Which method does the loT Security feature use to identify traffic sourced from IoT devices?
Exhibit
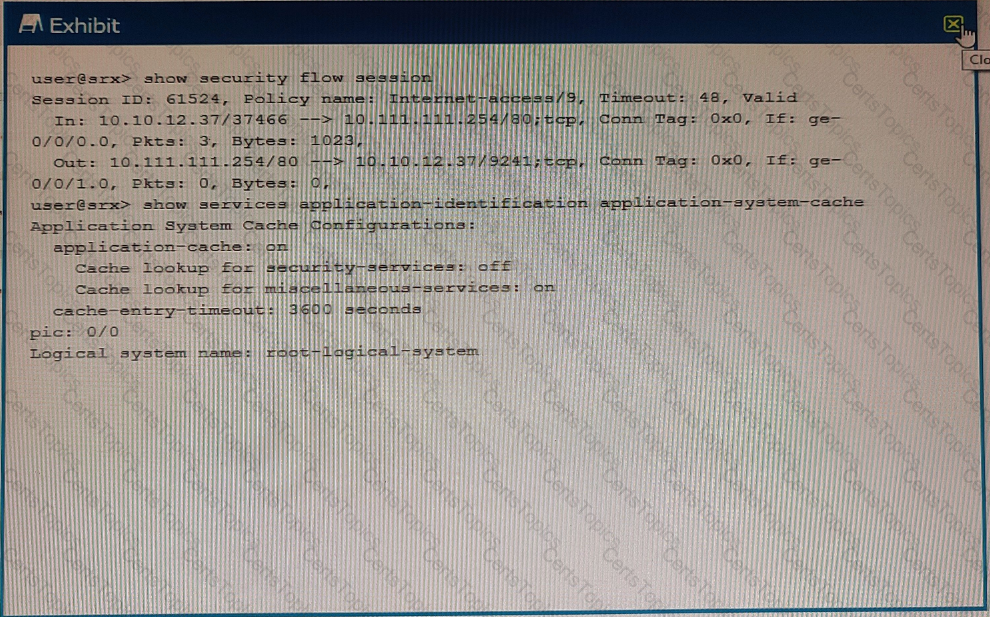
Referring to the exhibit which statement is true?
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)