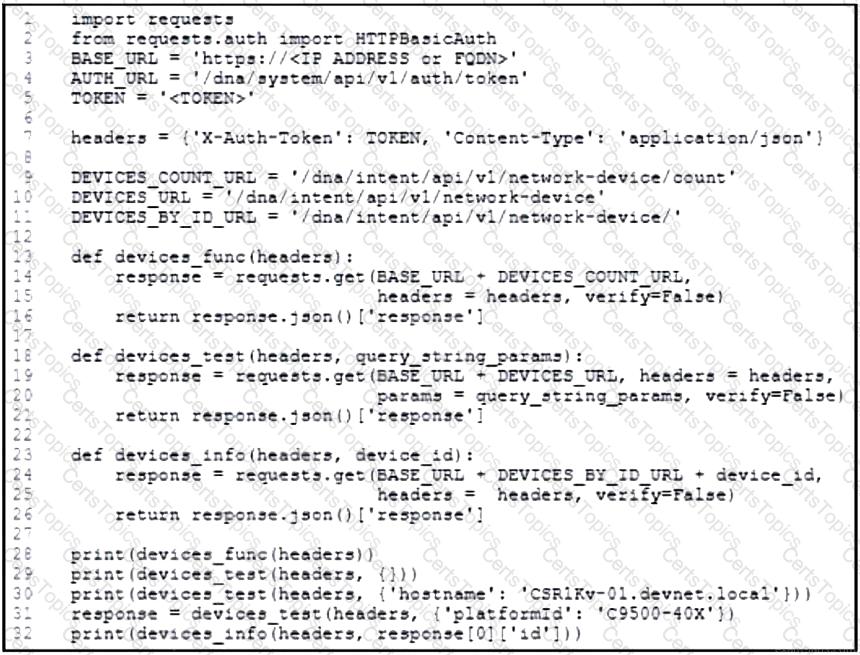
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
total count of devices
list of the network devices
information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
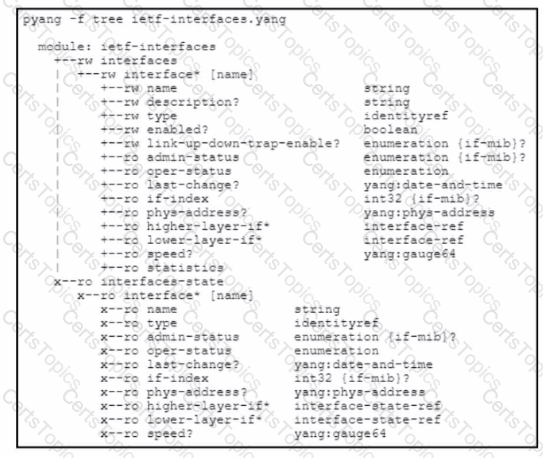
Refer to the exhibit.
Which type of YANG object is "interfaces"?
Refer to the exhibit.
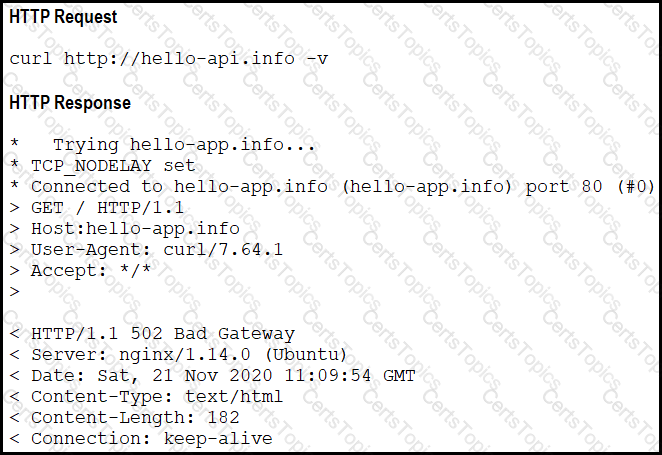
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?