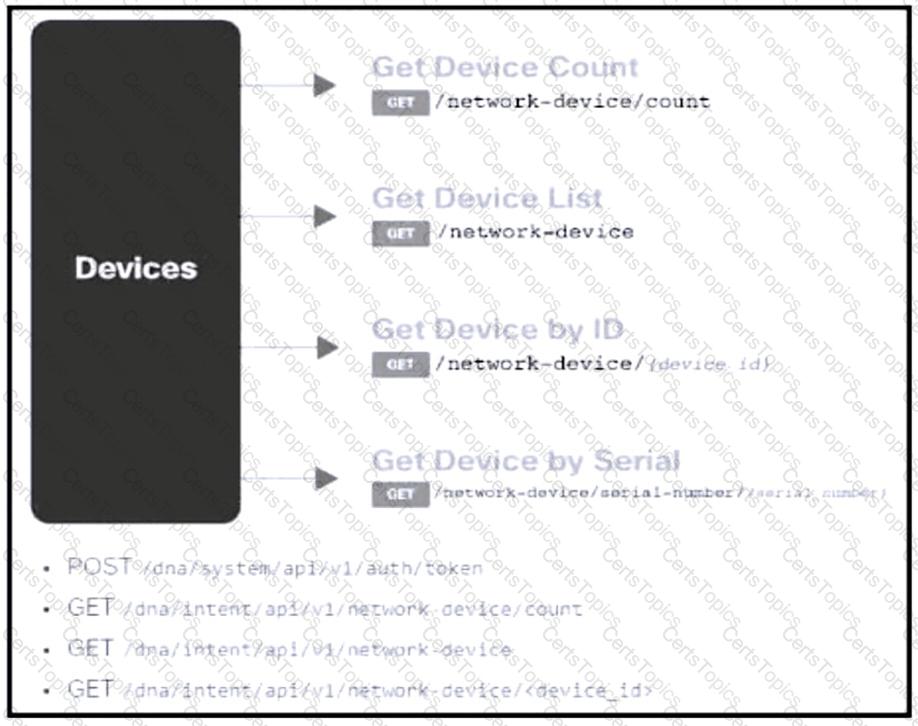
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a request that generates a security token and gets a list of network devices. Not all options are used.
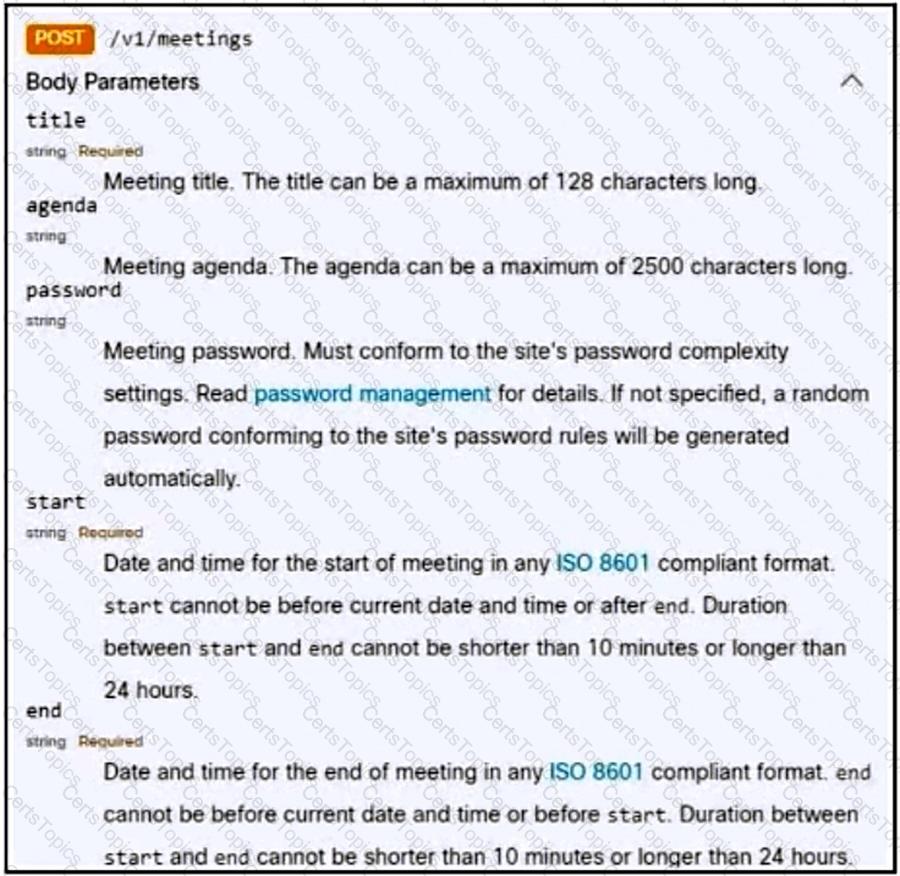
Refer to the exhibit. A bespoke meeting booking system must be integrated with Cisco Webex so that meetings are created automatically. Drag and drop the code from the bottom onto the box where the code is missing to create a sample meeting. Not all options are used.
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information?

Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the ..call?
A)

B)

C)

D)

A development team is creating an application used for contactless payments. The application must:
Be web-based
Capture and process the credit card information for a purchase.
Which security action must the web application use to gather and process the private customer data?
What is a capability of the AXL API?
Refer to the exhibit.
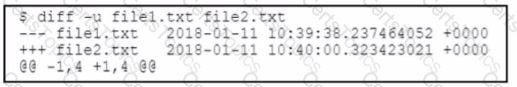
What occurs when the script runs?
What is a benefit of using a code review process in application development?
Which two details are captured from the subnet mask? (Choose two.)
Refer to the exhibit.
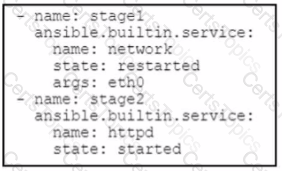
The IT team deployed a new Linux virtual machine for a software engineer to use. but the engineer is not comfortable configuring services using Bash. Which workflow is automated by the Ansible playbook?
Refer to the exhibit.
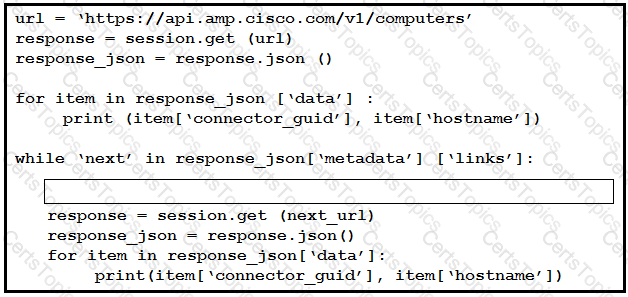
An engineer sends the request to collect data over Cisco AMP for Endpoints API. The Engineer must list guide and hostname data for all computers, but the first request returns only 500 items out of 2,000. Then, the engineer adds the loop to collect all the data. What must be added to the script where the code is missing to complete the requests?
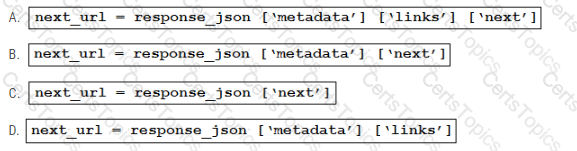
What is a benefit of a distributed version control system?
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.

Which IP service is responsible for automatically assigning an IP address to a device?
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
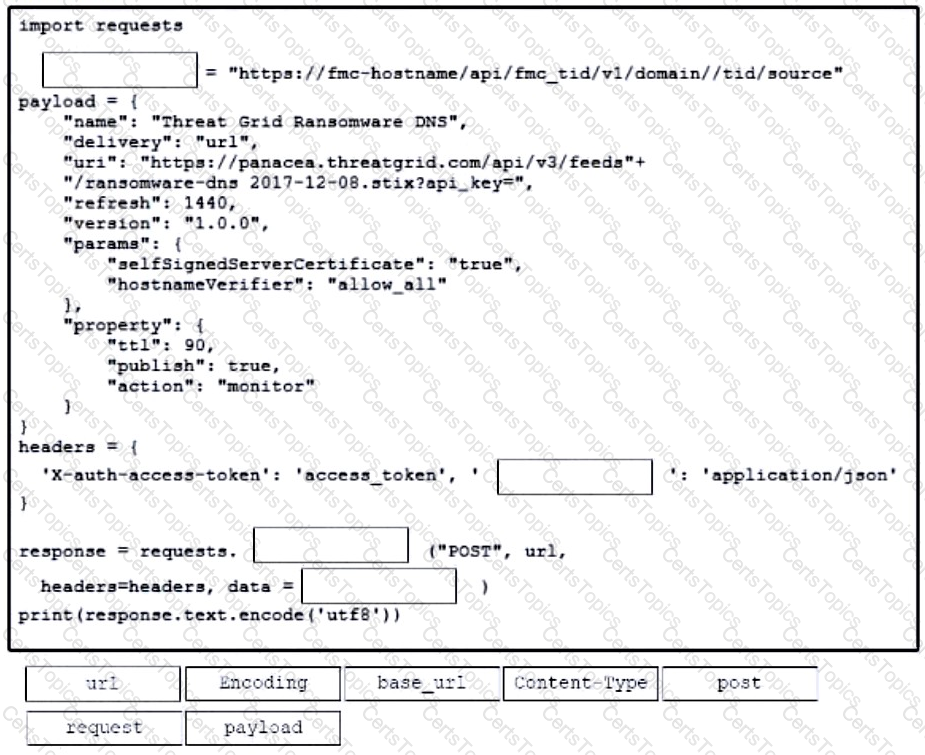
Which two protocols are associated with the control plane on a network device? (Choose two.)
Which function does a router provide to a network?
Refer to the exhibit.
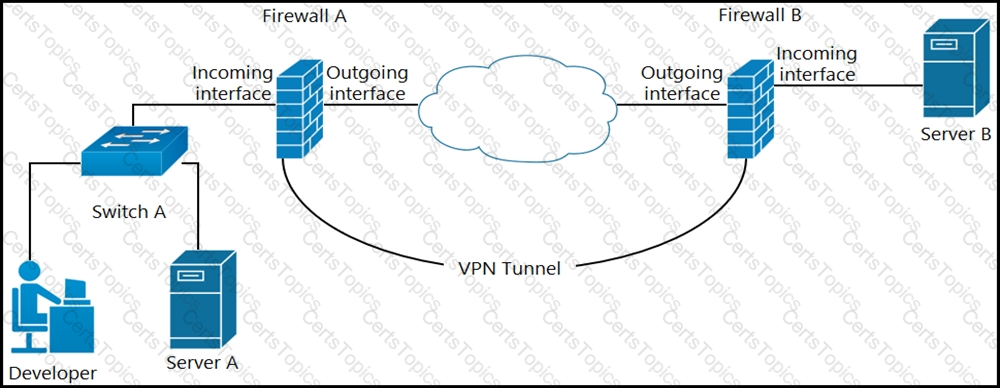
A developer can access the TLS REST API on server A, but cannot access the API on server B. The developer can ping server B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue?
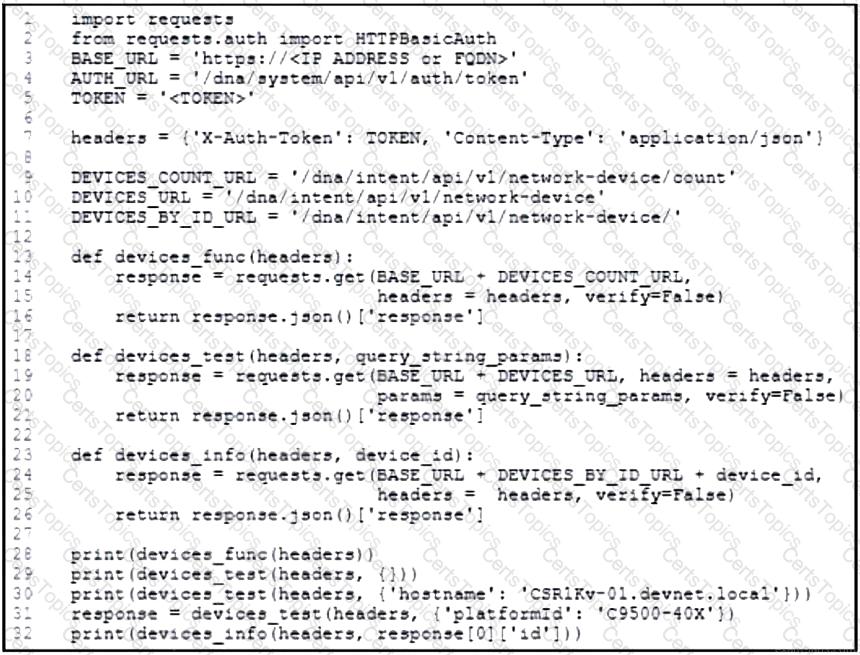
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
total count of devices
list of the network devices
information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
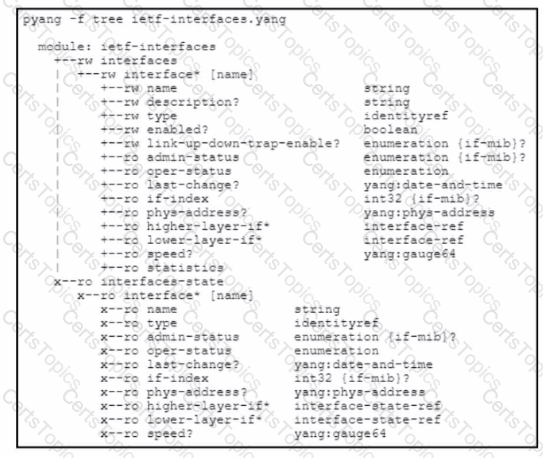
Refer to the exhibit.
Which type of YANG object is "interfaces"?
Refer to the exhibit.
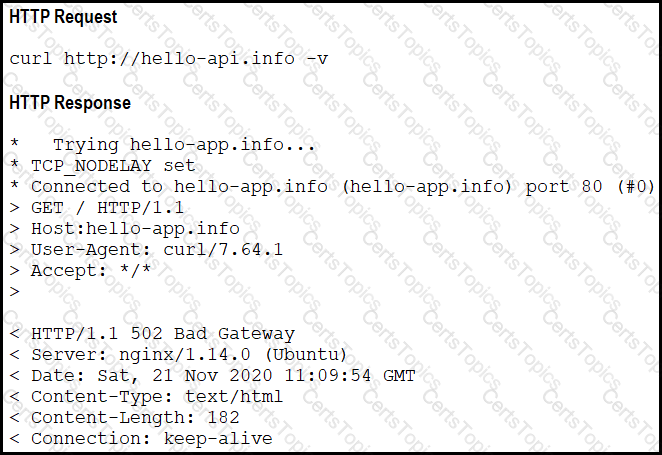
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
Which two commands download and execute an Apache web server container in Docker with a port binding 8080 in the container to 80 on the host? (Choose two.)
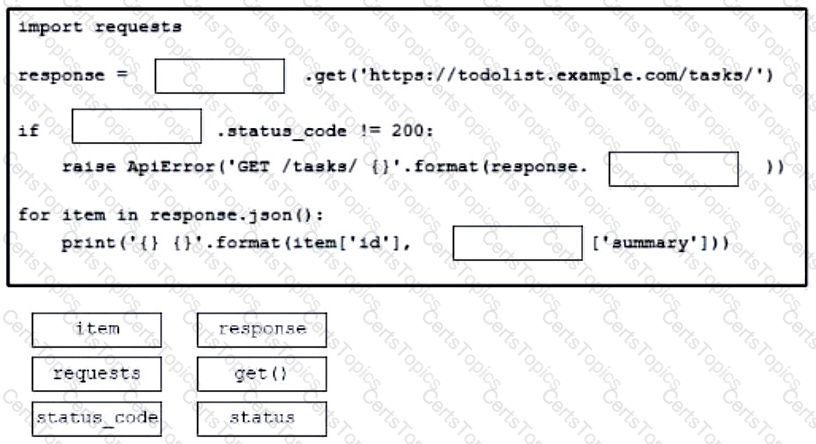
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. The Python script retrieves a list of tasks from a to-do list for effective project management purposes. Not all options are used.
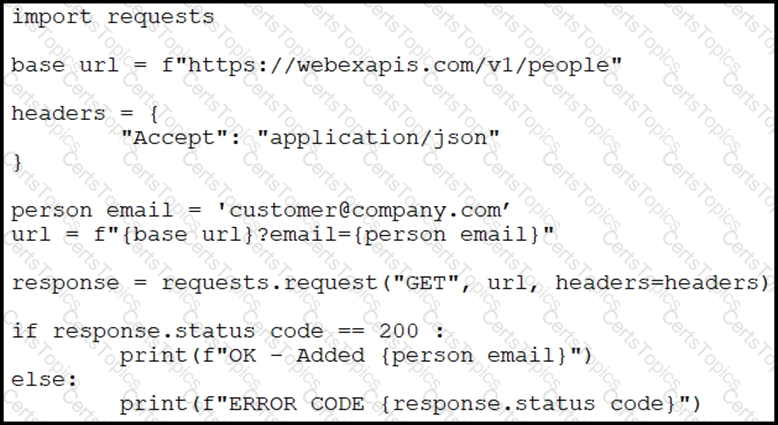
Refer to the exhibit.
A collaboration engineer has developed a script to automate the gathering of information by providing the email address of the individual. When the engineer tests the script, a 401 error is received. Which command fixes the script?
Which action do webhooks enable an application to perform?
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
Drag and drop the code from the bottom onto the box where the code is missing to enable ports on a switch by using RESTCONF. Not all options are used.

What is the impact on an application from having a large distance between a client device and a host server?
A group of software developers wants to improve its collaboration with the operations team. The group wants to deliver release-ready code that merges code changes back to the main branch and runs the automated testing as often as possible. Which DevOps concept does this scenario represent?
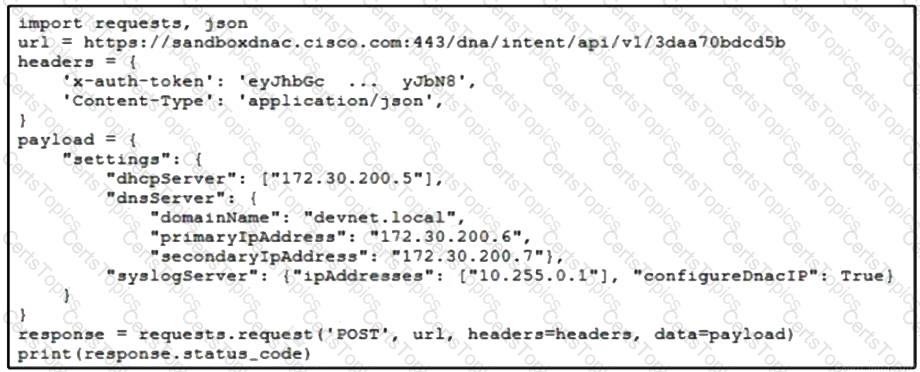
Refer to the exhibit. A developer writes a script to create a new network by using the Cisco DNA Center API. After running the script for the first time, the developer observes that HTTP code 404 is printed to the console. Which action resolves the problem?
A developer creates a program in which an object maintains a list of classes based on the observer pattern. The classes are dependent on the object. Whenever the state of the object changes, it notifies the dependent classes directly through callbacks. Which advantage of the observer pattern offers minimum dependencies and maximum flexibility between dependent objects or classes?
An engineer must investigate the problems on a web application and address them to related teams. The engineer verifies the application reachability from the single public IP
dress with port and discovers that HTTPS access works to three servers of a network farm with IP 172.16.50.1 .2 and .4. but HTTPS access to the server with IP 172.16.50.3 does : work. Which problem type must be addressed as the cause for the case?
What is the function of an Ethernet switch in a networking environment?
Which technology is responsible for matching a name to an IP address of an application running on a host?
Drag and drop the steps from the left into order on the right to create a common CI/CD pipeline process. Not all options are used.
A distributed application was developed using the Cisco intersight SDK. While testing the interaction between the application and the intersight API. the requests that were sent to ..server could not execute because the application was blocked by the firewall. Which URL and port must be provided to the firewall administrator to allow the traffic?
Which IP service is used to monitor the performance of network devices?
A developer creates a new application, but the application must be tested before being released to a customer. When a mobile phone that uses 4G is used to access the application, the request fails. Why does the connection to the application fail?
Refer to the exhibit.
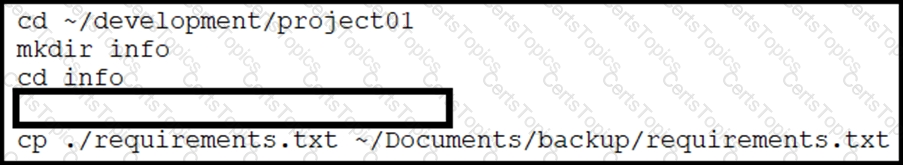
A developer just finished testing a Python script and wants to save the list of packages and versions installed on the current machine. The developer must make sure that it will not cause any issues if tested on another device due to different library versions. Which line of code needs to be placed on the snippet where the code is missing?
What is the purpose of grouping devices in a VLAN?
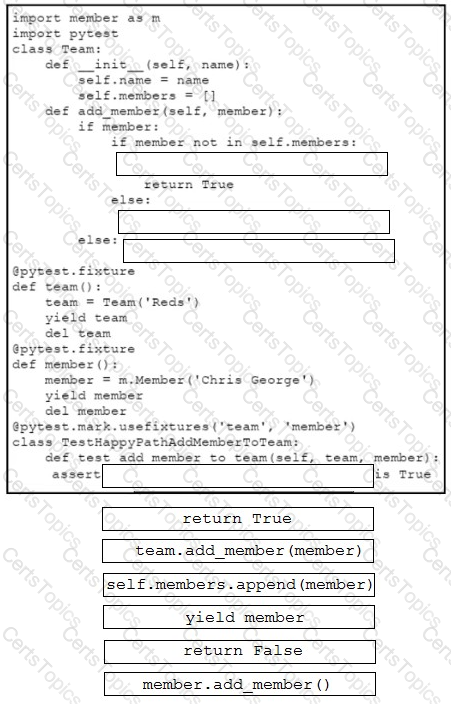
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used.