Which of the following can assist in recovering data if the decryption key is lost?
A security analyst reviews domain activity logs and notices the following:
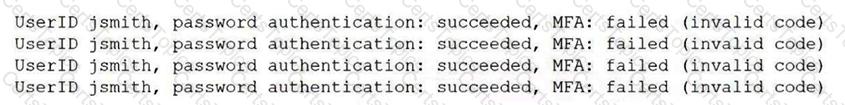
Which of the following is the best explanation for what the security analyst has discovered?
An administrator learns that users are receiving large quantities of unsolicited messages. The administrator checks the content filter and sees hundreds of messages sent to multiple users. Which of the following best describes this kind of attack?
A visitor plugs a laptop into a network jack in the lobby and is able to connect to the company's network. Which of the following should be configured on the existing network infrastructure to best prevent this activity?