Your JIMS server is unable to view event logs.
Which two actions would you take to solve this issue? (Choose two.)
Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
Which sequence does an SRX Series device use when implementing stateful session security policies using Layer 3 routes?
You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
Which two statements are true about the vSRX? (Choose two.)
Exhibit
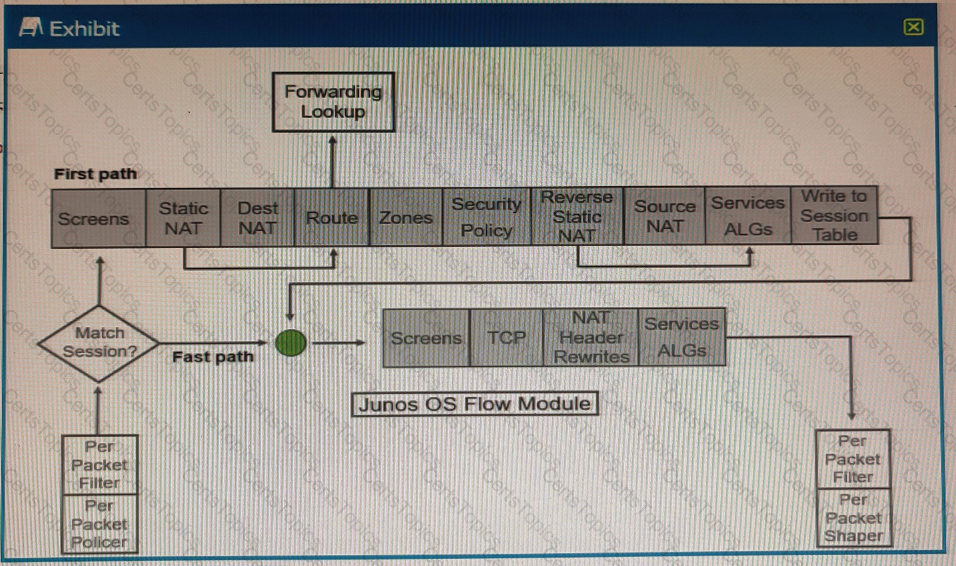
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Exhibit
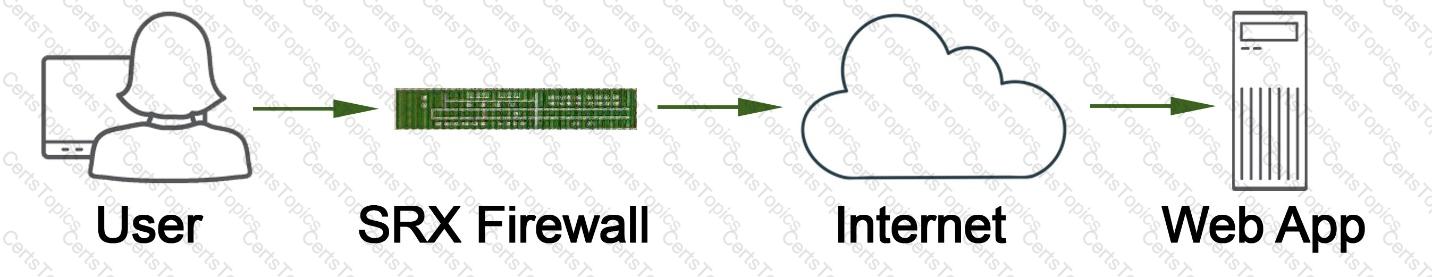
Referring to the exhibit, which two statements describe the type of proxy used? (Choose two.)
You want to deploy a virtualized SRX in your environment.
In this scenario, why would you use a vSRX instead of a cSRX? (Choose two.)
Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
Which statement defines the function of an Application Layer Gateway (ALG)?
You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
Click the Exhibit button.
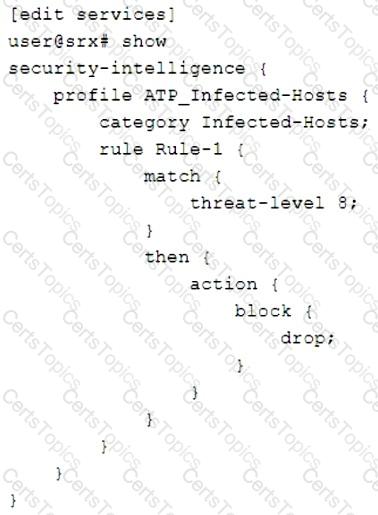
Referring to the exhibit, what will the SRX Series device do in this configuration?
Click the Exhibit button.
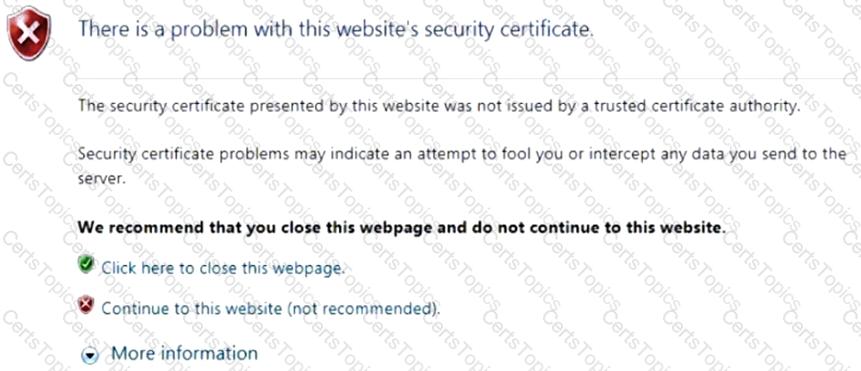
You have implemented SSL client protection proxy. Employees are receiving the error shown in the exhibit.
How do you solve this problem?
How does the SSL proxy detect if encryption is being used?
You are implementing an SRX Series device at a branch office that has low bandwidth and also uses a cloud-based VoIP solution with an outbound policy that permits all traffic.
Which service would you implement at your edge device to prioritize VoIP traffic in this scenario?
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
Which method does the loT Security feature use to identify traffic sourced from IoT devices?
Exhibit
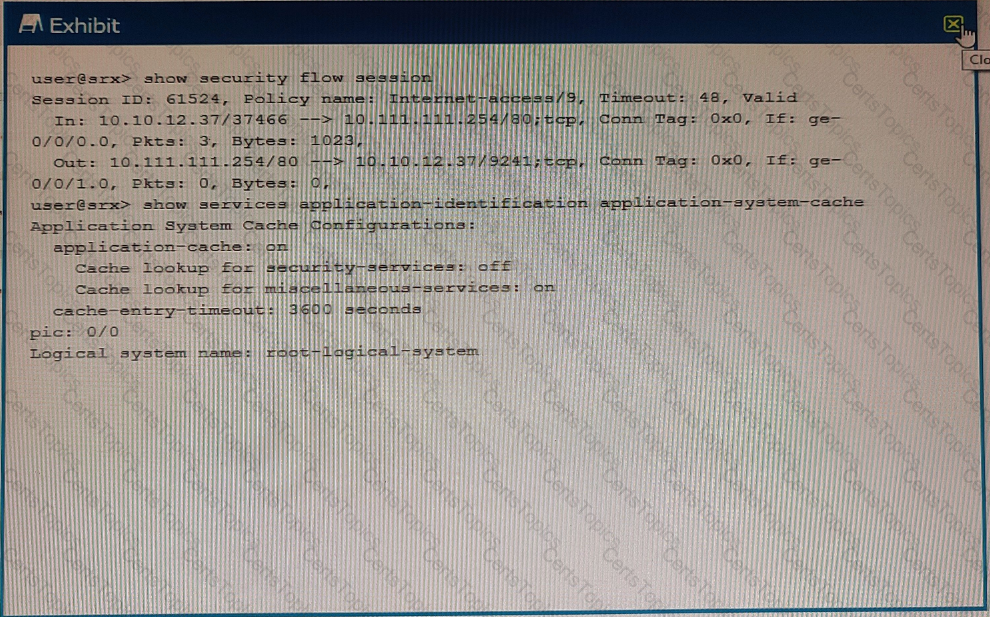
Referring to the exhibit which statement is true?
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
Which two statements are correct about the cSRX? (Choose two.)
While working on an SRX firewall, you execute the show security policies policy-name
Which function does this command accomplish?
You want to set up JSA to collect network traffic flows from network devices on your network.
Which two statements are correct when performing this task? (Choose two.)
Which two devices would you use for DDoS protection with Policy Enforcer? (Choose two.)
Which statement about security policy schedulers is correct?
Click the Exhibit button.
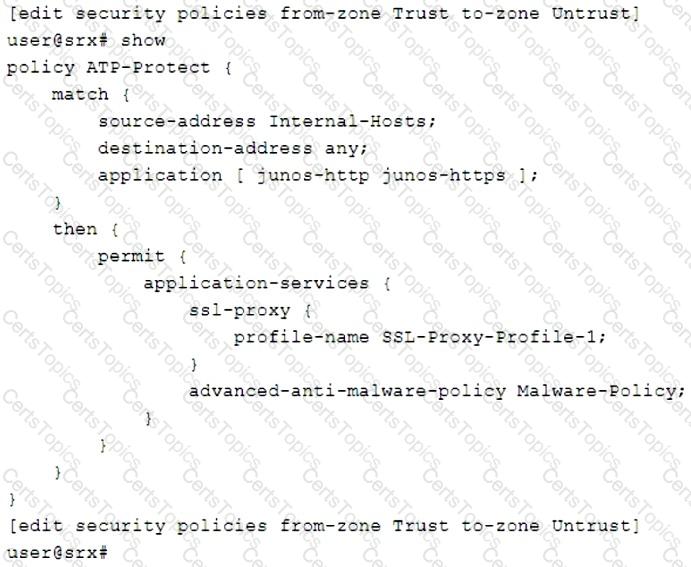
You are asked to create a security policy that will automatically add infected hosts to the infected hosts feed and block further communication through the SRX Series device.
What needs to be added to this configuration to complete this task?
Exhibit
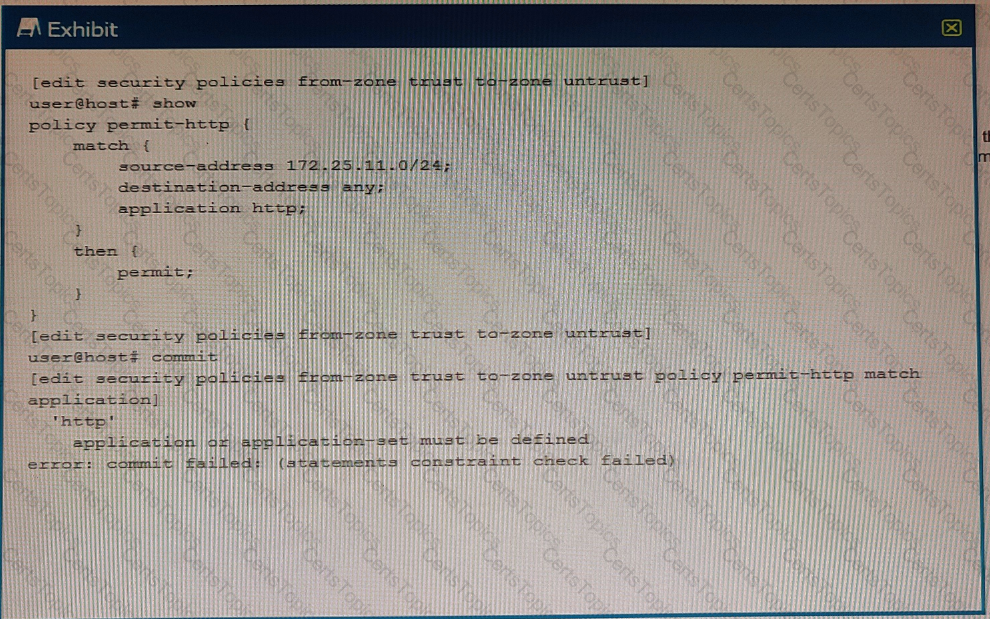
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two statements about unified security policies are correct? (Choose two.)