 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.
Step 1: Analyze the Data and Question
Scenario:
Company data (directory, compensation report, user data) is found on the dark web.
CIO asks you to investigate and implement the most secure protection for employee accounts.
Task:
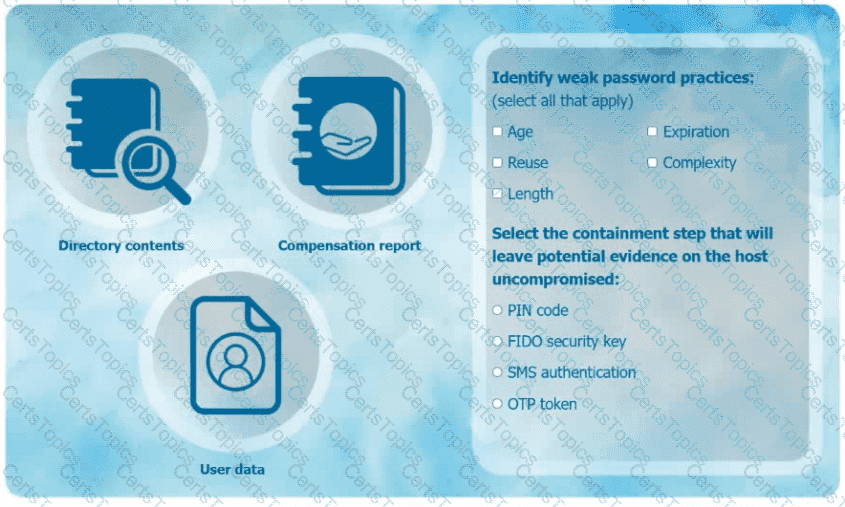
Identify weak password practices.
Choose the best containment step that keeps evidence on the host uncompromised.
Step 2: Identify Weak Password Practices
Prompt: Select all weak password practices from the list:
Age
Reuse
Length
Expiration
Complexity
Let’s analyze each:
Age: If passwords are used for a long time without change, it's a weak practice (passwords become easier to compromise over time).
Reuse: Reusing passwords across accounts is a serious weak practice (if one gets leaked, all accounts are at risk).
Length: Short passwords are weak; password length matters. If passwords are too short, that’s a weak practice.
Expiration: Forcing frequent expiration can lead to weaker passwords (users pick simple ones), but not expiring passwords at all is also risky. (For most exams, "expiration" by itself isn't usually called a weak practice unless the policy is poorly set.)
Complexity: Lack of complexity (not requiring numbers, symbols, etc.) is a weak practice.
So, select all that are truly weak practices:
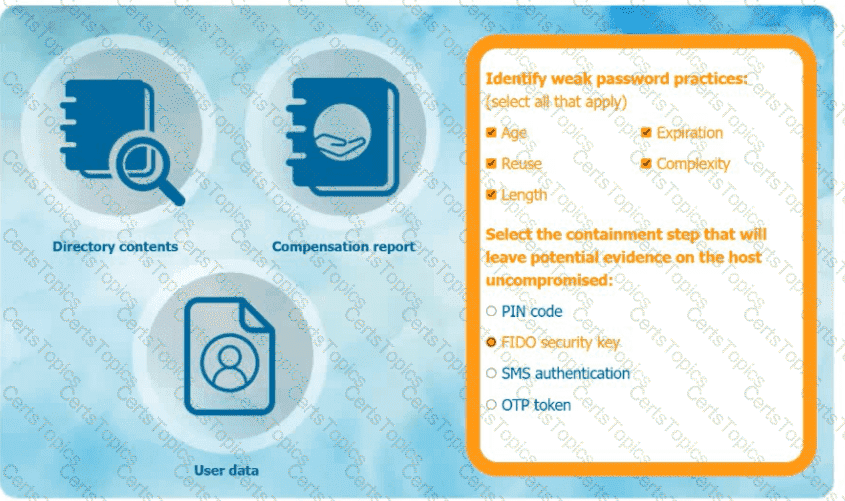
Answer for weak password practices (check all that apply):
✔️ Age
✔️ Reuse
✔️ Length
✔️ Complexity
(Expiration is more controversial; on the exam, the main focus is usually on Age, Reuse, Length, and Complexity.)
Step 3: Choose the Best Containment Step
Prompt:
Select the containment step that will leave potential evidence on the host uncompromised:
PIN code
FIDO security key
SMS authentication
OTP token
Containment step means “what security solution can you implement to protect employee accounts going forward, while preserving digital evidence on potentially compromised systems?”
The most secure solution for account protection among these, that also doesn’t interfere with host evidence, is FIDO security key.
Why?
PIN code: Not strong enough; also may be stored locally.
SMS authentication: Can be intercepted; often leaves traces on the host (like SMS logs).
OTP token: Similar risks, some implementations might log to the host.
FIDO security key: Hardware-based, phishing-resistant, no codes sent to the host, and doesn’t alter host evidence—authentication happens off the device.
So, the best answer is:
FIDO security key
Step 4: Solution Recap and Justification
Detailed Solution Recap:
Identify weak password practices:
Weaknesses: passwords are reused, not long enough, lack complexity, and used for a long time.
Select the best security solution:
Implement FIDO security keys for employees.
Most secure among listed options.
Hardware-based; resistant to phishing, interception, and does not leave evidence on the compromised host (which is important for forensics).