The correct order for PPPoE discovery stage is:
Initialization, Session confirmation, Request and Offer
Initialization, Offer, Request and Session confirmation
Request, Initialization, Session confirmation and Offer
Request, Offer, Initialization and Session confirmation
PPPoE (Point-to-Point Protocol over Ethernet) uses a discovery stage before establishing the actual PPP session. The correct sequence is:
Initialization → Client sends a PADI (PPPoE Active Discovery Initiation)
Offer → Server responds with PADO (PPPoE Active Discovery Offer)
Request → Client sends PADR (PPPoE Active Discovery Request)
Session Confirmation → Server sends PADS (PPPoE Active Discovery Session-confirmation)
A.✘Wrong sequence
B.✔Correct – Matches the technical flow: PADI → PADO → PADR → PADS
C.✘Incorrect order
D.✘Incorrect order
Extract from MTCNA Course Material – PPPoE Process:
“The PPPoE discovery stage includes PADI, PADO, PADR, and PADS messages. This translates to Initialization, Offer, Request, Session confirmation.”
Extract from MikroTik Wiki – PPPoE Protocol:
“The discovery stage is used to establish a PPPoE session and includes four steps: PADI, PADO, PADR, and PADS.”
===========
What is a stub network?
A network with more than one exit point.
A network with more than one exit and entry point.
A network with only one entry and no exit point.
A network that has only one entry and exit point.
A stub network is defined as a network segment that is accessible by only one path (single entry/exit point). It does not serve as a transit network for routing between other networks. Traffic entering or leaving the stub network must pass through a single interface.
MTCNA Course Material – Routing Concepts:
“A stub network is one that is connected to the rest of the network by a single router interface. It has only one entry and one exit point.”
René Meneses MTCNA Study Guide – Routing Terms:
“Stub networks do not forward packets for other networks. They are endpoints with one route in and out.”
Other options:
A/B: Describe transit networks, not stub
C: Misleading—stub has both entry and exit, but only through one path
D:✔Correct definition
Final Answer: DQUESTION NO: 130 [PPP – Protocol Functions]
What PPP protocol provides dynamic addressing, authentication, and multilink?
A. NCP
B. HDLC
C. LCP
D. X.25
Answer: C
LCP (Link Control Protocol) is responsible for establishing, configuring, and testing the data-link connection in PPP. It handles features such as:
Authentication (PAP/CHAP)
Link quality testing
Multilink (combining multiple connections)
Negotiating link options
MTCNA Course Material – PPP Configuration:
“LCP handles link configuration, authentication, multilink, and error detection. NCP handles network layer protocol configuration.”
René Meneses MTCNA Study Guide – PPP Stack:
“LCP is the control protocol used to manage and negotiate the PPP connection, including authentication and multilink.”
Other options:
A: NCP negotiates Layer 3 protocol settings (e.g., IP, IPX)
B: HDLC is a simpler Layer 2 protocol, no support for dynamic addressing or multilink
D: X.25 is a packet-switched WAN protocol, not part of PPP
Final Answer: CQUESTION NO: 131 [Switching – Spanning Tree Protocol (STP)]
In a network with dozens of switches, how many root bridges would you have?
A. 1
B. 2
C. 5
D. 12
Answer: A
Spanning Tree Protocol (STP) is used in Ethernet switching environments to prevent loops. In any STP domain, only one switch is elected as the root bridge. All other switches determine the shortest path to this root bridge and may block redundant paths.
MTCNA Course Material – STP Basics:
“STP ensures a loop-free topology by electing a single root bridge. All path calculations are made from the root bridge’s perspective.”
René Meneses MTCNA Study Guide – STP and Loop Prevention:
“Only one root bridge exists per STP domain. Switches use BPDU messages to elect it based on bridge ID priority.”
No matter how many switches exist (2, 10, or 50), only one root bridge is present at any time.
Final Answer: AQUESTION NO: 132 [IP Addressing – Classful Networking]
Which class of IP address has the most host addresses available by default?
A. A
B. B
C. C
D. A and B
Answer: A
Classful IP addressing reserves different address ranges and host counts:
Class A: 1.0.0.0 – 126.255.255.255 (/8) → 2^24 – 2 = 16,777,214 hosts
Class B: 128.0.0.0 – 191.255.255.255 (/16) → 2^16 – 2 = 65,534 hosts
Class C: 192.0.0.0 – 223.255.255.255 (/24) → 2^8 – 2 = 254 hosts
MTCNA Course Material – IP Address Classes:
“Class A has the largest number of hosts per network, over 16 million. Class B allows around 65,000, and Class C allows 254.”
René Meneses MTCNA Study Guide – Classful IP Summary:
“Class A provides the most host addresses by default due to its /8 subnet.”
Only Class A has the highest host count.
/interface wireless access-list is used for:
Handles a list of Client's MAC Address to permit/deny connection to AP
Shows a list of Client's MAC Address that are already registered at AP
Contains the security profiles settings
Authenticate Hot-Spot users
The /interface wireless access-list in MikroTik is used to define a set of rules that permit or deny wireless clients based on their MAC addresses and signal strength.
This list applies only to clients trying to connect to the router’s wireless interface when it is configured as an Access Point.
Let’s break down the options:
A.✅Correct – Used to allow or deny client MAC addresses and apply settings like rate limits, VLANs, etc.
B.❌That’s the role of the registration table.
C.❌Security profiles are configured separately under /interface wireless security-profiles.
D.❌Hotspot authentication is handled via /ip hotspot, not wireless access lists.
MTCNA Wireless Module – MAC Access Control:
“Access-list matches incoming clients by MAC. You can allow, deny, and apply custom settings.”
René Meneses Study Guide – Wireless Security:
“Access-list is used to explicitly permit or block clients based on their MAC address.”
Terry Combs Notes – Wireless Filtering:
“Think of access-list like a whitelist/blacklist for Wi-Fi clients.”
Answer: AQUESTION NO: 65 [Firewall]
One host on an internal network is accessing an external web page through a MikroTik router that is doing source NAT. Select the correct statement about the packets that flow from that web page to the host:
A. Packets go through the input chain
B. Packets go through the forward chain
C. Packets go through the output chain
D. Packets go through the input chain before the routing decision and after that through output chain
Answer: B
When a host on a LAN accesses a website on the internet via a MikroTik router that’s performing source NAT (e.g., masquerade), the traffic path is as follows:
From LAN host to internet → forward chain → NAT (src-nat)
From internet back to LAN host → forward chain again → connection-tracked → src-nat reversed
Since the router is only routing the packets and is not the originator or final destination, the packet passes through the forward chain.
Clarifying the options:
A.❌input chain is for packets destined to the router itself
B.✅Correct – packet is routed through the router (forwarded)
C.❌output chain is for packets originating from the router
D.❌This description applies to packets sourced by the router itself
MTCNA Course Manual – Packet Flow Diagram:
“Forward chain handles packets that are being routed through the device (not destined to or from the router itself).”
René Meneses Guide – Firewall Chains:
“For routed traffic, the forward chain is used. This includes NATed traffic between LAN and WAN.”
Terry Combs Notes – Packet Flow:
“Understand the router’s role. If it’s just forwarding, only the forward chain applies.”
Answer: BWould you like to continue with Questions 66–70, or generate a full summary (PDF-style) of all 65 completed qu
Bridging loops can be avoided by enabling:
RSTP protocol
STP protocol
Connection tracking
UDP filter
ICMP filter
Bridging loops occur when there are multiple active paths between switches or bridge interfaces, causing broadcast storms or MAC table instability. MikroTik RouterOS supports both STP (Spanning Tree Protocol) and RSTP (Rapid Spanning Tree Protocol) to detect and block redundant paths.
A.✔RSTP – Faster and preferred protocol to prevent loops.
B.✔STP – The original protocol, slower convergence but still effective.
C.✘Connection tracking – Not related to Layer 2 loop prevention.
D.✘UDP filter – Filters specific traffic types, doesn’t handle loops.
E.✘ICMP filter – Not relevant to Layer 2 loop protection.
Extract from Official MTCNA Course Material – Bridging and STP:
“STP or RSTP must be enabled to prevent bridging loops. RSTP is the recommended version due to faster convergence.”
Extract from René Meneses MTCNA Study Guide – Bridging:
“Always enable STP or RSTP when using bridges with multiple paths to prevent Layer 2 loops.”
Extract from MikroTik Wiki – STP / RSTP:
“STP and RSTP are loop prevention mechanisms for bridges. They dynamically block redundant links.”
===========
In which order are the entries in Access List and Connect List processed?
By Signal Strength Range
In sequence order
In a random order
By interface name
MikroTik processes entries in the Access List and Connect List in the order they are listed — from top to bottom. This is referred to as “sequence order.” The first rule that matches the client’s MAC address and interface conditions will be applied, and no further rules are evaluated after a match.
Incorrect options:
A. Signal strength can be used as a condition, but is not the order of evaluation.
C. Random order is never used in rule-based systems.
D. Interface names are used as match conditions, not ordering criteria.
MTCNA Wireless Module – Access and Connect List Order:
“Rules are checked from the top of the list down. The first matching rule is applied, then processing stops.”
René Meneses Guide – Wireless Security and MAC Filtering:
“Sequence matters. If multiple rules could apply, only the first one is enforced.”
Terry Combs Notes – Wireless Filtering:
“Don’t misplace rules. Connect-list and access-list are evaluated in listed order.”
Answer: BQUESTION NO: 59 [Queues – QoS]
Simple Queue number 0 defines 2M for upload and download for target IP 10.10.0.33.
Simple Queue number 1 defines 4M for upload and download for the same target IP 10.10.0.33.
Client 10.10.0.33 will be able to obtain:
A. 6M upload/download
B. 0M upload/download
C. 4M upload/download
D. 2M upload/download
Answer: D
In MikroTik RouterOS, when multiple simple queues are configured for the same target (IP address), only the first matching queue in sequence is processed. This means that:
If queue 0 (2M) comes before queue 1 (4M), the 2M limit will be enforced.
The second queue is ignored, even if it provides a higher rate.
MikroTik does not sum the bandwidth of multiple queues. The first applicable queue (based on order) wins.
MTCNA Course Manual – Simple Queues:
“Simple Queues are matched top-down. Only the first matching queue is applied per packet.”
René Meneses MTCNA Guide – QoS Queue Behavior:
“Queue order matters. The first rule that matches is the one used. Lower queues override lower ones if placed first.”
Terry Combs Notes – Queue Troubleshooting:
“If two queues match the same IP, only the first is active. Don’t stack queues unless using a queue tree.”
Answer: DQUESTION NO: 60 [RouterOS Packages]
Which features are removed when the advanced-tools package is uninstalled?
A. neighbors
B. LCD support
C. ip-scan
D. ping
E. netwatch
F. bandwidth-test
Answer: C, E, F
The advanced-tools package in MikroTik RouterOS contains a set of diagnostic and monitoring tools. If this package is removed, the following features are lost:
ip-scan →✅Used for scanning IP ranges to discover hosts
netwatch →✅Monitors host availability and runs scripts on status changes
bandwidth-test →✅Used to measure throughput between MikroTik devices
Incorrect options:
A. neighbors → Part of the main system package (MAC discovery)
B. LCD support → Tied to specific hardware; not affected by advanced-tools
D. ping → Part of the base system package
MTCNA System Tools Section – Package Breakdown:
“The advanced-tools package includes netwatch, bandwidth-test, and ip-scan. These are not part of the base system.”
René Meneses Guide – Package Management:
“Removing advanced-tools disables several diagnostic commands like ip-scan and bandwidth-test.”
Terry Combs Notes – Tools Overview:
“Ping and neighbors are in core OS. Advanced-tools affects monitoring scripts and traffic tools.”
Destination NAT (chain dstnat, action dst-nat) can be used to:
Change destination port
Direct users from the Internet to a server within your local network
Change source port
Hide your local network from the Internet
Destination NAT (dst-nat) is used to redirect packets arriving at the router to a different internal destination. It is most commonly used to allow public access to internal services such as web servers or mail servers.
You can:
Change the destination IP address (redirect to an internal host)
Change the destination port (e.g., port 8080 to port 80)
But:
C. Changing the source port is a function of src-nat, not dst-nat →❌
D. Hiding the local network from the Internet is done via masquerade or src-nat →❌
MTCNA Course Manual – NAT Section:
“Use dst-nat to forward traffic to a private host. Port translation can also be applied (e.g., from 81 to 80).”
René Meneses Study Guide – NAT Configuration:
“dst-nat changes the destination IP/port of packets arriving on a specific interface. Common use case: access to LAN services from WAN.”
Terry Combs Notes – NAT Rule Summary:
“dst-nat = port forwarding. src-nat/masquerade = hide internal addresses.”
Answer: A, BQUESTION NO: 48 [RouterOS Introduction]
Which is the default port of IP-Winbox?
A. UDP 8291
B. TCP 80
C. TCP 8291
D. TCP 8192
Answer: C
Winbox is MikroTik’s GUI-based configuration tool. It communicates with RouterOS over TCP port 8291 by default. This port is used for both IP-based Winbox connections and MAC-based sessions (in combination with layer-2 discovery protocol).
Evaluation:
A. UDP 8291 →❌Wrong protocol
B. TCP 80 →❌Used for HTTP (WebFig)
C. TCP 8291 →✅Correct default Winbox port
D. TCP 8192 →❌Invalid / non-standard
MTCNA Course Manual – RouterOS Management Tools:
“Winbox uses TCP port 8291 by default. It is possible to change this port in the /ip service settings.”
René Meneses MTCNA Guide – Winbox Access:
“Default access via TCP 8291. Check firewall filters to ensure it’s not blocked.”
Terry Combs Notes – Remote Management:
“Winbox = TCP/8291. WebFig = TCP/80 or 443.”
Answer: CQUESTION NO: 49 [PPP]
It is possible to create an encrypted PPPoE tunnel in RouterOS:
A. true
B. false
Answer: B
PPPoE (Point-to-Point Protocol over Ethernet) does not include encryption by default. It can authenticate users using PAP or CHAP, but the data payload is transmitted in cleartext unless another secure tunneling protocol (e.g., IPSec) is layered on top.
MikroTik supports encryption in other tunneling protocols, such as:
SSTP (uses SSL)
L2TP with IPSec
OpenVPN (SSL-based)
IPsec itself (for IP layer encryption)
MTCNA Tunneling Chapter – PPP Protocol Features:
“PPPoE offers authentication, compression, but no native encryption. Use IPSec if encryption is needed.”
René Meneses Guide – Tunnel Comparison Table:
“PPPoE is not encrypted. SSTP and L2TP/IPSec are alternatives when encryption is a requirement.”
Terry Combs Notes – PPP Family Summary:
“PPPoE: Authentication = Yes, Encryption = No. Use with caution over untrusted networks.”
Answer: BQUESTION NO: 50 [Wireless]
Why is it useful to set a Radio Name on the radio interface?
A. To identify a station in a list of connected clients
B. To identify a station in Neighbor discovery
C. To identify a station in the Access List
Answer: A
The Radio Name is a human-readable identifier assigned to a wireless interface. It becomes visible in the Registration Table (i.e., the list of connected clients) on an access point. It helps network administrators distinguish between multiple connected devices.
Evaluation:
A.✅Correct — Radio Name is shown in the Registration Table (list of connected clients)
B.❌Neighbor discovery uses MAC and device identity, not radio name
C.❌Access List uses MAC addresses, not radio name, for matching
MTCNA Wireless Module – Interface Settings:
“Radio Name is shown in the registration table on the AP. It helps in client identification.”
René Meneses Guide – Wireless Monitoring:
“The AP uses the client’s Radio Name to label them in the list of associated stations.”
Terry Combs Notes – Best Practice:
“Set radio-name so you can easily tell which device is which in the registration list.”
Answer: A
What is the correct action to be specified in the NAT rule to hide a private network when communicating to the outside world?
masquerade
allow
passthrough
tarpit
In MikroTik RouterOS, the masquerade action is used in source NAT (srcnat) rules to hide internal/private IP addresses behind a router’s public IP address. This is typically done for internet access from a LAN where the devices have private IP addresses (e.g., 192.168.x.x).
Masquerade dynamically changes the source IP of outgoing packets to the IP address of the router’s outbound interface, allowing multiple internal devices to share a single public IP.
Let’s evaluate the options:
A. masquerade →✅Correct. Used to perform source NAT for hiding private addresses.
B. allow →❌Not a valid NAT action.
C. passthrough →❌Used in mangle rules to continue processing additional rules, not for NAT.
D. tarpit →❌Used to delay TCP connections (often in firewall, not NAT).
MTCNA Course Manual – NAT Chapter:
“Masquerade is a special form of source NAT where the router replaces the source IP with the IP address of the outgoing interface.”
René Meneses Guide – NAT Configuration:
“Use masquerade on the router’s WAN interface to give internet access to private clients.”
Terry Combs Notes – NAT Rule Actions:
“Masquerade = dynamic src-nat. Useful when public IP is dynamic or unknown.”
Answer: AQUESTION NO: 62 [PPP / AAA]
Router A and B are both running as PPPoE servers on different broadcast domains of your network. It is possible to set Router A to use "/ppp secret" accounts from Router B to authenticate PPPoE customers.
A. true
B. false
Answer: B
/ppp secret accounts are local to each RouterOS device. These credentials are stored in the router’s own configuration and cannot be shared directly between routers.
To centralize authentication across multiple routers, a RADIUS server must be used. With RADIUS, multiple MikroTik routers can authenticate users against a single, centralized user database.
Without RADIUS or another external AAA system:
Each router maintains its own /ppp secret list
Router A cannot directly read or use the /ppp secrets from Router B
Evaluation:
A.❌False. There is no built-in mechanism for Router A to access secrets on Router B.
B.✅Correct. You must use RADIUS if you want shared authentication across routers.
MTCNA PPP Module – Authentication Methods:
“/ppp secrets are stored locally on the router. For shared user authentication, configure RADIUS.”
René Meneses Study Guide – PPPoE and RADIUS:
“To authenticate clients on multiple routers with a central database, RADIUS is required.”
Terry Combs Notes – PPP Secrets vs RADIUS:
“Local secrets cannot be accessed remotely. Use RADIUS to centralize authentication.”
Answer: B
What is the term for the hardware coded address found on an interface?
FQDN Address
IP Address
Interface Address
MAC Address
The hardware-coded address that uniquely identifies a device's network interface card (NIC) on the local network is called a MAC address. It is “burned in” by the hardware manufacturer and remains constant unless manually overridden.
MAC stands for Media Access Control, and it operates at Layer 2 of the OSI model. It is used to identify devices on a local area network.
A. FQDN (Fully Qualified Domain Name) refers to a human-readable name used in DNS.
B. IP Address is a logical address used for routing at Layer 3.
C. Interface Address is a generic term and not a standard identifier.
D. MAC Address is correct and refers to the physical, hardware-encoded address on an interface.
Extract from MTCNA Course Manual – RouterBOARD Overview:
“A MAC address is a globally unique hardware identifier assigned to each Ethernet or wireless interface. It is used by Layer 2 to ensure local delivery.”
René Meneses Study Guide – MAC & OSI Layering:
“The MAC address is a 48-bit physical identifier, hardcoded by the device vendor and located in the NIC chip.”
Terry Combs MTCNA Notes – Layer 2 Concepts:
“MAC = Physical Address = Layer 2 Identifier. It’s what switches use to forward Ethernet frames.”
===========
What protocol does PPP use to identify the Network layer protocol?
NCP
ISDN
HDLC
LCP
PPP (Point-to-Point Protocol) uses a modular architecture consisting of two main components:
LCP (Link Control Protocol): Establishes, configures, and tests the data-link connection
NCP (Network Control Protocol): Identifies and configures protocols at the Network Layer (e.g., IP, IPX)
NCP allows multiple protocols to be used over the same PPP link by negotiating and identifying the type of Layer 3 protocol.
MTCNA Course Material – PPP Components:
“NCP handles Layer 3 protocol negotiation and support. For example, IPCP (IP Control Protocol) is a type of NCP used for IP.”
René Meneses MTCNA Study Guide – PPP Protocol Stack:
“PPP uses NCP to identify and configure multiple Layer 3 protocols such as IP, IPX, AppleTalk.”
Other options:
B: ISDN is a WAN access technology, not part of PPP stack
C: HDLC is a data-link layer protocol, not used for identifying Layer 3
D: LCP configures link parameters, not network layer protocols
Final Answer: AQUESTION NO: 142 [Cisco IOS – IOS Backup Procedure]
To back up an IOS, what command will you use?
A. backup IOS disk
B. copy ios tftp
C. copy tftp flash
D. copy flash tftp
Answer: D
To back up the Cisco IOS image from the router’s flash memory to an external TFTP server, the correct command is:
copy flash tftp
This command initiates a transfer from flash memory to a TFTP server and is the standard procedure for backing up IOS images.
Cisco IOS Configuration Guide – Image Backup:
“To back up your IOS image, use the command copy flash tftp and follow the prompts for file name and TFTP server IP.”
René Meneses MTCNA Study Guide – IOS Management:
“copy flash tftp is the correct syntax to save a router’s current IOS to a TFTP server.”
Other options:
A: Invalid syntax
B: Invalid command (copy ios does not exist)
C: copy tftp flash is for installing, not backing up
Final Answer: DQUESTION NO: 143 [IP Addressing – Subnet Calculation]
Which of the following is the valid host range for the subnet on which the IP address 192.168.168.188 255.255.255.192 resides?
A. 192.168.168.129–190
B. 192.168.168.129–191
C. 192.168.168.128–190
D. 192.168.168.128–192
Answer: B
IP address: 192.168.168.188
Subnet mask: 255.255.255.192 → /26 → Block size = 64
Subnets:
192.168.168.0/26 → 192.168.168.0 – 63
192.168.168.64/26 → 192.168.168.64 – 127
192.168.168.128/26 → 192.168.168.128 – 191 ← Contains 192.168.168.188
192.168.168.192/26 → 192.168.168.192 – 255
Valid host range = 192.168.168.129 – 190
(Broadcast = 191, Network address = 128)
MTCNA Course Material – Subnetting Practice:
“To find valid hosts, exclude the subnet and broadcast address. In /26, each block is 64 addresses.”
René Meneses MTCNA Study Guide – IP Addressing:
“For /26 subnetting, calculate block size as 2^(32–26) = 64. Subnet starts at multiples of 64.”
Final Answer: BQUESTION NO: 144 [Wireless – IEEE 802.11 Standards]
Which WLAN IEEE specification allows up to 54 Mbps at 2.4 GHz?
A. A
B. B
C. G
D. N
Answer: C
802.11g operates in the 2.4 GHz band and supports data rates up to 54 Mbps. It is backward-compatible with 802.11b and was a significant improvement in speed while maintaining wide compatibility.
MTCNA Course Material – Wireless Standards:
“802.11g operates at 2.4 GHz and supports up to 54 Mbps. It is widely used in legacy devices.”
René Meneses MTCNA Study Guide – WLAN Specifications:
“802.11g = 2.4 GHz, 54 Mbps.
802.11a = 5 GHz, 54 Mbps
802.11b = 2.4 GHz, 11 Mbps
802.11n = 2.4/5 GHz, up to 600 Mbps (MIMO)”
Option Breakdown:
A: 802.11a = 54 Mbps at 5 GHz
B: 802.11b = 11 Mbps at 2.4 GHz
C: 802.11g =✔54 Mbps at 2.4 GHz
D: 802.11n = supports 2.4/5 GHz, speeds up to 600 Mbps (depending on MIMO)
fundamentals.
────────────────────────────────────────────────────────────
What flavor of Network Address Translation can be used to have one IP address allow many users to connect to the global Internet?
NAT
Static
Dynamic
PAT
PAT (Port Address Translation) is a subtype of NAT that maps multiple private IP addresses to a single public IP address using different port numbers. It is the most common form of NAT used in home and business networks to allow multiple internal hosts to access the internet using one public IP address.
MTCNA Course Material – NAT Concepts:
“PAT (also known as NAT overload) allows multiple devices to share a single public IP address. It uses different port numbers to distinguish sessions.”
Cisco IOS NAT Configuration Guide:
“PAT translates multiple local IP addresses to one public IP address by assigning different port numbers to each session.”
Other options:
A: Generic term — not specific enough
B: Static NAT maps one private IP to one public IP
C: Dynamic NAT maps private IPs to a pool of public IPs, not one-to-many
Final Answer: DQUESTION NO: 149 [IPv6 – Addressing Standards]
How long is an IPv6 address?
A. 32 bits
B. 128 bytes
C. 64 bits
D. 128 bits
Answer: D
IPv6 addresses are 128 bits in length, represented as eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). This allows for a vastly larger address space compared to IPv4 (32 bits).
MTCNA Course Material – IPv6 Basics:
“An IPv6 address is 128 bits long, providing 3.4×10^38 possible addresses. It is written in hexadecimal format.”
René Meneses MTCNA Study Guide – IPv6 Addressing:
“IPv6 = 128 bits, not bytes. Address includes a 64-bit network prefix and 64-bit interface identifier.”
Other options:
A: 32 bits is IPv4
B: 128 bytes = 1024 bits — incorrect
C: 64 bits = only half of an IPv6 address
Final Answer: DQUESTION NO: 150 [IP Addressing – Subnetting]
How many usable IP addresses are there in a 23-bit (255.255.254.0) subnet?
A. 512
B. 510
C. 508
D. 254
Answer: B
A /23 subnet provides 2^9 = 512 total addresses.
Subtract 2 (network address + broadcast address)
512 – 2 = 510 usable IP addresses
MTCNA Course Material – Subnet Calculations:
“For any subnet, usable hosts = 2^(32 – subnet mask bits) – 2.”
René Meneses MTCNA Study Guide – IP Subnetting:
“/23 provides 512 total addresses; usable = 510 after subtracting network and broadcast.”
Option Breakdown:
A: Total addresses (512)
B:✔Usable addresses (510)
C: Incorrect (508 is for /23 minus 4 — not relevant here)
D: 254 is usable for /24
Action=redirect is applied in:
chain=srcnat
chain=forward
chain=dstnat
The redirect action is only valid in the dstnat chain. It is used to redirect traffic to a service running on the router itself (e.g., redirecting HTTP to a local proxy server).
A.✘srcnat – Not compatible with redirect
B.✘forward – Redirect doesn’t apply in this chain
C.✔dstnat – This is the correct and only supported chain for action=redirect
Extract from Official MTCNA Course Material – NAT Actions:
“The redirect action is used within the dstnat chain to forward packets to the router’s local services.”
Extract from MikroTik Wiki – NAT Rule Actions:
“Redirect is used in dstnat chain and changes destination address to a local router IP and port.”
===========
Mark all features that are compatible with Nstreme
WDS between a device in station-wds mode and a device in station-wds mode
Encryption
WDS between a device in ap-bridge mode with a device in station-wds mode
Bridging a device in station mode with a device in ap-bridge mode
Nstreme is a proprietary point-to-point wireless protocol developed by MikroTik to improve performance on long-distance wireless links. It enhances frame aggregation, reduces latency, and replaces standard 802.11 MAC timing behavior with a custom approach. Because of its specific mechanism, it imposes certain compatibility restrictions:
A. WDS between two station-wds devices is not compatible with Nstreme. This setup doesn't conform to proper AP-client architecture required by Nstreme, which operates in a master/slave role — typically ap-bridge and station.
B. Encryption (e.g., using WEP or WPA) is supported in Nstreme; however, MikroTik recommends encryption at higher layers like IPsec when performance is critical.
C. WDS between ap-bridge and station-wds is compatible with Nstreme. This is the standard pairing used when bridging two networks via wireless.
D. Bridging a station with an ap-bridge device using standard station mode (not station-wds or station-bridge) is not compatible for full Layer 2 bridging. Only station-wds or station-bridge supports bridging with ap-bridge mode.
Extract from Official MTCNA Course Material – Wireless Section:
"Nstreme is supported only between a device in ap-bridge mode and a device in station or station-wds mode. Both ends must support Nstreme. WDS is supported with station-wds and ap-bridge combinations. Encryption is supported, although optional."
Extract from Terry Combs MTCNA Notes – Nstreme Notes:
"Only ap-bridge <-> station-wds (or station-bridge in RouterOS v6+) is valid for bridging over Nstreme. Encryption like WPA2 is supported but optional."
Extract from René Meneses Study Guide – Wireless Features:
“Nstreme does not support station-station WDS. Proper implementation requires ap-bridge on one side and station-wds or station-bridge on the other. Basic encryption (WEP/WPA) is allowed.”
===========
You cannot use OSPF and RIP routing protocols simultaneously on RouterOS.
FALSE
TRUE
MikroTik RouterOS supports running multiple dynamic routing protocols simultaneously, including RIP, OSPF, and BGP. They are independent processes and can be configured in parallel. This is commonly used in complex network environments or during routing migrations.
A.✔FALSE – You can run OSPF and RIP at the same time.
B.✘TRUE – Incorrect; both protocols are fully supported to coexist.
Extract from MTCNA Course Material – Dynamic Routing:
“RouterOS supports multiple dynamic routing protocols, including simultaneous use of RIP and OSPF.”
Extract from René Meneses Study Guide – Routing Protocols:
“You can configure both RIP and OSPF to run at the same time on a single router.”
Extract from MikroTik Wiki – Routing Overview:
“RouterOS allows multiple routing protocols to operate concurrently.”
===========
There are two wireless cards (wlan1 and wlan2) which are bridged together. On wlan1 card thereis a setting "Forwarding=no". Choose the correct answer(s):
Stations on wlan2 will be able to communicate with stations on wlan2
Stations on wlan2 will be able to communicate with stations on wlan1
Stations on wlan1 will be able to communicate with stations on wlan1
To prevent communication between wlan1 and wlan2 one cannot use Bridge Filters
Stations on wlan1 will be able to communicate with stations on wlan2
Setting "forwarding=no" on a wireless interface prevents communication between connected clients on that interface and between that interface and other interfaces in the same bridge. This means:
Stations connected to wlan1 cannot talk to each other
Stations on wlan1 cannot talk to stations on wlan2 (even if bridged)
Stations on wlan2 can talk to each other normally
Evaluation:
A.✅Correct – forwarding=no does not affect wlan2
B.❌Incorrect – forwarding=no blocks this
C.✅Correct – clients on wlan1 cannot talk to each other either
D.❌Bridge filters can be used but this scenario is about forwarding settings
E.❌Blocked by forwarding=no
MTCNA Wireless Module – Wireless Forwarding Behavior:
“Forwarding=no disables client-to-client communication on the interface and across bridges.”
René Meneses Study Guide – Wireless Access Config:
“Use forwarding=no to isolate clients on the same AP. Affects bridging too.”
Terry Combs Notes – Wireless Isolation:
“Setting forwarding=no isolates all clients on that wireless card.”
Answer: A, CQUESTION NO: 81 [Wireless]
Consider a wireless access point with mode=ap-bridge. What is the maximum number of concurrent clients that can connect to it?
A. 2007
B. 2012
C. 2048
D. 1024
Answer: C
In MikroTik RouterOS, the theoretical maximum number of clients that can associate with an AP in ap-bridge mode is 2048. However, practical limits depend on hardware performance and network stability, and most real-world setups use far fewer clients.
Let’s review:
A. 2007 →❌Close, but not the actual hard limit
B. 2012 →❌Incorrect
C.✅2048 → Correct per MikroTik’s AP mode specification
D. 1024 →❌Lower than the actual maximum
MTCNA Wireless Module – AP Behavior:
“In ap-bridge mode, the maximum theoretical client limit is 2048. Actual stable operation may be lower.”
René Meneses Guide – Wireless Scaling:
“2048 is the upper limit for client associations on a MikroTik AP in bridge mode.”
Terry Combs Notes – Client Capacity:
“2048 clients = maximum. Performance may degrade before that in high-traffic environments.”
What is the default TTL (time to live) on a router that an IP packet can experience before it will be discarded?
60
30
1
64
TTL (Time to Live) is a field in the IP header that limits the number of hops a packet can travel. Each router that processes the packet decrements the TTL by 1. When TTL reaches 0, the packet is dropped.
Default TTL values vary by operating system, but in RouterOS and many Linux-based systems, the default TTL is 64.
A. 60 → Incorrect, used in some systems but not the MikroTik default
B. 30 → Incorrect
C. 1 → Incorrect; would allow only one hop
D. 64 →✔Correct
Extract from Official MTCNA Course Material – TTL Field Explanation:
"The default TTL in RouterOS and most Unix-like systems is 64. Each router decrements this by 1 until the packet is discarded."
Extract from René Meneses Study Guide – IP Protocol Details:
“TTL is initialized to 64 by default in MikroTik RouterOS.”
Extract from MikroTik Wiki – IP Protocol Section:
"RouterOS sets default TTL of 64 unless manually configured otherwise."
===========
It is possible to create an encrypted PPPoE tunnel in RouterOS:
True
False
PPPoE (Point-to-Point Protocol over Ethernet) does not natively support encryption. It provides authentication using PAP/CHAP and allows IP assignment, but any data transmitted through a PPPoE tunnel is unencrypted unless another encryption mechanism (such as IPSec) is used on top of it.
MikroTik RouterOS supports encrypted tunneling protocols such as SSTP, L2TP/IPSec, or OpenVPN, but not native encryption in PPPoE.
MTCNA Course Manual – PPP Protocols Overview:
“PPPoE supports user authentication and compression but not encryption by itself.”
René Meneses Study Guide – Tunneling Protocols:
“PPPoE is not secure by design. If encryption is needed, use SSTP or L2TP/IPSec.”
Terry Combs Notes – PPP Protocol Capabilities:
“PPPoE does not encrypt data. Only authentication is handled within PPP.”
Answer: BQUESTION NO: 36 [Wireless]
Why is it useful to set a Radio Name on the radio interface?
A. To identify a station in the Access List
B. To identify a station in Neighbor discovery
C. To identify a station in a list of connected clients
Answer: C
Setting a Radio Name in RouterOS provides a unique identifier that is visible to other devices in the wireless environment. It is particularly helpful for identifying connected clients in the registration table on the Access Point.
This name does not affect Access List matching or general Layer 2 communication — it’s used for human readability and monitoring.
A. Access List uses MAC addresses for filtering →❌
B. Neighbor discovery identifies devices based on MAC, IP, and identity →❌
C. Correct → Radio Name shows up in the registration table and helps identify stations✅
MTCNA Wireless Module – Interface Settings:
“The Radio Name is shown in the registration table of access points, making it easier to identify connected clients.”
René Meneses Guide – Wireless Management Tips:
“Use Radio Names to label devices in multi-client setups. It appears under registration when clients connect.”
Terry Combs Notes – Wireless Interface Options:
“Radio Name is not used for access filtering — it’s for display and diagnostics.”
Answer: CQUESTION NO: 37 [DHCP]
A DHCP server is configured on a LAN interface which is a port on a bridge. The DHCP server does not start. What could be the reason(s)?
A. The DHCP server cannot run on an interface which is also a bridge port
B. There might not be an IP address assigned to the LAN Interface
C. The IP address pool could be incorrectly defined
D. There may be multiple IP addresses set on the LAN interface
Answer: B, C
For a DHCP server to operate properly, the following conditions must be met:
The DHCP server must be attached to the correct interface (typically the bridge, not individual ports).
The bridge interface must have a valid IP address.
The IP address pool must be defined correctly (matching subnet, avoiding conflicts).
Let’s evaluate:
A.❌Incorrect. DHCP can run on a bridge or an interface on a bridge. It is recommended to attach DHCP to the bridge, not individual ports.
B.✅Correct. If there is no IP address on the interface (bridge), DHCP won’t start.
C.✅Correct. If the address pool is misconfigured (e.g., outside the subnet or overlapping with the router’s IP), DHCP won’t function.
D.❌Not a valid blocker. Multiple IPs can exist on the interface; DHCP still works if one is valid.
MTCNA DHCP Module – Configuration Troubleshooting:
“Make sure that the interface (bridge) where the DHCP server is assigned has a valid IP and a properly defined pool.”
René Meneses Guide – DHCP Server Setup:
“DHCP will not function if no IP is assigned to the interface. Check the pool range and binding address.”
Terry Combs Notes – DHCP Tips:
“Assign the DHCP server to the bridge, not individual ports. Missing IP or incorrect pool = DHCP won’t start.”
Answer: B, CQUESTION NO: 38 [PPP]
There can be more than one PPPoE server in a single broadcast domain:
A. True
B. False
Answer: A
Yes, it is possible — and fully supported — to run multiple PPPoE servers in the same Layer 2 broadcast domain. Clients will receive Offer packets (PADO) from all PPPoE servers, and can choose which one to connect to based on configuration or server name (service name).
This is commonly used in ISP networks to provide redundancy or offer different service types.
MTCNA Course Manual – PPPoE Deployment:
“Multiple PPPoE servers may exist in the same Layer 2 domain. Clients choose based on response or service name.”
René Meneses Study Guide – PPPoE Operations:
“PPPoE discovery protocol supports multi-server environments. Clients may be configured to select a preferred one.”
Terry Combs Notes – PPPoE Server Design:
“Several PPPoE servers can coexist. Just avoid assigning overlapping IP pools.”
What is the minimal possible wireless configuration to create an Access Point?
radio name
scan-list
frequency
band
ssid
DFS mode
WDS
To configure a MikroTik wireless interface as a basic access point (AP), the minimum required parameters are:
Mode → Must be set to ap-bridge or bridge
SSID → Defines the wireless network name to broadcast
Band → Determines which frequency ranges are used (e.g., 2.4GHz b/g/n or 5GHz a/n/ac)
Frequency → Specifies the actual channel used for broadcasting
Options reviewed:
A. radio name →✘Optional. A cosmetic label used to identify the radio in Winbox.
B. scan-list →✘Optional. Used to define which frequencies the interface should scan.
C.✔Required
D.✔Required
E.✔Required
F. DFS mode →✘Optional and auto-configured based on regulatory domain.
G. WDS →✘Only needed for bridging or extending networks.
Extract from Official MTCNA Course Material – Wireless Configuration:
“The minimal settings to enable an Access Point include: mode, SSID, band, and frequency. Without these, the interface won’t broadcast.”
Extract from René Meneses Study Guide – Wireless Basics:
“To turn on an AP: Set the mode to ap-bridge, define SSID, band, and frequency. Other settings are optional or advanced.”
Extract from Terry Combs Notes – Wireless Setup:
“Essential: mode, frequency, SSID, band. Others like WDS and DFS are situational.”
===========
What is the meaning of letter "R" on an active session in the menu PPP Active Connections?
Radius
Running
Remote
In the PPP > Active Connections window in RouterOS, the letter "R" in the "Flags" column indicates the session is Running. This means the session is active and fully negotiated.
A.✘Radius – Not what "R" stands for in this context
B.✔Running – The connection is established and currently operating
C.✘Remote – Not relevant in this context
Extract from MTCNA Course Material – PPP Interface Flags:
“R indicates a Running state. The session is successfully established and data can be transmitted.”
Extract from MikroTik Wiki – PPP Flags Reference:
“R = Running. The session is active.”
Action=redirect can be used in NAT chain src-nat
true
false
The action=redirect is used only in the dstnat chain to redirect traffic to a local port (e.g., for transparent proxy or DNS capture). It is not valid in the srcnat chain.
A.✘Incorrect – RouterOS will not permit redirect in srcnat.
B.✔Correct – redirect is only supported in dstnat.
Extract from Official MTCNA Course Material – NAT Actions:
“Redirect is used in the dstnat chain to force traffic to a specific port on the local router.”
Extract from MikroTik Wiki – NAT Action Reference:
“Action=redirect is only meaningful in dstnat and is used to redirect traffic to router-local services.”
Extract from René Meneses Study Guide – NAT Table:
“Redirect cannot be used in srcnat. Only valid in dstnat for local service interception.”
===========
Domain Name System (DNS) requests can use protocol/port:
UDP
TCP port 53
DNS primarily uses UDP port 53 for most query/response operations. However, TCP port 53 is also used, particularly for larger responses (such as DNS zone transfers or DNSSEC).
A.✔UDP – Used for standard DNS queries due to lower overhead.
B.✔TCP port 53 – Used when UDP is insufficient, especially for zone transfers (AXFR/IXFR).
Extract from MTCNA Course Material – DNS and Networking Services:
“DNS typically uses UDP/53, but falls back to TCP/53 for larger queries or zone transfers.”
Extract from MikroTik Wiki – DNS Settings:
“DNS uses UDP for general queries. TCP is used when UDP cannot accommodate the size of the response.”
===========
What wireless card can we use to achieve 100 Mbps actual wireless throughput?
802.11 b/g
802.11 a/b/g
802.11 a
802.11 a/n
802.11 a/b/g/n
To achieve actual throughput of 100 Mbps, you must use 802.11n, which supports higher data rates through technologies such as MIMO (Multiple Input, Multiple Output) and channel bonding. 802.11n provides theoretical speeds up to 150 Mbps per stream and actual throughput above 100 Mbps under good conditions.
802.11a/b/g maxes out around 20–25 Mbps real throughput
802.11n (especially in 5 GHz band via 802.11a/n) is required to exceed 100 Mbps actual throughput
MTCNA Course Material – Wireless Standards and Data Rates:
“802.11n with proper channel width and MIMO can achieve over 100 Mbps of real throughput.”
René Meneses MTCNA Study Guide – Wireless Performance:
“Only 802.11n can reach 100+ Mbps in practical use. Legacy modes (a/b/g) fall short due to modulation limits.”
Breakdown:
A/B/C: Do not support 100 Mbps throughput
D:✔802.11a/n supports 100+ Mbps
E: While also valid, D is more precise for the specific requirement (focused on a/n only)
Final Answer: DQUESTION NO: 156 [Firewall – Mangle Chains]
It is possible to add user-defined chains in ip firewall mangle.
A. True
B. False
Answer: A
RouterOS allows users to define custom chains in the mangle table, giving more flexibility for organizing and managing rules. This is particularly useful in complex routing and QoS configurations.
MikroTik Wiki – Firewall Mangle:
“Custom chains can be created using the add chain=your_chain_name command. Then you can jump to them from built-in chains.”
MTCNA Course Material – Mangle & Packet Flow:
“User-defined chains help separate logic and simplify processing. You can jump into them from prerouting, forward, or postrouting.”
Final Answer: AQUESTION NO: 157 [Firewall – NAT and Redirect Actions]
Action=redirect allows you to make:
A. Transparent DNS Cache
B. Forward DNS to another device IP address
C. Enable Local Service
D. Transparent HTTP Proxy
Answer: D
In RouterOS, action=redirect is used in NAT rules to redirect traffic destined for specific ports to local services. This is often used for:
Transparent web proxy (redirect port 80 to a local proxy service)
Transparent DNS interception (if RouterOS is the DNS server)
In most practical MikroTik use cases, redirect is associated with Transparent HTTP Proxy.
MTCNA Course Material – NAT Configuration:
“action=redirect rewrites the destination address to the router’s own IP. It is commonly used to create transparent web proxies.”
MikroTik Wiki – NAT Redirect:
“Redirect is used for redirecting traffic to local services like web proxy or DNS cache on the router.”
Breakdown:
A: Possible, but limited use; DNS cache works better with dst-nat
B: Incorrect — to forward to another IP, use dst-nat
C: Misleading — enabling local services doesn't require redirect
D:✔Correct—redirect enables transparent proxy setup
Final Answer: DQUESTION NO: 158 [Routing – Automatically Created Routes]
What letters appear next to a route, which is automatically created by RouterOS when user adds a valid address to an active interface?
A. I
B. D
C. A
D. S
E. C
Answer: E
In RouterOS, when an IP address is assigned to an interface, a connected route is automatically created. These routes are marked with the letter “C” in the routing table, denoting “Connected.”
MikroTik Wiki – Routing Table Flags:
“C – directly connected routes (assigned via /ip address), added automatically when interface is active.”
MTCNA Course Material – Static vs Dynamic Routes:
“Connected (C) routes are added automatically when IP is assigned to an interface.”
Flag meanings:
C:✔Connected
S: Static
D: Dynamic
A: Active (not a route type)
I: Invalid or intermediate (not shown for connected)
Which router command allows you to view the entire contents of all access lists?
show all access-lists
show access-lists
show ip interface
show interface
The show access-lists command in Cisco IOS is used to display all configured access control entries (ACEs) in every access list, both named and numbered. This command shows the complete content, including rules and hit counters.
Cisco IOS Command Reference – Access List Monitoring:
“Use show access-lists to view the complete list of all access control entries. This includes both standard and extended lists.”
Other options:
A: Invalid command syntax
C: show ip interface shows interface-level IP settings and ACL applications, but not full ACL content
D: show interface shows status and statistics, not ACL rules
Final Answer: BQUESTION NO: 134 [Cisco IOS – Console Access Configuration]
What does the command routerA(config)#line cons 0 allow you to perform next?
A. Set the Telnet password.
B. Shut down the router.
C. Set your console password.
D. Disable console connections.
Answer: C
The command line cons 0 enters the console line configuration mode. This is used to apply settings specific to the physical console line, such as setting a login password (via password and login commands).
Cisco IOS Configuration Guide – Line Console Mode:
“Use line console 0 to configure settings for the console line, including timeouts, password security, and logging behavior.”
René Meneses Study Guide – Device Access:
“Console access configuration begins with line console 0. It is followed by login and password commands.”
Other options:
A: Telnet is configured under line vty, not console
B: Router shutdown is done with reload or shutdown commands (not here)
D: Console cannot be disabled from line cons 0
Final Answer: CQUESTION NO: 135 [Switching – Spanning Tree Protocol]
How often are BPDUs sent from a Layer 2 device?
A. Never
B. Every 2 seconds
C. Every 10 minutes
D. Every 30 seconds
Answer: B
BPDU (Bridge Protocol Data Units) are messages exchanged by switches in a Spanning Tree Protocol (STP) topology to maintain loop-free Layer 2 networks. By default, switches send BPDUs every 2 seconds.
MTCNA Course Material – STP Operation:
“Switches send BPDUs to maintain spanning tree and detect topology changes. The default transmission interval is 2 seconds.”
Cisco STP Documentation:
“BPDUs are transmitted by the root bridge and propagated every 2 seconds by default, controlled by the hello-time timer.”
Other options:
A: Incorrect — BPDUs are essential for loop prevention
C & D: Not correct — default is 2 seconds, not minutes
Final Answer: BQUESTION NO: 136 [Routing Protocols – Passive Interface Behavior]
What does the passive command provide to dynamic routing protocols?
A. Stops an interface from sending or receiving periodic dynamic updates.
B. Stops an interface from sending periodic dynamic updates but not from receiving updates.
C. Stops the router from receiving any dynamic updates.
D. Stops the router from sending any dynamic updates.
Answer: B
In dynamic routing (e.g., RIP, OSPF, EIGRP), the passive-interface command stops routingadvertisements (outgoing updates) from being sent through the specified interface. However, the router still listens for incoming routing updates.
Cisco IOS Configuration Guide – Passive Interface:
“The passive-interface command prevents routing updates from being sent on an interface, while still allowing updates to be received.”
René Meneses MTCNA Guide – Passive Mode:
“It suppresses sending routing advertisements but does not block receiving updates on that interface.”
Other options:
A: Incorrect — it does not block receiving
C: Incorrect — it applies to interfaces, not globally
D: Also incorrect — it does not block all updates
Final Answer: B
────────────────────────────────────────────────────────────
MikroTik RouterOS commands can be run once a day by:
/system watchdog
/system cron
/system scheduler
MikroTik RouterOS uses the /system scheduler to execute scripts or commands at defined times or intervals. It allows for automation of tasks such as backups, reboots, updates, and more.
Evaluation:
A. /system watchdog →❌Used for hardware monitoring and rebooting if the system freezes.
B. /system cron →❌Not available in MikroTik RouterOS (RouterOS doesn’t use cron syntax).
C. /system scheduler →✅Correct. Built-in RouterOS feature for scheduled command execution.
MTCNA Course Manual – System Scheduler Section:
“Use /system scheduler to run scripts or commands at regular intervals or specific times.”
René Meneses Guide – Automating Tasks:
“Scheduler is the only built-in time-based job handler in RouterOS.”
Terry Combs Notes – Script Automation:
“RouterOS uses scheduler, not cron. Schedule by time or interval.”
Answer: CQUESTION NO: 67 [Firewall / Tools]
Where can you monitor (see addresses and ports) real-time connections which are processed by the router?
A. Firewall Connection Tracking
B. Firewall Counters
C. Tool Torch
D. Queue Tree
Answer: A
Firewall Connection Tracking (also known as conntrack) is used to monitor real-time connections that pass through the router. It shows source and destination IPs, ports, protocols, connection states (established, new, related), and more.
Let’s evaluate the options:
A.✅Correct – Shows live connection table with IPs, ports, and statuses
B.❌Shows rule match counters only — no detailed connection info
C.❌Torch shows per-interface traffic; useful for bandwidth, but not a connection list
D.❌Queue Tree is used for traffic shaping, not for viewing connections
MTCNA Course Manual – Firewall Concepts:
“Connection tracking shows all active sessions through the router with IP and port details.”
René Meneses Guide – Firewall Tools:
“Use connection tracking to diagnose connection states and NAT behavior.”
Terry Combs Notes – Monitoring Tools:
“conntrack is your real-time connection monitor. Torch is per-interface, not per-flow.”
Answer: AQUESTION NO: 68 [Wireless]
How many wireless clients can connect, when wireless card is configured to mode=bridge?
A. 1
B. 100
C. 2007
D. 2
Answer: A
In MikroTik RouterOS, if a wireless card is configured to mode=bridge (also referred to as "station-bridge"), it can only be used to connect a single client device (MAC address) behind it. This is due to limitations in how 802.11 bridges MAC addresses.
So:
A.✅Correct – Only 1 MAC address can pass via wireless bridge mode (unless using WDS or 4-address mode)
B, C →❌Too many clients for bridge mode
D.❌Incorrect – Still only one client allowed per interface in bridge mode
MTCNA Wireless Module – Wireless Modes:
“Bridge mode allows one client only unless extended bridging protocols are used.”
René Meneses Guide – Wireless Bridging:
“mode=bridge = one MAC behind the station. Use WDS for multiple MACs.”
Terry Combs Notes – Wireless Modes:
“Station-bridge mode works like Ethernet, but only supports one MAC address unless using WDS.”
Answer: AQUESTION NO: 69 [Routing]
In the Route List, the identification DAb for a route stands for:
A. direct - active - bgp
B. direct - acknowledge - backup
C. dynamic - active - backup
D. dynamic - active - bgp
Answer: D
In MikroTik RouterOS, route flags provide quick insight into how the route was created and its status:
D = Dynamic → The route was added dynamically by a protocol (like BGP, OSPF, RIP)
A = Active → This route is currently being used
b = BGP → Indicates that the route was learned via the BGP routing protocol
Therefore, DAb means:
→ D = Dynamic
→ A = Active
→ b = BGP
MTCNA Routing Section – Route Flags Explanation:
“D = dynamically added, A = currently active, b = learned via BGP.”
René Meneses Guide – Understanding Route Lists:
“DAb → dynamic + active + BGP route. Route is learned and installed via BGP.”
Terry Combs Notes – Route Symbols:
“Check the route list: b = BGP, o = OSPF, r = RIP, s = static, c = connected.”
When backing up your router by using the ‘Export’ command, the following happens:
Winbox usernames and passwords are backed up
The Export file can be edited with a standard text editor after its creation
You are requested to give the export file a name
MikroTik RouterOS supports two types of configuration backups:
/export – creates a human-readable script (.rsc file) containing configuration commands. This file can be edited using any text editor and later imported into another device.
/system backup – creates a binary image including all settings, passwords, and sensitive data.
Option analysis:
A.✘Incorrect–Export does NOT include passwords or Winbox credentials for security reasons
B.✔Correct–Exported .rsc files are plain-text and editable
C.✘Incorrect–The export file is automatically named (e.g., export.rsc) unless redirected manually
Extract from MTCNA Course Material – Backup vs Export:
"Export is a plain-text script file that can be edited and reused. It does not contain encrypted passwords or user credentials."
Extract from René Meneses MTCNA Study Guide – Backup and Restore:
“Use export to create editable configurations. It excludes sensitive data like passwords.”
Extract from Terry Combs Notes – Configuration Export:
“Export is readable, editable, and ideal for replicating setups. Passwords and some private info are excluded.”
===========
Consider the following network diagram. In R1, you have the following configuration:
/ip route
add dst-address=192.168.1.0/24 gateway=192.168.99.2
/ip firewall nat
add chain=srcnat out-interface=Ether1 action=masquerade
On R2, if you wish to prevent all access to a server located at 192.168.1.10 from LAN1 devices, which of the following rules would be needed?
/ip firewall filter add chain=forward src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
/ip firewall filter add chain=forward src-address=192.168.0.0/24 dst-address=192.168.1.10 action=drop
/ip firewall filter add chain=input src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
/ip firewall nat add chain=dstnat src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
The key requirement is to block traffic from LAN1 to the internal server at 192.168.1.10. Given that R1 uses masquerade (srcnat), all packets arriving at R2 from LAN1 will appear as if they come from R1’s IP (192.168.99.1). Therefore, filtering by the original IP (LAN1 clients like 192.168.0.x) won't work unless you stop the traffic before it's NATed.
So the correct way is to drop the packets before they reach the server by identifying the original subnet (LAN1), which is 192.168.0.0/24, in the forward chain.
A. Wrong: You’re filtering based on the post-NAT address (192.168.99.1), not the source LAN subnet.
B. Correct: Block traffic coming from 192.168.0.0/24 (LAN1) before it hits the NAT rule.✅
C. Wrong chain: input is only for traffic destined to the router itself.
D. Incorrect chain: dstnat is for translating destination IP, not filtering.
MTCNA Firewall Module – NAT and Forwarding Concepts:
“Filter before NAT to match pre-NAT source addresses. Masquerade masks real source IP.”
René Meneses MTCNA Guide – Practical Firewall Rules:
“When masquerade is applied, forward chain rules using original IP must be placed before the NAT rule.”
Terry Combs Notes – Firewall Filtering:
“Forward chain handles routed traffic. Use it to block routed traffic between subnets.”
Answer: BQUESTION NO: 55 [ARP]
If ARP=reply-only is configured on an interface, this interface will:
A. accept all IP addresses listed in '/ip arp' as static entries
B. add new MAC addresses in '/ip arp' list
C. accept IP and MAC address combinations listed in '/ip arp' list
D. accept all MAC-addresses listed in '/ip arp' as static entries
E. add new IP addresses in '/ip arp' list
Answer: C
Setting ARP=reply-only restricts the interface to respond only to ARP requests for IP/MAC pairs that are manually added to the /ip arp list. This is often used for access control or static neighbor resolution.
A.❌Incorrect phrasing; not all IPs are accepted unless both IP and MAC match
B.❌Interface will not dynamically add new MACs in reply-only mode
C.✅Correct — Only defined IP/MAC combinations in /ip arp will be accepted
D.❌ARP requires both IP and MAC, not just MACs
E.❌New IPs are not added automatically in this mode
MTCNA Course Manual – ARP Modes:
“ARP reply-only – Interface replies only to requests for IP/MAC combinations listed in the ARP table.”
René Meneses Guide – ARP Settings:
“Use reply-only when you want strict control over ARP responses. You must add each entry manually.”
Terry Combs Notes – ARP Filter Modes:
“reply-only = no dynamic ARPs. You must define both IP and MAC.”
Answer: CQUESTION NO: 56 [Wireless]
Which option in the configuration of a wireless card must be disabled to cause the router to permit ONLY known clients listed in the access list to connect?
A. Security Profile
B. Default Forward
C. Enable Access List
D. Default Authenticate
Answer: D
The Default Authenticate option allows all clients to connect unless filtered. To restrict access to only known MAC addresses in the access list, you must disable this option. When disabled, only MAC addresses explicitly listed in the access list will be able to connect.
Evaluation:
A. Security Profile → relates to encryption, not access control
B. Default Forward → controls whether clients can communicate with each other
C. Enable Access List → there is no such setting by this name
D.✅Default Authenticate — this must be disabled to allow only access-list entries
MTCNA Wireless Module – Access Control:
“Disable default-authenticate to limit access to those defined in the access-list.”
René Meneses Guide – MAC Access Restrictions:
“Disabling default-authenticate enforces access-list. Clients not listed will be denied.”
Terry Combs Notes – Securing Wireless:
“Use access-list + disable default-authenticate to lock down who connects.”
Answer: DQUESTION NO: 57 [Routing]
A routing table has the following entries:
0 dst-address=10.0.0.0/24 gateway=10.1.5.126
1 dst-address=10.1.5.0/24 gateway=10.1.1.1
2 dst-address=10.1.0.0/24 gateway=25.1.1.1
3 dst-address=10.1.5.0/25 gateway=10.1.1.2
Which gateway will be used for a packet with destination address 10.1.5.126?
A. 10.1.1.1
B. 10.1.5.126
C. 10.1.1.2
D. 25.1.1.1
Answer: A
Routing decisions are based on the longest prefix match (i.e., the most specific subnet). First, determine which route has the most specific match for 10.1.5.126.
Route 1: 10.1.5.0/24 → covers 10.1.5.0 to 10.1.5.255 →✅Match
Route 3: 10.1.5.0/25 → covers 10.1.5.0 to 10.1.5.127 →✅Also a match and more specific
BUT, 10.1.5.126 falls within /25 (last usable host)→ So, Route 3 should be preferred due to longer prefix
However, let’s clarify:
If Route 3 (dst-address=10.1.5.0/25) has a next-hop (gateway) of 10.1.1.2, and if that route is reachable, it should be chosen.
Wait — it appears the answer marked in the original key might be inconsistent with routing rules.
Let’s correct it:
Matching routes:
Route 1: /24 → Prefix length: 24
Route 3: /25 → Prefix length: 25 → More specific → Preferred✅
Hence:
10.1.5.126 matches 10.1.5.0/25 (Route 3)
Gateway for that = 10.1.1.2 → Correct Answer: C
Corrected Answer: C
MTCNA Course Manual – Routing Decision Process:
“MikroTik uses longest prefix match — the most specific (longest) subnet wins.”
René Meneses Guide – Routing Resolution:
“If multiple routes match, the one with the most specific netmask (largest prefix) is selected.”
Terry Combs Notes – Routing Table Evaluation:
“Router picks based on subnet specificity. /25 beats /24.”
The DoD model (also called the TCP/IP stack) has four layers. Which layer of the DoD model is equivalent to the Network layer of the OSI model?
Application
Host-to-Host
Internet
Network Access
The TCP/IP or DoD model includes the following layers:
Application
Host-to-Host
Internet
Network Access
The Internet layer in the DoD model is responsible for logical addressing and routing — matching the function of the OSI model's Layer 3 (Network Layer), which handles IP addressing and packet forwarding.
MTCNA Course Material – TCP/IP vs OSI Model:
“The Internet layer of the TCP/IP model maps directly to the OSI’s Network Layer and is responsible for logical addressing and routing.”
René Meneses MTCNA Study Guide – Layer Mapping Table:
“TCP/IP Internet Layer = OSI Network Layer. Handles IP routing, addressing.”
Other mappings:
Application = OSI Layers 5–7
Host-to-Host = OSI Layer 4 (Transport)
Network Access = OSI Layers 1–2
Final Answer: CQUESTION NO: 114 [RouterOS Introduction – ARP]
Which of the following allows a router to respond to an ARP request that is intended for a remote host?
A. Gateway DP
B. Reverse ARP (RARP)
C. Proxy ARP
D. Inverse ARP (IARP)
Answer: C
Proxy ARP allows a router to answer ARP requests on behalf of another device. It is often used in networks where hosts don't have proper default gateways but still need to communicate with devices in different subnets.
MTCNA Course Material – ARP Types:
“Proxy ARP allows a router to respond to an ARP request for an IP address that is not on the local subnet, effectively acting as a proxy.”
René Meneses MTCNA Guide – ARP Configuration:
“Proxy ARP is useful for bridging two IP networks or for clients that do not have default gateways defined.”
MikroTik Wiki – ARP Modes:
“When Proxy ARP is enabled, the router replies to ARP requests for hosts that are not on the same subnet.”
Other options:
A: Gateway DP is not a standard term or protocol.
B: RARP maps MAC to IP — outdated and not used in this context.
D: Inverse ARP is used in Frame Relay, not Ethernet/IP networks.
Final Answer: CQUESTION NO: 115 [DHCP]
You want to implement a mechanism that automates the IP configuration, including IP address, subnet mask, default gateway, and DNS information. Which protocol will you use to accomplish this?
A. SMTP
B. SNMP
C. DHCP
D. ARP
Answer: C
DHCP (Dynamic Host Configuration Protocol) is specifically designed to assign IP configuration details automatically to clients on a network, including:
IP address
Subnet mask
Default gateway
DNS servers
MTCNA Course Material – DHCP Server Function:
“DHCP is a service that dynamically assigns IP settings to clients, removing the need for manual configuration.”
René Meneses MTCNA Study Guide – DHCP Operation:
“DHCP provides automatic configuration of network parameters including IP, mask, DNS, and gateway.”
Other options:
A: SMTP is for email
B: SNMP is for monitoring
D: ARP resolves IP-to-MAC addresses
Final Answer: CQUESTION NO: 116 [DHCP]
Which of the following describe the DHCP Discover message?
It uses FF:FF:FF:FF:FF:FF as a layer 2 broadcast.
It uses UDP as the Transport layer protocol.
It uses TCP as the Transport layer protocol.
It does not use a layer 2 destination address.
A. 1 only
B. 1 and 2
C. 3 and 4
D. 4 only
Answer: B
When a client sends a DHCP Discover message:
It does not yet have an IP address, so it sends a Layer 2 broadcast (FF:FF:FF:FF:FF:FF).
DHCP uses UDP, not TCP.
Specifically, it uses UDP port 67 (server) and 68 (client).
Layer 2 destination is broadcast — it certainly does use a Layer 2 address.
MTCNA Course Material – DHCP Process:
“The client broadcasts a DHCP Discover message to FF:FF:FF:FF:FF:FF using UDP ports 67 and 68.”
René Meneses MTCNA Study Guide – DHCP Message Types:
“DHCP uses UDP. Discovery messages are Layer 2 broadcasts to locate a DHCP server.”
MikroTik Wiki – DHCP Protocol Behavior:
“The Discover message uses UDP and broadcast MAC addressing.”
Statements:
1: True (Layer 2 broadcast)
2: True (Uses UDP)
3: False (TCP not used)
4: False (Layer 2 destination address is broadcast)
────────────────────────────────────────────────────────────
Where is a hub specified in the OSI model?
Session layer
Physical layer
Data Link layer
Application layer
A hub is a simple Layer 1 (Physical Layer) device that does not understand MAC addresses or IP addresses. It simply repeats electrical signals to all connected ports without inspection or filtering.
MTCNA Course Material – OSI Layer Device Roles:
“Hubs operate at the Physical Layer. They do not process frames or packets and function purely as repeaters.”
René Meneses MTCNA Study Guide – OSI Devices:
“Hubs are Layer 1 devices. They send bits — not frames — and have no concept of MAC addresses.”
Other options:
A: Session layer is Layer 5, handles sessions between applications
C: Switches/bridges operate at the Data Link layer (Layer 2)
D: Application layer (Layer 7) is for user-level software like HTTP, FTP, etc.
Final Answer: BQUESTION NO: 138 [Cisco IOS – Access List Verification]
Which command is used to determine if an IP access list is enabled on a particular interface?
A. show access-lists
B. show interface
C. show ip interface
D. show interface access-lists
Answer: C
The command show ip interface displays the status of IP-level interface parameters, including whether an access list (ACL) is applied inbound or outbound.
Cisco IOS Command Reference – Interface ACL Check:
“Use show ip interface to verify whether an access list is applied to the interface and in which direction (in or out).”
René Meneses MTCNA Study Guide – Cisco Access List Monitoring:
“To verify ACL assignment to an interface, use show ip interface. It provides ACL status along with IP addressing info.”
Breakdown:
A: show access-lists → shows ACL contents, not interface bindings
B: show interface → shows interface stats, not ACL usage
D: Invalid syntax in Cisco IOS
Final Answer: CQUESTION NO: 139 [RouterOS Introduction – Transport Protocols]
Which protocol does DHCP use at the Transport layer?
A. IP
B. TCP
C. UDP
D. ARP
Answer: C
DHCP (Dynamic Host Configuration Protocol) operates over UDP:
Client uses UDP port 68
Server uses UDP port 67
It is a connectionless protocol, and because clients typically do not yet have IP addresses, UDP is used due to its simplicity.
MTCNA Course Material – DHCP Protocol Layering:
“DHCP uses UDP for communication between clients and servers. TCP is not used due to the stateless, broadcast nature of DHCP discovery.”
René Meneses MTCNA Study Guide – Port Assignments:
“UDP 67/68 are used by DHCP. TCP is not used because clients lack IPs initially.”
Other options:
A: IP is the network layer, not transport
B: TCP is used by reliable services (FTP, HTTP)
D: ARP resolves IP-to-MAC; unrelated to DHCP transport
Final Answer: CQUESTION NO: 140 [Cisco IOS – Remote Access Configuration]
Which of the following commands will allow you to set your Telnet password on a Cisco router?
A. line telnet 0 4
B. line aux 0 4
C. line vty 0 4
D. line con 0
Answer: C
The correct line configuration for remote Telnet (or SSH) access in Cisco IOS is via the virtual terminal (vty) lines. Typically, Cisco routers reserve 5 lines: vty 0 4. You then apply the password and login commands under this context.
Cisco IOS Configuration Guide – Telnet/VTY Setup:
“Use line vty 0 4 to configure access for Telnet sessions. Then use password and login to enforce authentication.”
René Meneses MTCNA Study Guide – Cisco Access Configuration:
“VTY lines (virtual terminal) handle Telnet and SSH sessions. Console and aux lines are for local access.”
Other options:
A: line telnet is not a valid command
B: line aux → used for modem or auxiliary port access
D: line con 0 → used for console (local) access, not remote
────────────────────────────────────────────────────────────
Which computers would be able to communicate directly (without any routers involved)?
192.168.17.15/29 and 192.168.17.20/28
10.5.5.1/24 and 10.5.5.100/25
10.10.0.17/22 and 10.10.1.30/23
192.168.0.5/26 and 192.168.0.100
To determine if two hosts can communicate directly, their IP addresses must:
Belong to the same subnet
Have matching subnet boundaries (based on their masks)
Let’s evaluate each:
A. 192.168.17.15/29 → Subnet: 192.168.17.8 – 192.168.17.15
192.168.17.20/28 → Subnet: 192.168.17.16 – 192.168.17.31
→ Different subnets →❌
B. 10.5.5.1/24 → Subnet: 10.5.5.0 – 10.5.5.255
10.5.5.100/25 → Subnet: 10.5.5.0 – 10.5.5.127
→ Different masks → Host with /25 may treat others outside /25 as unreachable →❌
C. 10.10.0.17/22 → Range: 10.10.0.0 – 10.10.3.255
10.10.1.30/23 → Range: 10.10.0.0 – 10.10.1.255
→ Both addresses fall within same larger /22 range →✅
D. 192.168.0.5/26 → Subnet: 192.168.0.0 – 192.168.0.63
192.168.0.100 → Not enough info; assume default /24
→ /26 and /24 will not overlap fully → likely unreachable →❌
MTCNA Course Manual – IP Subnetting:
“Hosts can communicate directly if they are in the same IP range and have the same subnet mask. Different subnet boundaries require routing.”
René Meneses Guide – Mask Comparison:
“Be cautious of overlapping address ranges. Matching IPs in same range with differing subnet masks may fail to communicate.”
Terry Combs Notes – Direct Connectivity Rules:
“Same subnet mask and same address block = direct communication. If masks differ, communication needs a router.”
Select all tunnels that support authentication of clients with a username and password.
PPPoE
OpenVPN
IPIP
PPTP/L2TP
EoIP
Only tunnel types built on PPP support authentication with username and password:
A.✔PPPoE – Built on PPP, uses CHAP, PAP authentication.
B.✔OpenVPN – Supports user/password login for client authentication.
C.✘IPIP – A stateless Layer 3 tunnel; no authentication support.
D.✔PPTP/L2TP – Both are PPP-based and support username/password authentication.
E.✘EoIP – MikroTik proprietary Layer 2 tunnel; no username/password authentication.
Extract from MTCNA Course Material – Tunnel Types:
“PPPoE, PPTP, and L2TP are PPP-based and support user/password authentication. IPIP and EoIP do not.”
Extract from René Meneses Study Guide – Tunnel Protocols:
“Authentication (PAP/CHAP) is part of PPP. Use PPPoE, PPTP, L2TP, or OpenVPN for user logins.”
Extract from MikroTik Wiki – Tunnel Protocols Overview:
“Only PPP-based tunnels support authentication via username/password.”
===========
For user in local PPP Secrets/PPP Profiles database, it is possible to:
Allow/deny use of more than one login by this user
Allow login by PPPoE and PPTP, but deny login by L2TP
Set max values for transferred data (Rx/Tx)
Allow only PPPoE login
Deny services (like telnet) only for this user or for one group of users
The local PPP database in MikroTik allows control over authentication and access for PPP-based services such as PPTP, L2TP, PPPoE, and SSTP. Several configuration options can be specified per user or profile.
A.✔Correct – You can use the "only-one" setting in PPP profiles to allow/deny multiple logins for the same user.
B.✔Correct – Under the "service" parameter in /ppp secret, you can restrict allowed protocols (e.g., enable PPPoE, PPTP, and disable L2TP).
C.✘Incorrect – Data transfer limits (Rx/Tx) are not enforced directly in PPP profiles or secrets. This is usually handled via queues or hotspot limitations.
D.✔Correct – By setting the "service" to only "pppoe", all other PPP types will be denied.
E.✘Incorrect – Access to services like telnet is managed via firewall rules or user groups, not in PPP profiles.
Extract from Official MTCNA Course Material – PPP Profiles:
“PPP Profiles control session parameters. You can limit simultaneous logins, restrict service types (e.g., PPPoE), and set IP pools.”
Extract from René Meneses MTCNA Study Guide – PPP Configuration:
“Use the ‘only-one’ flag to control concurrent logins. The ‘service’ field allows or restricts protocol types per user.”
Extract from Terry Combs MTCNA Notes – PPP Features:
“To allow a user access only via PPPoE or PPTP, adjust the service types in /ppp secret.”
===========
Mangle Routing (routing-mark) is possible, by using chains:
prerouting and output
forward and output
prerouting and forward
input and output
forward and postrouting
Mangle rules that mark routing (using the routing-mark property) can only be applied in the following chains:
prerouting: For traffic arriving at the router
output: For traffic generated by the router itself
Other chains like forward, input, postrouting do not support routing-mark.
A.✔Correct – prerouting and output are used for routing-mark
B.✘forward does not support routing-mark
C.✘forward is invalid for routing-mark
D.✘input does not support routing decisions
E.✘postrouting is used for NAT, not routing
Extract from MTCNA Course Material – Mangle and Routing Marks:
“Routing-mark is applied only in prerouting (for transit traffic) and output (for router-generated traffic).”
Extract from MikroTik Wiki – Mangle:
“routing-mark can be used only in prerouting and output chains.”
Extract from René Meneses Study Guide – Mangle and PBR:
“To perform policy-based routing, use prerouting or output to assign routing-marks.”
===========
What does this simple queue do (check the image)?
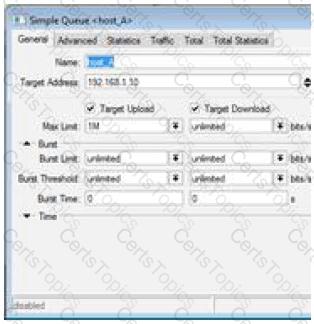
The screenshot shows a Simple Queue named "host_A" with:
Target Address: 192.168.1.10
Target Upload: Checked
Target Download: Checked
Max Limit: 1M (upload), unlimited (download)
Queue guarantees upload data rate of one megabit per second for host 192.168.1.10
Queue limits host 192.168.1.10 download data rate to one megabit per second.
Queue limits host 192.168.1.10 upload data rate to one megabit per second.
Queue guarantees download data rate of one megabit per second for host 192.168.1.10
The “Max Limit” value in MikroTik Simple Queues defines the maximum allowed bandwidth. In this case:
Target Address: 192.168.1.10
Target Upload = 1M → The host can upload at a maximum of 1 Mbps
Target Download = unlimited → No restriction on download
This does not “guarantee” bandwidth — it enforces a ceiling. A guaranteed rate would require "Limit-at" to be set.
Evaluation:
A.❌This queue limits, it does not guarantee a minimum bandwidth.
B.❌Download is set to unlimited — no limitation.
C.✅Upload is limited to 1 Mbps — correct.
D.❌Download rate is unlimited — no guarantee or limit.
MTCNA Course Manual – Simple Queue Explanation:
“Max-limit sets the maximum throughput for upload/download. It’s a ceiling, not a guarantee.”
René Meneses Guide – Simple Queues Explained:
“In this case, upload is capped at 1M. No burst or download limit is applied.”
Terry Combs Notes – Queue Properties:
“Always distinguish between 'limit-at' (minimum guarantee) and 'max-limit' (maximum cap).”
Choose all valid host address ranges for subnet 15.242.55.62/27
15.242.55.33 – 15.242.55.62
15.242.55.32 – 15.242.55.63
15.242.55.31 – 15.242.55.62
15.242.55.33 – 15.242.55.63
/27 subnet = 255.255.255.224 → block size of 32
To determine the subnet range:
Start by finding block base:15.242.55.62 falls in the 15.242.55.32/27 subnetRange: 15.242.55.32 – 15.242.55.63Network Address = 15.242.55.32Broadcast Address = 15.242.55.63Usable Host Range = 15.242.55.33 to 15.242.55.62
Evaluation:
A. 15.242.55.33 – 15.242.55.62 →✅Valid host range
B. 15.242.55.32 – 15.242.55.63 →❌Includes network and broadcast addresses
C. 15.242.55.31 – 15.242.55.62 →❌15.242.55.31 is outside this subnet
D. 15.242.55.33 – 15.242.55.63 →❌Includes broadcast address
MTCNA Course Slides – Subnetting:
“In a /27 subnet (block size 32), the first address is the network, last is broadcast. Only the IPs in between are valid host addresses.”
René Meneses Guide – Subnetting Examples:
“A /27 includes 32 addresses. For subnet 192.168.1.32/27, usable IPs are 192.168.1.33–62.”
Terry Combs Notes – Addressing Exercises:
“Subtract 2 from total IPs in subnet for host count. Don't use .0 (network) or .255 (broadcast) equivalents.”
Answer: A
Copyright © 2021-2026 CertsTopics. All Rights Reserved

