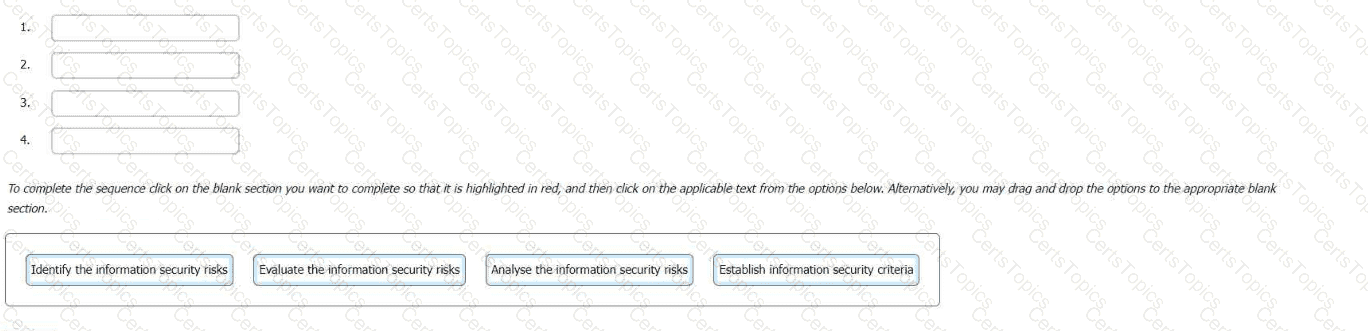
Select the correct sequence for the information security risk assessment process in an ISMS.
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank
The scope of an organization certified against ISO/IEC 27001 states that they provide editing and web hosting services. However, due to some changes in the organization, the technical support related to the web hosting services has been outsourced. Should a change in the scope be initiated in this case?
In regard to generating an audit finding, select the words that best complete the following sentence.
To complete the sentence with the best word(s), click on the blank section you want to complete so that it Is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.

Select two of the following options that are the responsibility of a legal technical expert on the audit team during a certification audit.
Evaluating the auditee's legal knowledge