Refer to the scenario.
# Introduction to the customer
You are helping a company add Aruba ClearPass to their network, which uses Aruba network infrastructure devices.
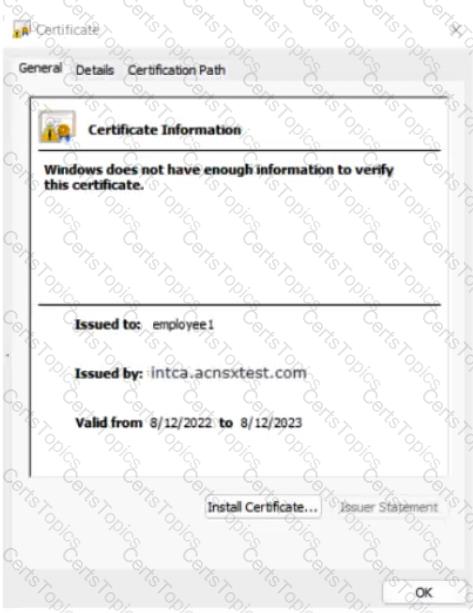
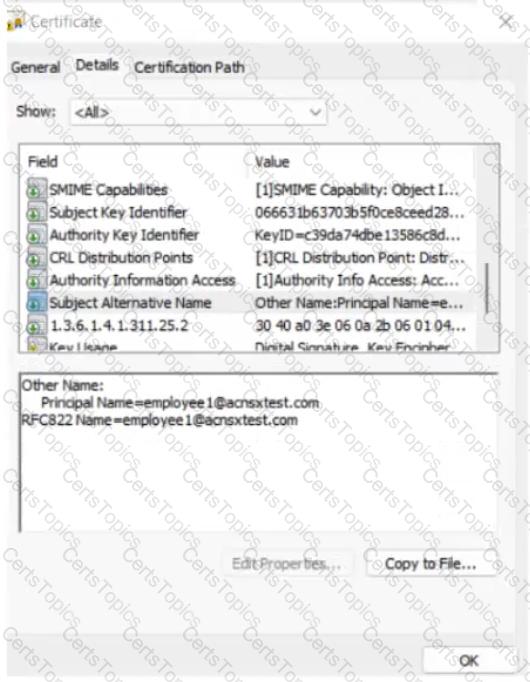
The company currently has a Windows domain and Windows CA. The Window CA issues certificates to domain computers, domain users, and servers such as domain controllers. An example of a certificate issued by the Windows CA is shown here.
The company is in the process of adding Microsoft Endpoint Manager (Intune) to manage its mobile clients. The customer is maintaining the on-prem AD for now and uses Azure AD Connect to sync with Azure AD.
# Requirements for issuing certificates to mobile clients
The company wants to use ClearPass Onboard to deploy certificates automatically to mobile clients enrolled in Intune. During this process, Onboard should communicate with Azure AD to validate the clients. High availability should also be provided for this scenario; in other words, clients should be able to get certificates from Subscriber 2 if Subscriber 1 is down.
The Intune admins intend to create certificate profiles that include a UPN SAN with the UPN of the user who enrolled the device.
# Requirements for authenticating clients
The customer requires all types of clients to connect and authenticate on the same corporate SSID.
The company wants CPPM to use these authentication methods:
 EAP-TLS to authenticate users on mobile clients registered in Intune
EAP-TLS to authenticate users on mobile clients registered in Intune
 TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
To succeed, EAP-TLS (standalone or as a TEAP method) clients must meet these requirements:
 Their certificate is valid and is not revoked, as validated by OCSP
Their certificate is valid and is not revoked, as validated by OCSP
 The client’s username matches an account in AD
The client’s username matches an account in AD
# Requirements for assigning clients to roles
After authentication, the customer wants the CPPM to assign clients to ClearPass roles based on the following rules:
 Clients with certificates issued by Onboard are assigned the “mobile-onboarded” role
Clients with certificates issued by Onboard are assigned the “mobile-onboarded” role
 Clients that have passed TEAP Method 1 are assigned the “domain-computer” role
Clients that have passed TEAP Method 1 are assigned the “domain-computer” role
 Clients in the AD group “Medical” are assigned the “medical-staff” role
Clients in the AD group “Medical” are assigned the “medical-staff” role
 Clients in the AD group “Reception” are assigned to the “reception-staff” role
Clients in the AD group “Reception” are assigned to the “reception-staff” role
The customer requires CPPM to assign authenticated clients to AOS firewall roles as follows:
 Assign medical staff on mobile-onboarded clients to the “medical-mobile” firewall role
Assign medical staff on mobile-onboarded clients to the “medical-mobile” firewall role
 Assign other mobile-onboarded clients to the “mobile-other” firewall role
Assign other mobile-onboarded clients to the “mobile-other” firewall role
 Assign medical staff on domain computers to the “medical-domain” firewall role
Assign medical staff on domain computers to the “medical-domain” firewall role
 All reception staff on domain computers to the “reception-domain” firewall role
All reception staff on domain computers to the “reception-domain” firewall role
 All domain computers with no valid user logged in to the “computer-only” firewall role
All domain computers with no valid user logged in to the “computer-only” firewall role
 Deny other clients access
Deny other clients access
# Other requirements
Communications between ClearPass servers and on-prem AD domain controllers must be encrypted.
# Network topology
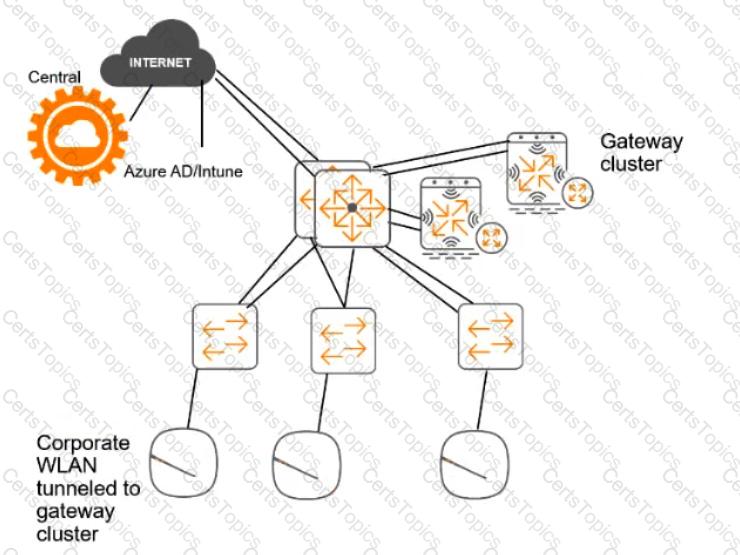
For the network infrastructure, this customer has Aruba APs and Aruba gateways, which are managed by Central. APs use tunneled WLANs, which tunnel traffic to the gateway cluster. The customer also has AOS-CX switches that are not managed by Central at this point.
# ClearPass cluster IP addressing and hostnames
A customer’s ClearPass cluster has these IP addresses:
 Publisher = 10.47.47.5
Publisher = 10.47.47.5
 Subscriber 1 = 10.47.47.6
Subscriber 1 = 10.47.47.6
 Subscriber 2 = 10.47.47.7
Subscriber 2 = 10.47.47.7
 Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
The customer’s DNS server has these entries
 cp.acnsxtest.com = 10.47.47.5
cp.acnsxtest.com = 10.47.47.5
 cps1.acnsxtest.com = 10.47.47.6
cps1.acnsxtest.com = 10.47.47.6
 cps2.acnsxtest.com = 10.47.47.7
cps2.acnsxtest.com = 10.47.47.7
 radius.acnsxtest.com = 10.47.47.8
radius.acnsxtest.com = 10.47.47.8
 onboard.acnsxtest.com = 10.47.47.8
onboard.acnsxtest.com = 10.47.47.8
You cannot see flow attributes for wireless clients.
What should you check?





 EAP-TLS to authenticate users on mobile clients registered in Intune
EAP-TLS to authenticate users on mobile clients registered in Intune TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them Their certificate is valid and is not revoked, as validated by OCSP
Their certificate is valid and is not revoked, as validated by OCSP The client’s username matches an account in AD
The client’s username matches an account in AD Clients with certificates issued by Onboard are assigned the “mobile-onboarded” role
Clients with certificates issued by Onboard are assigned the “mobile-onboarded” role Clients that have passed TEAP Method 1 are assigned the “domain-computer” role
Clients that have passed TEAP Method 1 are assigned the “domain-computer” role Clients in the AD group “Medical” are assigned the “medical-staff” role
Clients in the AD group “Medical” are assigned the “medical-staff” role Clients in the AD group “Reception” are assigned to the “reception-staff” role
Clients in the AD group “Reception” are assigned to the “reception-staff” role Assign medical staff on mobile-onboarded clients to the “medical-mobile” firewall role
Assign medical staff on mobile-onboarded clients to the “medical-mobile” firewall role Assign other mobile-onboarded clients to the “mobile-other” firewall role
Assign other mobile-onboarded clients to the “mobile-other” firewall role Assign medical staff on domain computers to the “medical-domain” firewall role
Assign medical staff on domain computers to the “medical-domain” firewall role All reception staff on domain computers to the “reception-domain” firewall role
All reception staff on domain computers to the “reception-domain” firewall role All domain computers with no valid user logged in to the “computer-only” firewall role
All domain computers with no valid user logged in to the “computer-only” firewall role Deny other clients access
Deny other clients access
 Publisher = 10.47.47.5
Publisher = 10.47.47.5 Subscriber 1 = 10.47.47.6
Subscriber 1 = 10.47.47.6 Subscriber 2 = 10.47.47.7
Subscriber 2 = 10.47.47.7 Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8 cp.acnsxtest.com = 10.47.47.5
cp.acnsxtest.com = 10.47.47.5 cps1.acnsxtest.com = 10.47.47.6
cps1.acnsxtest.com = 10.47.47.6 cps2.acnsxtest.com = 10.47.47.7
cps2.acnsxtest.com = 10.47.47.7 radius.acnsxtest.com = 10.47.47.8
radius.acnsxtest.com = 10.47.47.8 onboard.acnsxtest.com = 10.47.47.8
onboard.acnsxtest.com = 10.47.47.8