Juniper Related Exams
JN0-335 Exam







A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Exhibit
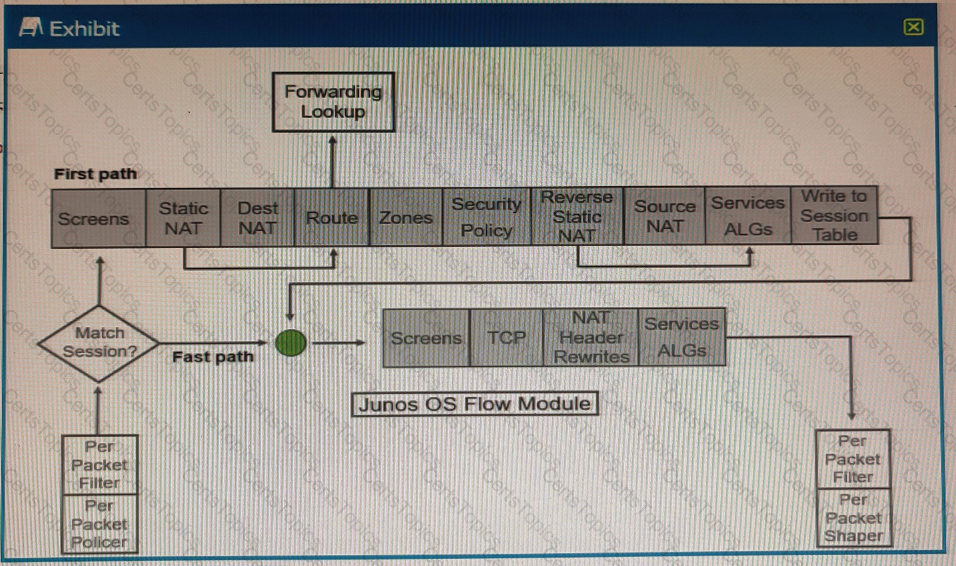
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?