HP Related Exams
HPE6-A84 Exam







How does Aruba Central handle security for site-to-site connections between AOS 10 gateways?
Refer to the scenario.
A customer is using an AOS 10 architecture with Aruba APs and Aruba gateways (two per site). Admins have implemented auto-site clustering for gateways with the default gateway mode disabled. WLANs use tunneled mode to the gateways.
The WLAN security is WPA3-Enterprise with authentication to an Aruba ClearPass Policy Manager (CPPM) cluster VIP. RADIUS communications use RADIUS, not RadSec.
CPPM is using the service shown in the exhibits.
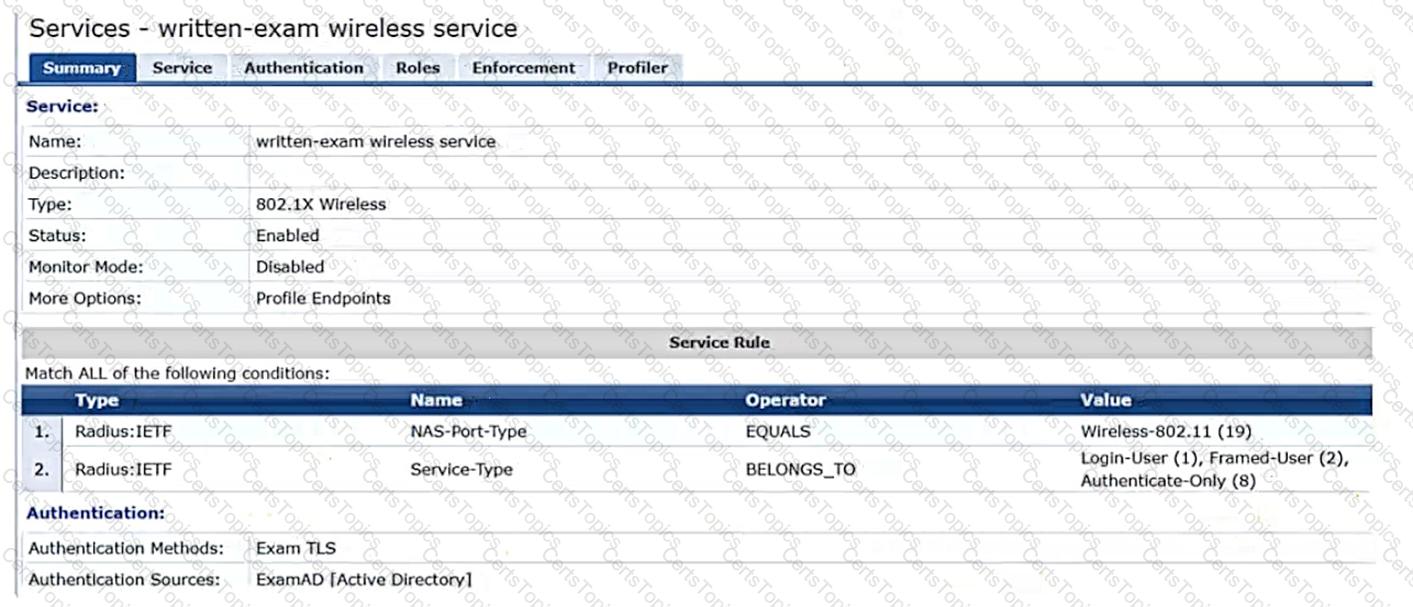
Which step can you take to improve operations during a possible gateway failover event?
A company has Aruba gateways that are Implementing gateway IDS/IPS in IDS mode. The customer complains that admins are receiving too frequent of repeat email notifications for the same threat. The threat itself might be one that the admins should investigate, but the customer does not want the email notification to repeat as often.
Which setting should you adjust in Aruba Central?